Web Cache Vulnerability Scanner v1.2 releases: CLI tool for testing for web cache poisoning
Web Cache Vulnerability Scanner
Web Cache Vulnerability Scanner (WCVS) is a fast and versatile CLI scanner for web cache poisoning developed by Hackmanit.
The scanner supports many different web cache poisoning techniques, includes a crawler to identify further URLs to test, and can adapt to a specific web cache for more efficient testing. It is highly customizable and can be easily integrated into existing CI/CD pipelines.
Features
- Support for 9 web cache poisoning techniques:
- Unkeyed header poisoning
- Unkeyed parameter poisoning
- Parameter cloaking
- Fat GET
- HTTP response splitting
- HTTP request smuggling
- HTTP header oversize (HHO)
- HTTP meta character (HMC)
- HTTP method override (HMO)
- Analyzing a web cache before testing and adapting to it for more efficient testing
- Generating a report in JSON format
- Crawling websites for further URLs to scan
- Routing traffic through a proxy (e.g., Burp Suite)
- Limiting requests per second to bypass rate limiting
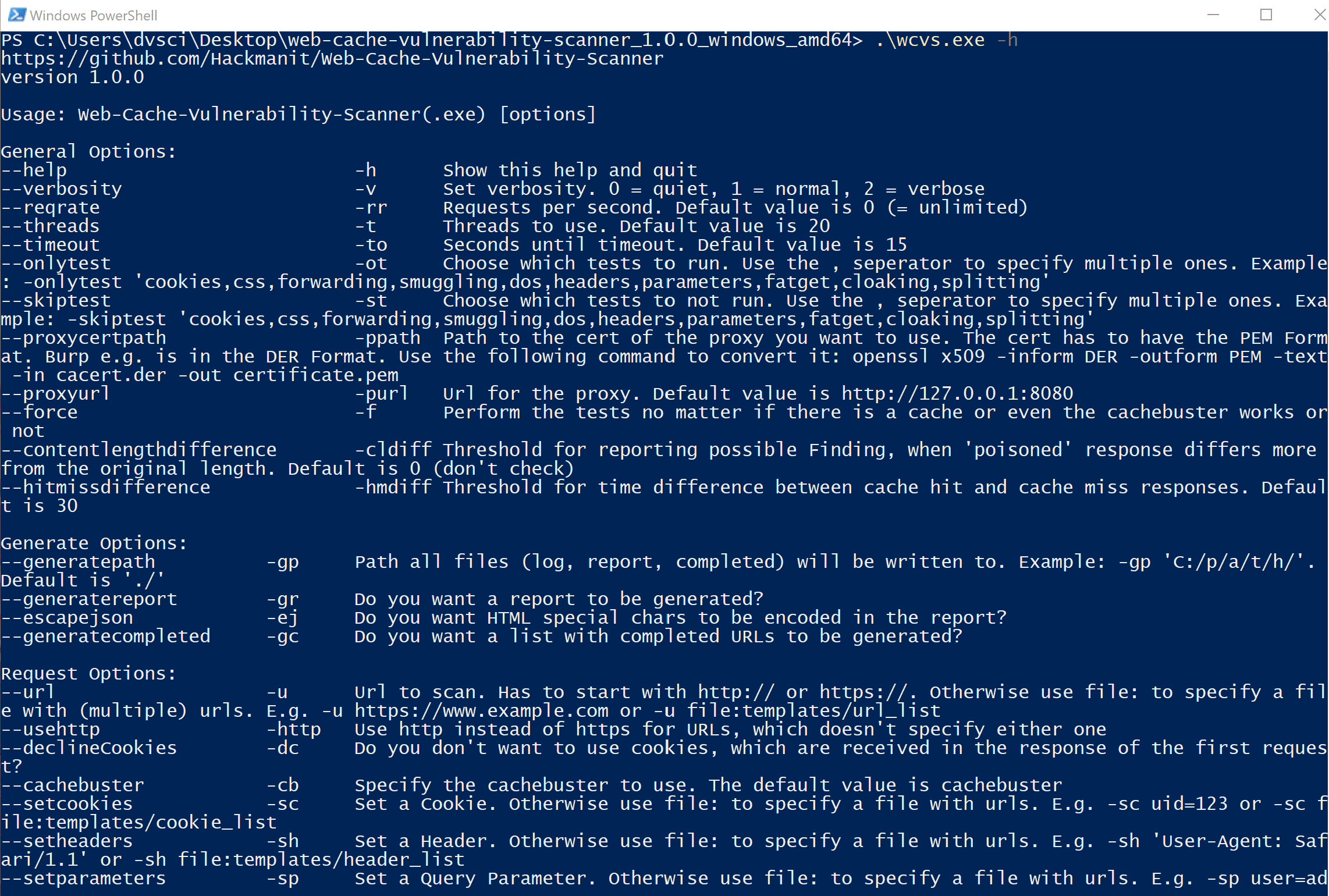
Usage

WCVS is highly customizable using its flags. Many of the flags can either contain a value directly or the path to a file.
The only mandatory flag is -u/–url to provide the target URL which should be tested for web cache poisoning. The target URL can be provided in different formats,
WCVS needs two wordlists in order to test for the first 5 techniques – one wordlist with header names and one with parameter names. The wordlists can either be present in the same directory WCVS is executed from or specified using the –headerwordlist/-hw and –parameterwordlist/-pw flags.
Changelog v1.2
The WCVS now detects Web Cache Deception. It uses various techniques for this purpose:
- Path Parameter
- Path Traversal
- Appended Newline, Null Byte, Semicolon, Pound, Question Mark or Ampersand
In summary, WCVS’s procedure is as follows:
If the cache returns a HIT, it is tested for web cache poisoning. If the cache always returns a MISS, it is tested for web cache deception.
Changelog
- Added Web Cache Deception Detection d773d4b 8a52b8b accdb13
- Added support for more common cache headers (from GoogleCloud, RackCache, Akamai & more) c6789a6
- Added Web Cache Deception & Bachelor’s Thesis to the Readme 3c237c0 127125e
Download & Tutorial
Copyright (C) 2022 Hackmanit





