WINELOADER: A Tool for Espionage and Disruption
A new campaign orchestrated by the notorious APT29 hacking group – widely associated with Russia’s Foreign Intelligence Service (SVR) – exposes a dangerous shift in tactics for this sophisticated threat actor. The group has turned its attention towards hacking political parties, as evidenced by the recent targeting of German political entities first detected in late February 2024. A detailed analysis by the Splunk Threat Research Team reveals a multi-pronged attack and the use of a new backdoor malware called ‘WINELOADER’.
The Anatomy of a Sophisticated Attack

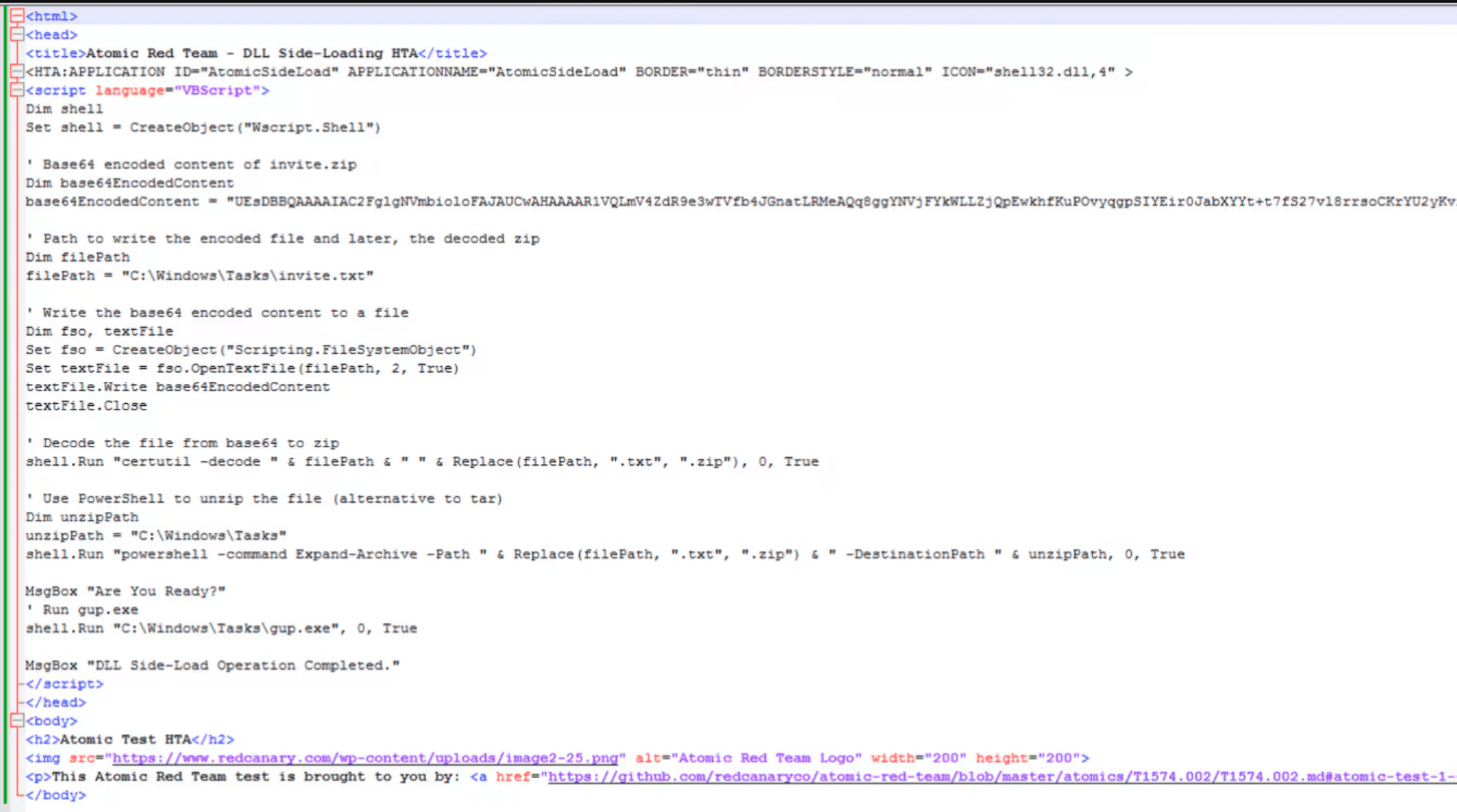
malicious .HTA
Disguised as seemingly innocuous wine-tasting event invitations, carefully crafted spear-phishing emails serve as the initial entry point. Those who take the bait are directed to download a ZIP file hosted on a compromised website. Within this ZIP file lurks an HTML Application (HTA) file which sets off a complex infection chain when unwittingly opened by the victim.
The attackers cleverly leverage legitimate Microsoft software to side-load a malicious component, ultimately installing the WINELOADER backdoor. This process is designed to fly under the radar of traditional security solutions.
Inside WINELOADER
Upon execution, the HTA file deploys obfuscated JavaScript, utilizing techniques reminiscent of the obfuscator.io tool, to further the infection chain. The process includes the deployment of legitimate yet vulnerable Microsoft-signed binaries, such as “sqlwriter.exe” or “sqldumper.exe”. These binaries are manipulated to side-load a malicious DLL— “vcruntime140.dll”, crafted specifically by the attackers. This marks the initial phase of the WINELOADER backdoor installation, highlighting the threat actor’s adept use of legitimate tools for malicious purposes.
Breakdown of WINELOADER’s Capabilities
The intricacies of the WINELOADER malware include advanced capabilities like:
- DLL side-loading to discreetly execute malicious payloads.
- Communication with command and control (C2) servers to receive further malicious instructions or to exfiltrate data.
- Evasion techniques designed to bypass conventional security measures and complicate static analysis by encrypting critical APIs and strings.
This variant of WINELOADER employs an RC4 algorithm for decrypting a significant data segment, which then executes to contact its C2 infrastructure and potentially download additional payloads.
The Vital Role of Cybersecurity Research
The work of Splunk’s Threat Research Team is instrumental in combating threats like APT29. Their in-depth analysis of the WINELOADER campaign arms defenders with the tools and insights needed to protect against this ongoing threat.
A Call to Action
Vigilance is critical in today’s world. Political parties, government organizations, businesses, and individuals must be aware of the advanced tactics used by state-sponsored hackers and take proactive steps to secure their systems and data. The consequences of inaction could have severe repercussions for both individual organizations and the stability of democratic societies.





