
A cloned GlobalProtect page that directs users to download spoofed GlobalProtect installers | Image: Unit 42
In a recent investigation, the Unit 42 Managed Threat Hunting (MTH) team uncovered a sophisticated cyber campaign leveraging a unique variant of the WikiLoader malware. The attackers behind this operation employed SEO poisoning to masquerade as Palo Alto Networks’ GlobalProtect, a trusted VPN solution, to deliver the malware.
WikiLoader, a versatile malware loader active since late 2022, has historically relied on phishing as its primary delivery method. However, in June 2024, Unit 42 observed a notable change in strategy. Instead of phishing, the attackers utilized SEO poisoning—a tactic where malicious websites are optimized to appear at the top of search engine results for legitimate software downloads. In this instance, the malicious site spoofed GlobalProtect, tricking users into downloading and executing the malware.
The implications of this shift are significant. While phishing campaigns are often targeted, SEO poisoning can potentially affect a much broader audience. By targeting popular search terms related to GlobalProtect, the attackers increased their chances of compromising users from diverse sectors. Unit 42’s analysis revealed that the U.S. higher education and transportation sectors were particularly affected, although the broad nature of SEO poisoning suggests that many others could also be at risk.
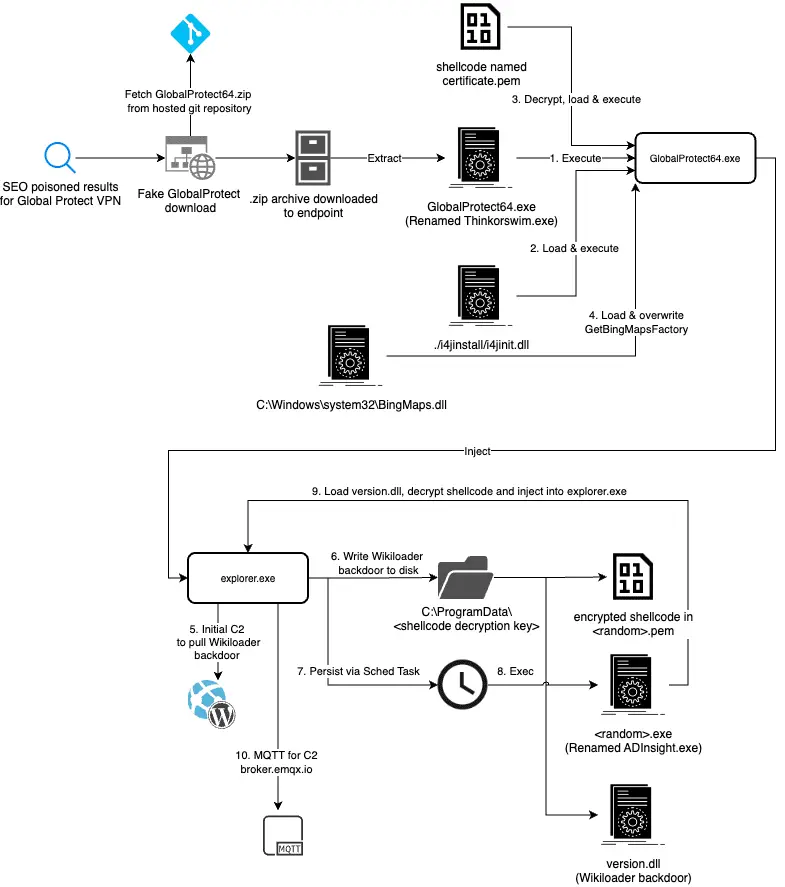
The campaign’s success is underpinned by several advanced evasion techniques designed to circumvent traditional detection mechanisms:
- Typosquatting and Cloned Websites: The attackers created websites that closely resembled legitimate GlobalProtect download pages. These sites were designed to deliver the WikiLoader malware under the guise of a legitimate VPN client.
- Use of MQTT Protocol for C2: The campaign leveraged the MQTT IoT event queue protocol for command and control (C2) communications. This approach allowed the attackers to blend their traffic with legitimate IoT communications, making detection more challenging.
- Signed Binaries and Sideloading: To further evade detection, the malware was delivered using legitimate, signed binaries. These binaries were then used to sideload the WikiLoader malware, effectively bypassing many security controls.
- Complex Encryption and Obfuscation: The malware’s shellcode was encrypted and stored separately from the main executable, making static analysis difficult. The decryption keys were stored on the C2 servers, further complicating analysis and detection.
The infection process begins innocuously enough: a user unknowingly downloads and launches a fake GlobalProtect installer, named GlobalProtect64.exe. This file triggers a series of actions designed to load the WikiLoader backdoor with minimal detection. Key stages include:
- Decryption and Execution: The malicious installer decrypts shellcode hidden within an encrypted
certificate.pemfile. This shellcode is then injected into theexplorer.exeprocess, establishing a foothold in the system. - Persistence Mechanisms: The malware establishes persistence by creating scheduled tasks and hiding its components in innocuously named files within the
ProgramDatadirectory. This ensures that the malware remains active even after system reboots. - Command and Control: The injected code reaches out to the C2 servers for further instructions, downloading additional payloads as needed. These payloads are decrypted and executed, allowing the attackers to maintain control over the compromised system.
The move from phishing to SEO poisoning in WikiLoader campaigns raises important questions. One theory suggests that another initial access broker (IAB) may have adopted WikiLoader and introduced SEO poisoning as a delivery method. Alternatively, the shift could reflect a response to improved phishing detection capabilities within organizations, forcing attackers to explore new avenues.
By spoofing trusted security software like GlobalProtect, attackers can bypass security measures that rely on file name-based allowlisting, increasing their chances of success.
Unit 42 has provided a set of queries that organizations can use to hunt for WikiLoader in their endpoint data. The researchers urge organizations to remain vigilant and to take proactive steps to protect themselves from this evolving threat.
Related Posts:
- Popular Text Editor Notepad++ Compromised in “WikiLoader” Malware Attack
- Fake Palo Alto Tool Delivers Sophisticated Malware in Middle East Cyberattack
- PAN-OS: PAN-OS Remote Code Execution Vulnerability
- WailingCrab Malware Evolves: Embracing MQTT for Stealthier C2 Communication
- Palo Alto Networks Issues Security Advisories, Urges Updates Amidst 34 Vulnerabilities