winafl: fuzzing tool for coverage-guided fuzzing
AFL is a popular fuzzing tool for coverage-guided fuzzing. The tool combines fast target execution with clever heuristics to find new execution paths in the target binary. It has been successfully used to find a large number of vulnerabilities in real products. For more info about the original project, please refer to the original documentation at:
http://lcamtuf.coredump.cx/afl/
Unfortunately, the original AFL does not work on Windows due to very *nix-specific design (e.g. instrumentation, forkserver etc). This project is a fork of AFL that uses different instrumentation approach which works on Windows even for black box binary fuzzing.
The WinAFL approach
Instead of instrumenting the code at compilation time, WinAFL relies on dynamic instrumentation using DynamoRIO (http://dynamorio.org/) to measure and extract target coverage. This approach has been found to introduce an overhead about 2x compared to the native execution speed, which is comparable to the original AFL in the binary instrumentation mode.
To improve the process startup time, WinAFL relies heavily on persistent fuzzing mode, that is, executing multiple input samples without restarting the target process. This is accomplished by selecting a target function (that the user wants to fuzz) and instrumenting it so that it runs in a loop.
WinAFL has been successfully used to identify bugs in Windows software, such as
- CVE-2016-7212 – found by Aral Yaman of Noser Engineering AG
- CVE-2017-0073, CVE-2017-0190, CVE-2017-11816 – found by Symeon Paraschoudis of SensePost
Building WinAFL
- Download and build DynamoRIO sources or download DynamoRIO Windows binary package from https://github.com/DynamoRIO/dynamorio/wiki/Downloads
- Open Visual Studio Command Prompt (or Visual Studio x64 Win64 Command Prompt if you want a 64-bit build). Note that you need a 64-bit winafl.dll build if you are fuzzing 64-bit targets and vice versa.
- Go to the directory containing the source: git clone https://github.com/ivanfratric/winafl.git
- Type the following commands. Modify the -DDynamoRIO_DIR flag to point to the location of your DynamoRIO cmake files (either full path or relative to the source directory).
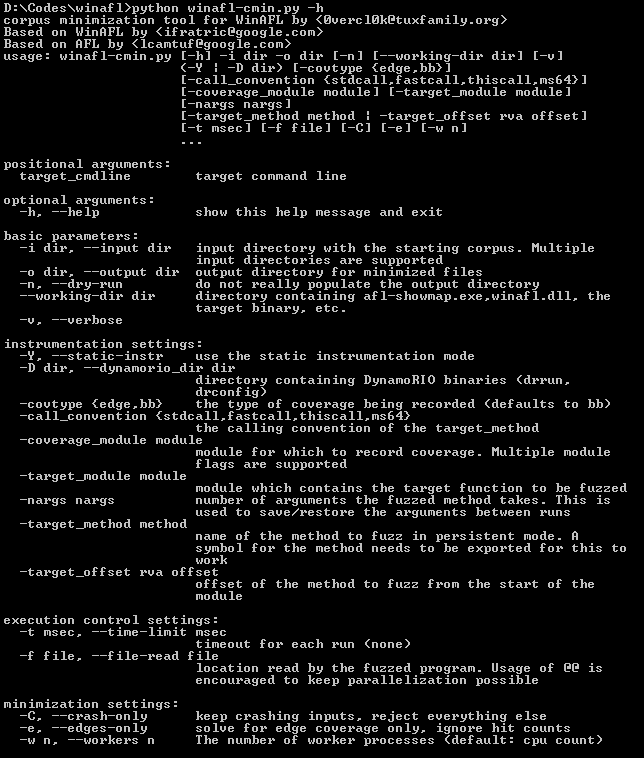
Usage
The command line for afl-fuzz on Windows is different than on Linux. Instead of:
%s [ afl options ] — target_cmd_line
it now looks like this:
afl-fuzz [afl options] — [instrumentation options] — target_cmd_line
The following afl-fuzz options are supported:
The following instrumentation options are used:
Original AFL code was written by Michal Zalewski <lcamtuf@google.com>
Windows fork wrote and maintained by Ivan Fratric <ifratric@google.com>
Copyright 2016 Google Inc. All Rights Reserved.
Source: https://github.com/ivanfratric/






