wifiphisher v1.4 releases, Rogue Access Point framework
Wifiphisher is a security tool that performs Wi-Fi automatic association attacks to force wireless clients to unknowingly connect to an attacker-controlled Access Point. It is a rogue Access Point framework that can be used to mount automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the victims with malware. It can work a social engineering attack tool that unlike other methods it does not include any brute forcing. It is an easy way for obtaining credentials from captive portals and third-party login pages (e.g. in social networks) or WPA/WPA2 pre-shared keys.
Wifiphisher works on Kali Linux and is licensed under the GPL license.
How it works
After achieving a man-in-the-middle position using Wi-Fi automatic association techniques (including “KARMA” and “Known Beacons” attacks), Wifiphisher by default redirects all HTTP requests to an attacker-controlled phishing page.
From the victim’s perspective, the attack makes use in three phases:
- The victim is being deauthenticated from her access point. Wifiphisher continuously jams all of the target access point’s wifi devices within range by forging “Deauthenticate” or “Disassociate” packets to disrupt existing associations.
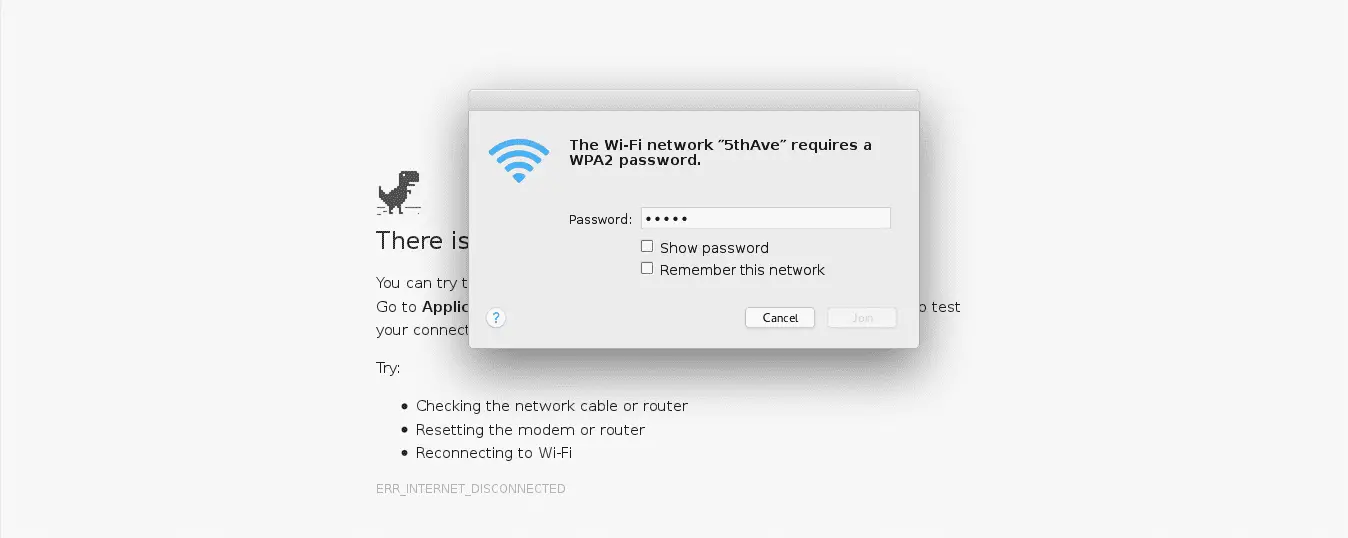
- Victim joins a rogue access point. Wifiphisher sniffs the area and copies the target access point’s settings. It then creates a rogue wireless access point that is modeled by the target. It also sets up a NAT/DHCP server and forwards the right ports. Consequently, because of the deauth attack and the automatic association techniques, clients will eventually start connecting to the rogue access point. After this phase, the victim is MiTMed.
- The victim is being served a realistic specially-customized phishing page. Wifiphisher employs a minimal web server that responds to HTTP & HTTPS requests. As soon as the victim requests a page from the Internet, wifiphisher will respond with a realistic fake page that asks for credentials or serves malware. This page will be specifically crafted for the victim. For example, a router config-looking page will contain the brand of the victim’s vendor. The tool supports community-built templates for different phishing scenarios.
Changelog v1.4
- Added dissociation frame to DEAUTH attack [@anakin1028]
- RSSI output fix [@anakin1028]
- Code quality fixes. [@blackHatMonkey]
- Introduced MAC address randomization [@anakin1028]
- Refactoring of interface management module [@blackHatMonkey]
- Introduced tox. [@blackHatMonkey]
- Added support for providing Internet to victim users via a wireless interface [@anakin1028]
- Tool now kills any interfering processes on startup [@anakin1028]
- Use curses everywhere for TUI [@anakin1028]
- Show the encryption type during AP discovery. [@sophron]
- Introduced Wifiphisher Extensions [@sophron]
- Introduced roguehostapd, a patched version of hostapd. [@anakin1028]
- Introduced WPA/WPA2 captured passphrase validation. [@anakin1028]
- Added WPS info during AP discovery. [@anakin1028]
- Added the option to perform DEAUTH attack based on ESSID [@anakin1028]
- Added operation moded [@sophron]
- Increased performance of modules [@blackHatMonkey]
- Made the tool run with only one physical interface [@anakin1028]
- Introduced –logging option [@blackHatMonkey]
- Introduced channel monitoring to check if target AP switches channel [@anakin1028]
- Introduced Known Beacons attack [@sophron]
- Introduced WPS PBC phishing attack [@anakin1028]
Requirements
Following are the requirements for getting the most out of Wifiphisher:
- Kali Linux. Although people have made Wifiphisher work on other distros, Kali Linux is the officially supported distribution, thus all new features are primarily tested on this platform.
- One wireless network adapter that supports AP & Monitor mode and is capable of injection. For advanced mode, you need two cards; one that supports AP mode and another that supports Monitor mode. Drivers should support netlink.
Installation
To install the latest development version type the following commands:
Usage
python bin/wifiphisher

Disclaimer
- Usage of Wifiphisher for attacking infrastructures without prior mutual consistency can be considered as an illegal activity. It is the final user’s responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.
wifiphisher Copyright (C) 2017 anakin1028
Source: https://github.com/wifiphisher/





