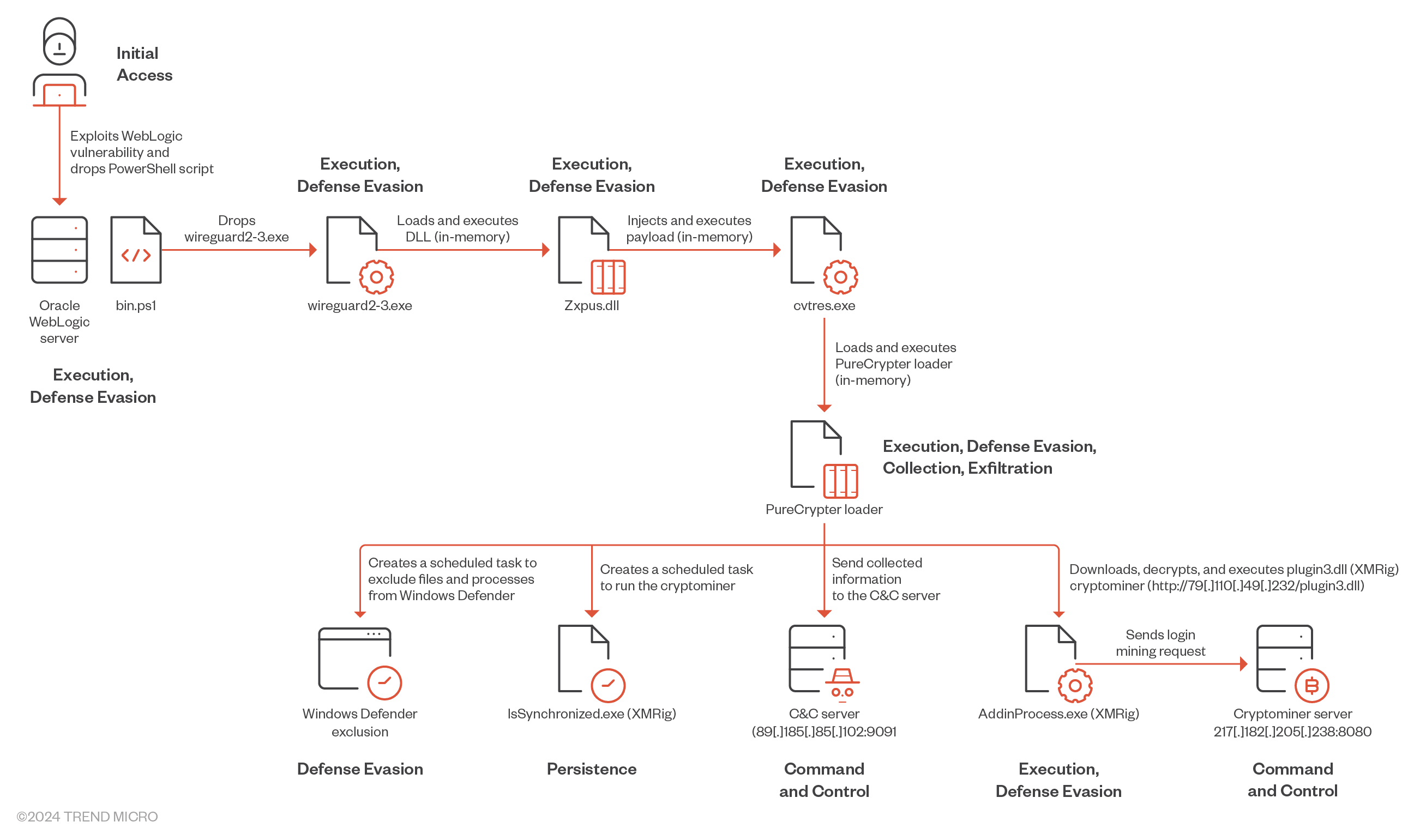
Water Sigbin Attack diagram
Security researchers at Trend Micro have uncovered a sophisticated campaign by the Water Sigbin threat actor, also known as the 8220 Gang, targeting Oracle WebLogic servers to deploy XMRig cryptocurrency miners. This group, primarily focused on crypto-mining malware, has been found exploiting vulnerabilities in Oracle WebLogic Server, such as CVE-2017-3506 and CVE-2023-21839, to initiate multi-stage attacks.
