Image: Tonmoy Jitu
Security researchers have exposed a new aspect in the Living Off the Land Binaries and Scripts (LOLBAS) arsenal: the little-known potential of Windows’ wevtutil.exe for stealthy, malicious operations. Tonmoy Jitu’s in-depth analysis sheds light on how this legitimate utility, designed for event log management, can become a dangerous tool in an attacker’s hands.
Wevtutil.exe is a command-line tool bundled with Windows, primarily used by system administrators for event log management. Its capabilities include:
- Exporting logs to XML.
- Clearing entire event logs.
- Querying logs using specific criteria.
However, as Jitu notes, “These capabilities make wevtutil.exe a double-edged sword: while invaluable for legitimate operations, they can also aid attackers in covering tracks or exfiltrating information.”
Attackers have increasingly adopted LOLBAS techniques to evade detection by using trusted, pre-installed tools. Wevtutil.exe’s presence on all Windows systems makes it an appealing candidate for such exploits.
- Log Clearing for Evasion
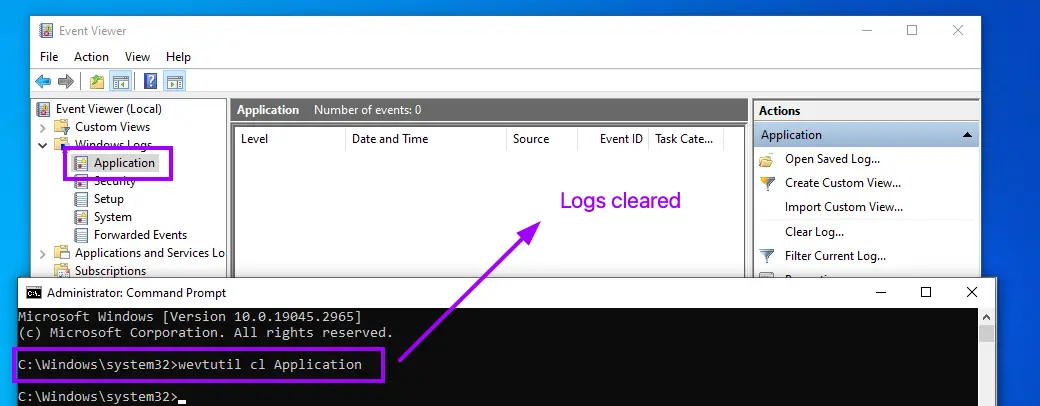
- Commands like
wevtutil cl Applicationallow attackers to clear event logs, making it harder for defenders to track malicious activity. - However, attempts to clear Security logs generate a detectable Event ID 1102, as the report highlights: “Clearing the Security log generates Event ID 1102…making it highly noticeable to defenders.”
- Commands like
- Log Exportation for Data Exfiltration
- Using commands like wevtutil qe Security /f:xml > exported_logs.xml, attackers can export logs to analyze sensitive data or exfiltrate critical information.
- Elevated privileges are necessary for this activity, ensuring some barriers to unauthorized use.
- Reconnaissance Through Log Queries
- Attackers can precisely query logs to gain insights into system or user activity. For example:
- This command retrieves successful logon events, offering valuable intelligence for subsequent actions.
Unlike widely monitored tools like PowerShell, wevtutil.exe often escapes scrutiny. “Using less common utilities could evade traditional detection mechanisms that primarily focus on widely used tools,” states Jitu.
To counter the misuse of wevtutil.exe, organizations should consider the following:
- Enhanced Monitoring
- Track unusual commands executed via wevtutil.exe.
- Set baselines for legitimate usage to detect anomalies.
- Centralized Logging
- Aggregate logs centrally to prevent attackers from covering their tracks locally.
- Behavioral Analytics
- Leverage analytics to identify patterns indicative of LOLBAS techniques.
Jitu concludes in his report: “Understanding these behaviors is crucial for both red teams leveraging this utility and defenders aiming to detect and mitigate its abuse.”
Related Posts:
- Lazarus Group Exploits xattr with “RustyAttr” to Evade Detection
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware