WindowSpy: Cobalt Strike Beacon Object File meant for targeted user surveillance
WindowSpy
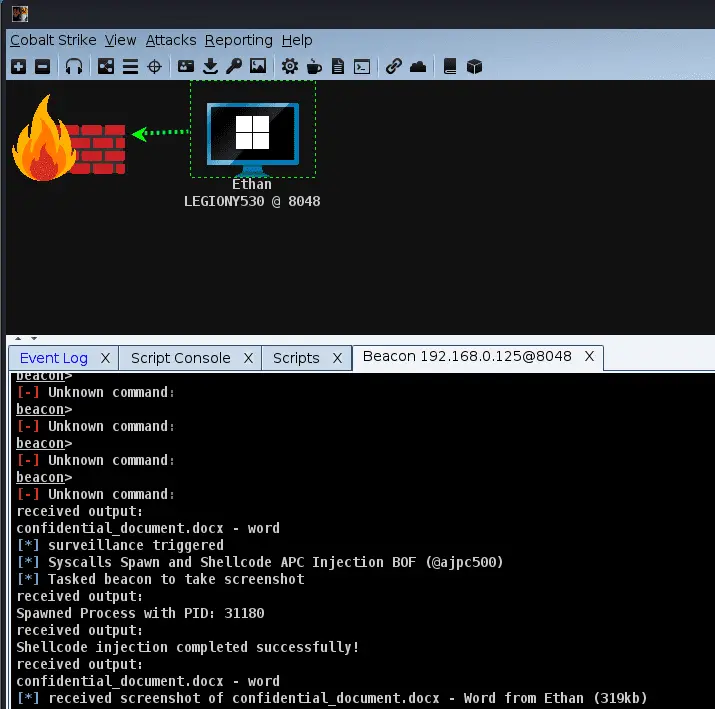
WindowSpy is a Cobalt Strike Beacon Object File meant for targeted user surveillance. The goal of this project was to trigger surveillance capabilities only on certain targets, e.g. browser login pages, confidential documents, vpn logins, etc. The purpose was to increase stealth during user surveillance by preventing detection of repeated use of surveillance capabilities e.g. screenshots. It also saves the red team time in sifting through many pages of user surveillance data, which would be produced if the keylogging/screenwatch was running at all times.
How it works

Each time a beacon checks in, the BOF runs on the target. The BOF comes with a hardcoded list of strings that are common in useful window titles e.g. login, administrator, control panel, VPN, etc. You can customize this list and recompile it yourself. It enumerates the visible windows and compares the titles to the list of strings, and if any of these are detected, it triggers a local aggressorscript function defined in WindowSpy.cna named spy(). By default, it takes a screenshot. You may customize this function however you want, e.g. keylogging, WireTap, webcam, etc.
The spy() function has 1 argument, $1 being the beacon id of the beacon that triggered it.
Installation
- clone the repo: git clone https://github.com/CodeXTF2/WindowSpy.git
- load the WindowSpy.cna script into Cobalt Strike
Building from source
- open the WindowSpy.sln solution file in Visual Studio
- Build for target BOF (x64/x86)
Usage
- Leave it to run. It should automatically run on each beacon checkin and trigger accordingly.
Source: https://github.com/CodeXTF2/