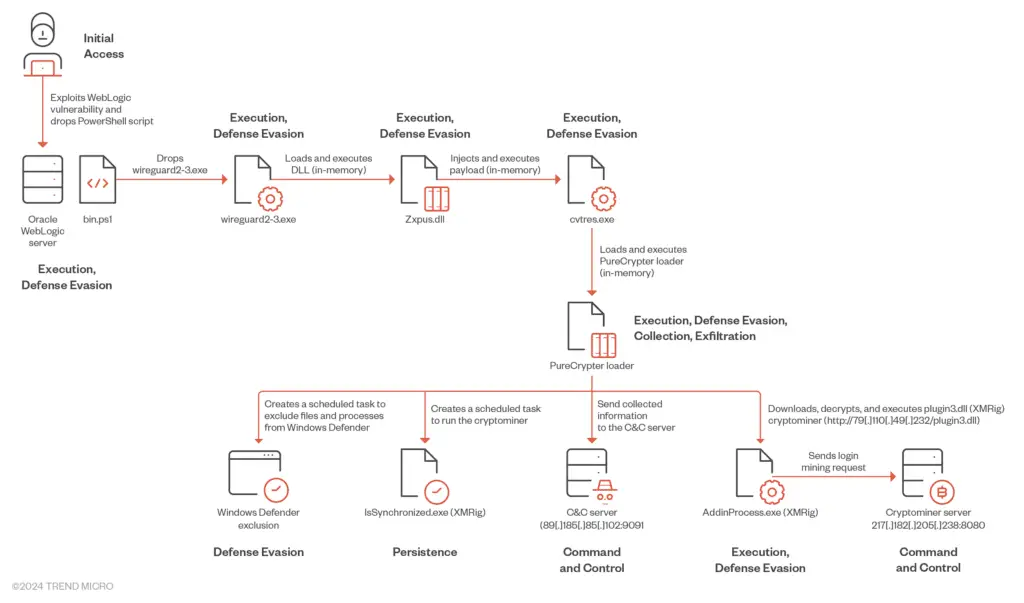
The researchers uncovered a multi-stage attack chain, where Water Sigbin cleverly obfuscates its malware using .NET Reactor, a code protection software designed to hinder reverse engineering efforts. The initial stage involves exploiting vulnerabilities in Oracle WebLogic Server to deploy a PowerShell script, which then decodes and executes a first-stage loader. This loader, disguised as a legitimate WireGuard VPN application, further decrypts and loads a second-stage payload into memory.
The attack progresses with reflective DLL injection, a fileless execution technique that allows the malware to operate entirely in memory, evading traditional disk-based detection mechanisms. The second-stage loader then retrieves and decrypts another payload, ultimately leading to the execution of the PureCrypter loader V6.0.7D. This sophisticated loader serves as the final step in the infection chain, establishing communication with the attacker’s command-and-control server and downloading the XMRig cryptocurrency miner.
XMRig, an open-source miner, is then unleashed on the compromised system, utilizing its computational resources to generate Monero cryptocurrency for the threat actors. To maintain persistence, Water Sigbin employs various techniques, including creating scheduled tasks, adding exclusions to Windows Defender, and replicating itself under hidden directories.
The Trend Micro analysis also revealed that the malware collects system information, including usernames, antivirus software, and CPU details, which is then exfiltrated to the attackers’ server. This information could be used for further malicious activities or sold on underground markets.
Organizations can protect their systems and networks from such sophisticated attacks by implementing the following best practices:
- Regular Updates and Patching: Keep operating systems, applications, and firmware up to date with the latest security patches to mitigate vulnerabilities.
- Robust Access Controls: Ensure that users and applications have the minimum level of access necessary for their tasks. Implement strong authentication methods, such as multi-factor authentication (MFA).
- Regular Security Assessments: Conduct frequent scans for vulnerabilities and perform thorough security assessments to identify and address potential threats.
- Security Awareness Training: Educate employees continuously on security best practices and the latest threat vectors.