WatchAD – AD Security Intrusion Detection System
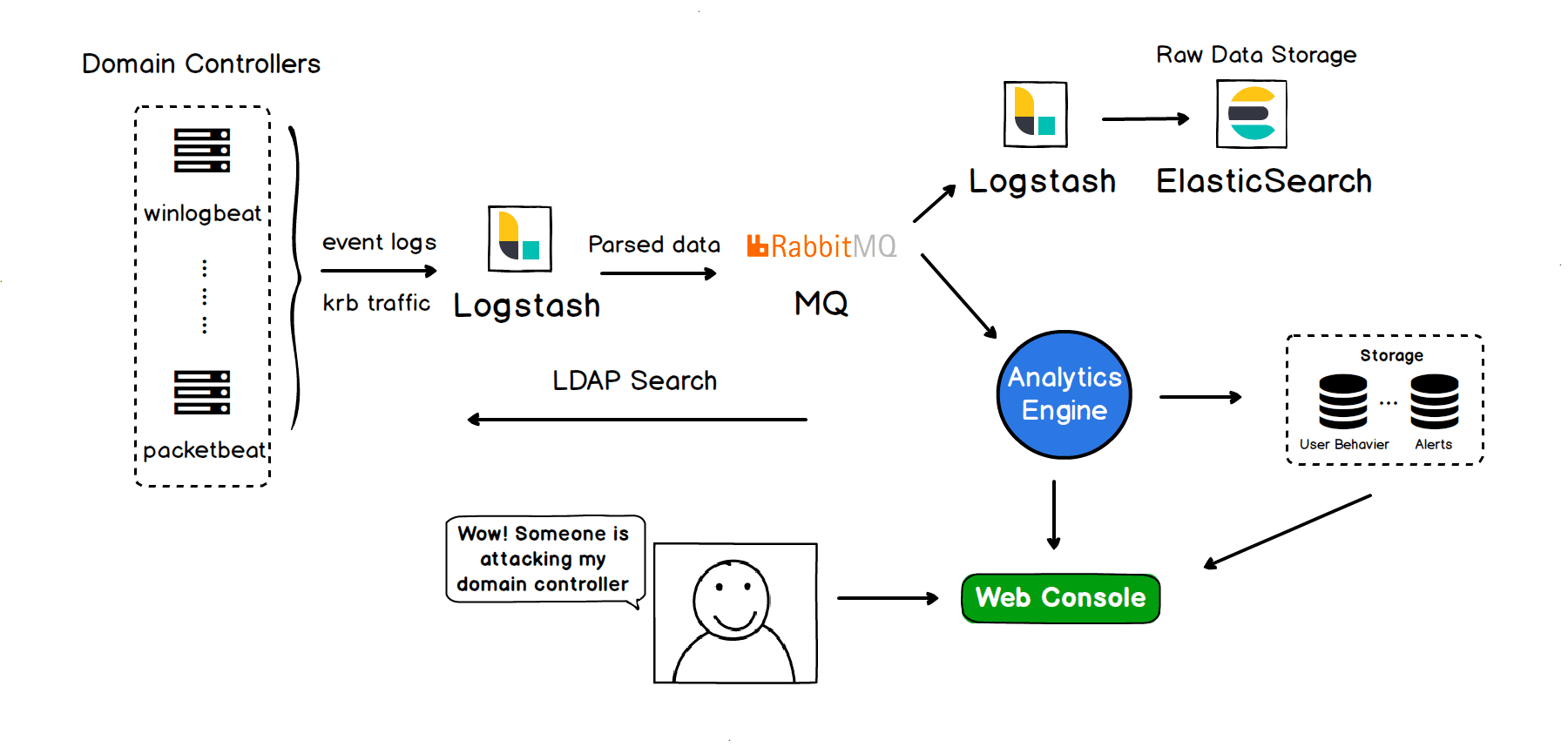
After Collecting event logs and Kerberos traffic on all domain controls, WatchAD can detect a variety of known or unknown threats through features matching, Kerberos protocol analysis, historical behaviors, sensitive operations, honeypot accounts and so on. The WatchAD rules cover the many common AD attacks.
The WatchAD has been running well on the Qihoo 360 intranet for more than six months and has found several threat activities.
In order to support the open-source community and promote the improvement of the project, we decided to open-source part of the system based on the event log detections.
The following are currently supported detections:
- Discovery: Reconnaissance using Directory Services queries, Reconnaissance using PsLoggedOn, Honeypot accounts Activity.
- Credential Dumping: Kerberoasting [NT], AS-REP Roasting, Remotely dump the password of DC.
- Lateral Movement: Brute Force, Suspicious remotely logon using credentials, Remote execution targeting to DC、Abnormal windows file share name, Encryption downgrade activity [NT], Abnormal Kerberos ticket request [NT].
- Privilege Escalation: Abnormal modification of ACL, Detection of MS17-010 attacks, Creation of new Group Policy, NTLM Relay Activity, Sensitive permission of resource-based constraint delegation granted, Attacking printer services with SpoolSample, Privilege escalation with MS14-068 Attacks [NT], Suspicious Kerberos Constraint Delegation activity [NT]
- Persistence: Modification of AdminSDHolder, DCShadow Attack Detection, Modification of the DSRM password, Sensitive permission of Group Policy delegation granted, Sensitive permission of Kerberos constraint delegated granted, Modification of sensitive groups, Creation of new System Service on DC, Creation of new Scheduled Task on DC, Modification of SIDHistory, Skeleton Key active detection, Skeleton Key passive detection [NT], Kerberos Golden Ticket Activity [NT].
- Defense Evasion: Malicious clearance of event logs, Event log service shut down
[NT] represent “based on Network traffic”. Up to now, these part is not in this open-source plan. We will continue to open source based on the feedback.
Architecture:
This project WatchAD only contains part of the code, which associated with the detection engine. In order to format the display, you can put alarm data into your platform, or use the Web platform we developed — WatchAD-Web, which is a simple platform tailored to WatchAD for some common operations. If you have more needs for interface design or operation experience, please customize the development according to WatchAD’s alarm data.
Install & Use