Crypto-phishing collecting secret recovery phrase | Image: Netskope
New research from Netskope Threat Labs reveals a surge in phishing attacks targeting cryptocurrency wallets, employing a novel tactic that leverages Webflow, a popular website builder.
The report, authored by Threat Research Engineer Jan Michael Alcantara, highlights a 10-fold increase in traffic to phishing pages crafted through Webflow between April and September 2024. These attacks target sensitive information from various crypto wallets, including Coinbase, MetaMask, Phantom, Trezor, and Bitbuy, as well as login credentials for company webmail platforms and Microsoft 365.
The campaigns primarily target organizations across North America and Asia, with financial services, banking, and technology being the hardest-hit sectors. More than 120 organizations have already been impacted by this phishing scheme. Alcantara’s report reveals that the phishing pages mimic legitimate crypto wallet sites by using full-page screenshots of actual wallet homepages. The entire webpage is often converted into a clickable image that redirects victims to malicious sites, collecting valuable information like secret recovery phrases.
One of the standout aspects of this campaign is how attackers can build phishing sites without writing any code. Alcantara explains, “Some of the phishing websites we investigated were more creative. They combined imagery from their target with Webflow’s form blocks. The form blocks allow the attacker to collect victims’ credentials directly in Webflow.” This is a stark departure from traditional phishing attacks, where attackers typically rely on custom scripts or embedded malicious code.
In some cases, these phishing sites use Webflow’s form blocks to capture the victim’s credentials, which are then forwarded to attacker-controlled websites. This use of Webflow provides attackers with stealth and convenience, as there are no obvious phishing lines of code to detect.
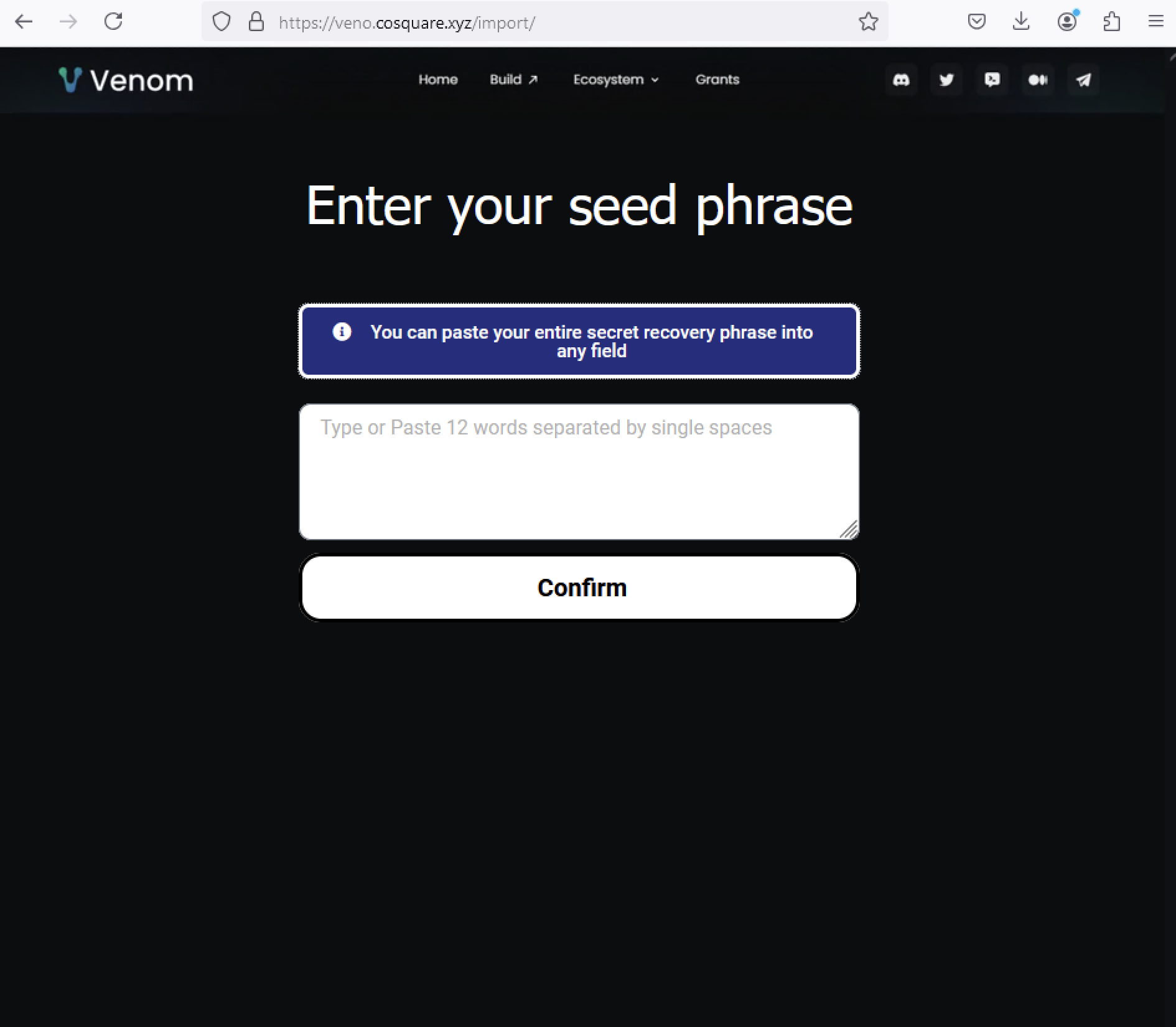
The primary target of these phishing pages is the victim’s secret recovery phrase—a critical component for accessing and controlling cryptocurrency wallets. The secret recovery phrase acts as a master key, allowing users to recover their accounts if passwords are forgotten or mobile devices are lost. By stealing this phrase, attackers gain complete control of the victim’s wallet and can drain it of all assets.
“The majority of Webflow crypto-phishing websites we investigated only targeted the victim’s secret recovery phrase,” Alcantara writes. Once the phrase is entered, victims are typically redirected to an error message, and in some cases, a fraudulent tech support chat option appears. Netskope found that these phishing campaigns often used the chat platform “tawk.to,” which has been previously linked to other crypto scams.