webscan: Browser-based network scanner & local-IP detection
webscan
webscan is a browser-based network IP scanner and local IP detector. It detects IPs bound to the user/victim by listening on an RTP data channel via WebRTC and looping back to the port across any live IPs, as well as discovering all live IP addresses on valid subnets by monitoring for immediate timeouts (TCP RST packets returned) from fetch() calls or hidden img tags pointed to valid subnets/IPs. Works on mobile and desktop across all major browsers and OS’s. The Beta version is extensible to allow the addition of multiple techniques.
webscan takes advantage of the fact that non-responsive img tag sockets can be closed to prevent browser & network-based rate-limiting by altering the src attribute to a non-socket URI (removing from DOM ironically does not close the socket), or by using fetch()’s signal support of the AbortController() interface.
webscan works like so
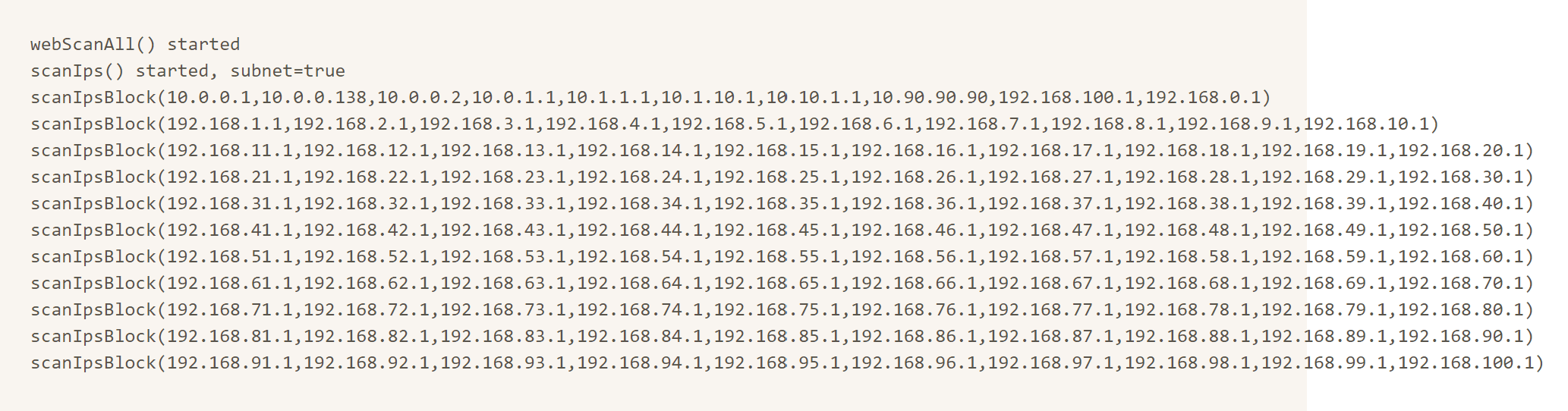
- webscan first iterates through a list of common gateway IP addresses
- for each IP, use fetch() to make a fake HTTP connection to http://common.gateway.ip:1337
- if a TCP RST returns, the fetch() promise will be rejected, or img tag onerror will trigger before a timeout, indicating a live IP
- to prevent browser or network rate limiting, non-responsive fetch() sockets are closed via AbortController() signal while img-tags have the src redirected to non-socket URI, closing the socket
- when live gateway detected, step 1-3 reran for every IP on the subnet (e.g. 192.168.0.[1-255])
- a WebRTC data channel is opened on the browser, opening a random port on the victim machine
- for any IPs that are found alive on the subnet, a WebRTC data channel connection is made to that host
- if the WebRTC data channel is successful, we know we just established a connection to our own local IP