The ten WordPress plug-ins provided by the Woo e-commerce website have security flaws. These plug-ins are provided by the same company Multidots for the WOO website. Because the developer has not yet released a patch and the plug-in for the Woo site is used by many high-traffic websites, WordPress has disabled dangerous plug-ins. The following is information on dangerous plugins:
- WooCommerce Category Banner Management (Active installations: 3,000+) – Unauthenticated Settings Change
- Add Social Share Messenger Buttons Whatsapp and Viber (Active installations: 500+) – Cross-site Request Forgery (CSRF)
- Advance Search for WooCommerce (Active installations: 200+) – Stored Cross-site scripting (XSS)
- Eu Cookie Notice (Active installations: 600+) – Cross-site request forgery (CSRF)
- Mass Pages/Posts Creator (Active installations: 1,000+) – Authenticated Stored Cross-Site scripting (XSS)
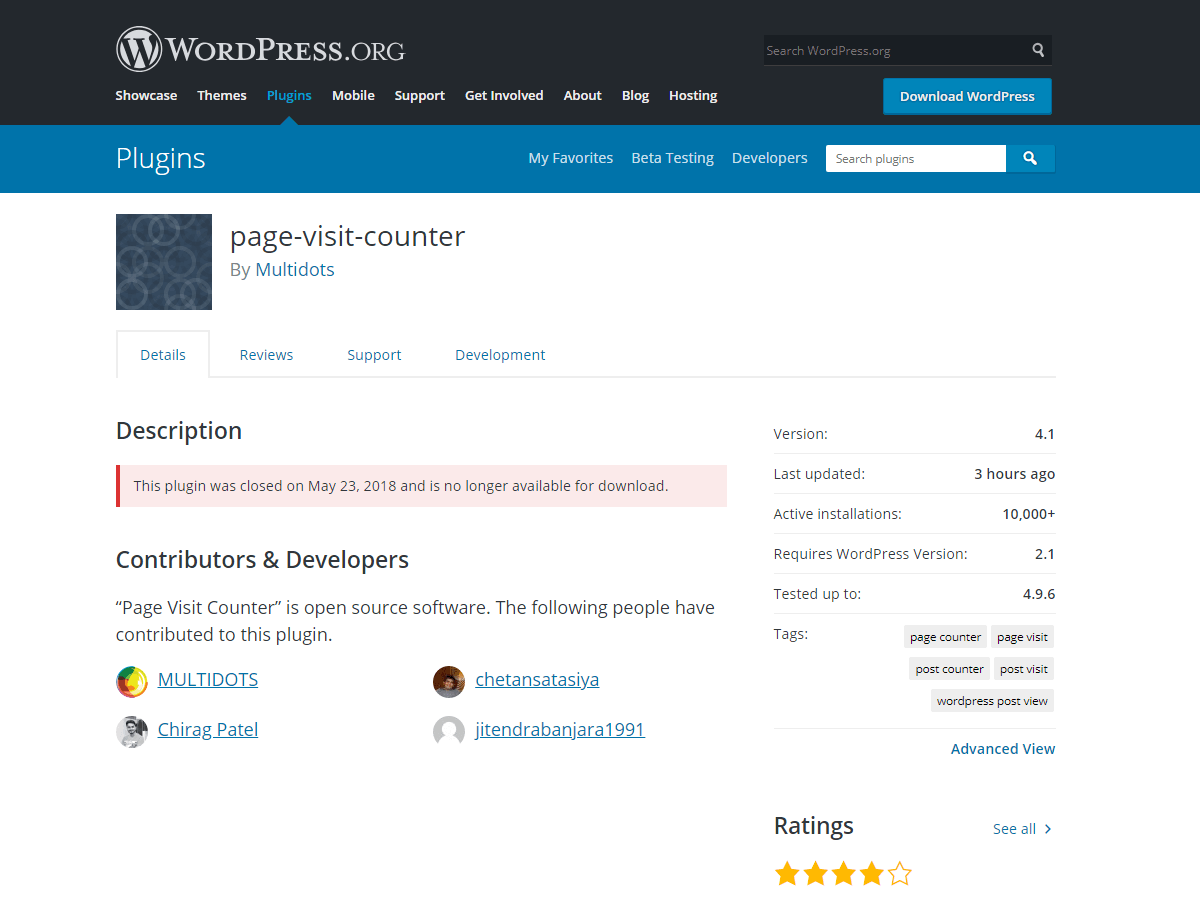
- Page Visit Counter (Active installations: 10,000+) – SQL Injection
- WooCommerce Checkout For Digital Goods (Active installations: 2,000) – Cross-site request forgery (CSRF)
- WooCommerce Enhanced Ecommerce Analytics Integration with Conversion Tracking (Active installations: 1,000+) – Cross-site request forgery (CSRF) and Stored Cross-site scripting (XSS)
- WooCommerce Product Attachment (Active installations: 800+) – Authenticated stored Cross-site scripting (XSS)
- Woo Quick Reports (Active installations: 300+) – Stored Cross-Site Scripting (XSS)
According to ThreatPress, security researchers discovered a wide variety of vulnerabilities in 10 plug-ins. Affected plugins are available through WordPress.org, which allows Woo Marketplace users to manage their online WooCommerce e-commerce and dropshipping stores. According to statistics, there have been nearly 20,000 active installations of vulnerable plugins, inclu10,000-page page access counters, 3,000 WooCommerce category banner installations, and 2,000 WooCommerce Checkout installations.

After researching by security experts, the plug-ins created by Multidots are affected by stored cross-site scripting (XSS), cross-site request forgery (CSRF), and SQL injection vulnerabilities. These vulnerabilities can be used to control the e-commerce of installed plug-ins. website. An attacker can compromise a website, execute a remote shell, populate a keylogger, and upload cryptocurrency mining programs or other types of malware.
Given that the affected sites are online stores that collect personal and financial information, attackers may be able to obtain valuable information. These vulnerabilities allow unauthenticated attackers to inject malicious JavaScript, thus providing an opportunity to hijack customer’s credit card data and receive customer and administrator logins. Although most dangerous scenarios require the installation of plug-in access URLs or pages, there are still some vulnerabilities that can be exploited without any interaction.
Multidots confirmed the problem after it was known on May 8, and then it did not act again. Fortunately, WordPress learned to decide to disable most of the affected plugins. Before ThreatPress publicly released the survey results, they had contacted Multidots for comments, but the company did not respond.
The CVE identifier has been assigned to four of these vulnerabilities and there are still six vulnerabilities that have not yet been identified. So far, the assigned identifiers are CVE-2018-11579, CVE-2018-11580, CVE-2018-11633, and CVE-2018-11632.
The current technical details and proof of concept (PoC) code for each vulnerability has been disclosed. Experts said: “It’s good to know that WordPress Security reacts quickly, but still, we have a big problem. There is no way to inform all users of these plugins about the threat. It’s strange that WordPress can show you information about available updates, but still can’t protect you by providing the information about closed plugins in the same way. We hope to see some changes in this area. In this case, we could notify owners of affected websites and secure almost twenty thousand websites.”
Source, Image: threatpress