whonow: A “malicious” DNS server for executing DNS Rebinding attacks
Whonow DNS Server
A malicious DNS server for executing DNS Rebinding attacks on the fly. whonow lets you specify DNS responses and rebind rules dynamically using domain requests themselves.
What’s great about dynamic DNS Rebinding rules is that you don’t have to spin up your own malicious DNS server to start exploiting the browser’s Same-origin policy. Instead, everyone can share the same public whonow server running on port 53 of rebind.network.
Note: You should include UUIDs (e.g. a06a5856-1fff-4415-9aa2-823230b05826) as a subdomain in each DNS lookup to a whonow server. These have been omitted from examples in this README for brevity, but assume requests to *.rebind.network should be *.a06a5856-1fff-4415-9aa2-823230b05826.rebind.network. See the Gotchas section for more info as to why.
Subdomains = Rebind Rules
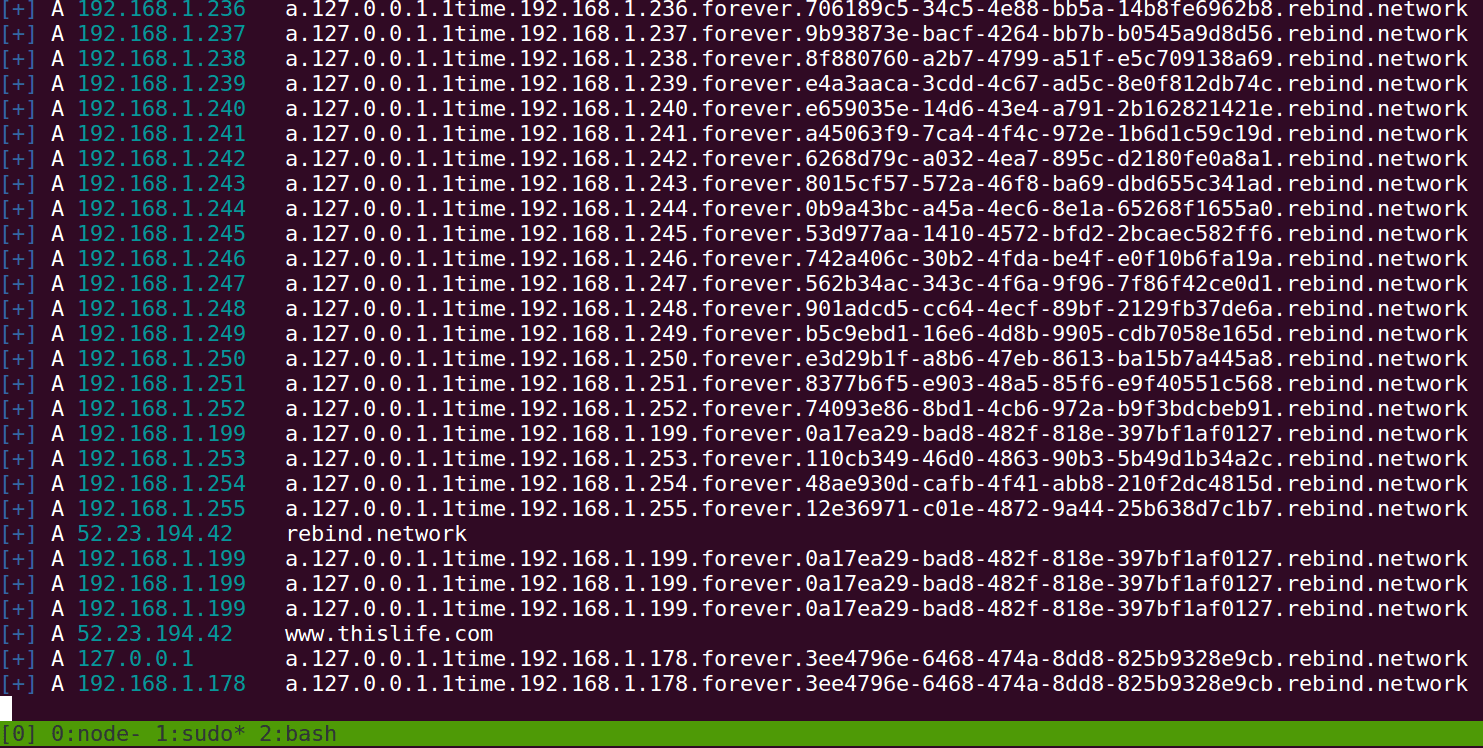
The beauty of whonow is that you can define the behavior of DNS responses via subdomains in the domain name itself. Using only a few simple keywords: A, (n)times, forever, and repeat, you can define complex and powerful DNS behavior.
Anatomy of a whonow request
A: The type of DNS request. Currently onlyArecords are supported, butAAAAshould be coming soon.<ip-address>: an ipv4 (ipv6 coming soon) address with each octet seprated by a period (e.g.192.168.1.1.<rule>: One of three rules(n)time[s]: The number of times the DNS server should reply with the previous IP address. Accepts both plural and singular strings (e.g.1time, 3times, 5000times)forever: Respond with the previous IP address forever.repeat: Repeat the entire set of rules starting from the beginning.
[uuid/random-string]: A random string to keep DNS Rebind attacks against the same IP addresses separate from each other. See Gotchas for more info.example.com: A domain name you have pointing to awhonownameserver, like the publicly availablerebind.network:53whonowinstance.
Download
git clone https://github.com/brannondorsey/whonow.git
Usage

Copyright (c) 2018 Brannon Dorsey <brannon@brannondorsey.com>





