Xerror: fully automated pentesting tool
Xerror
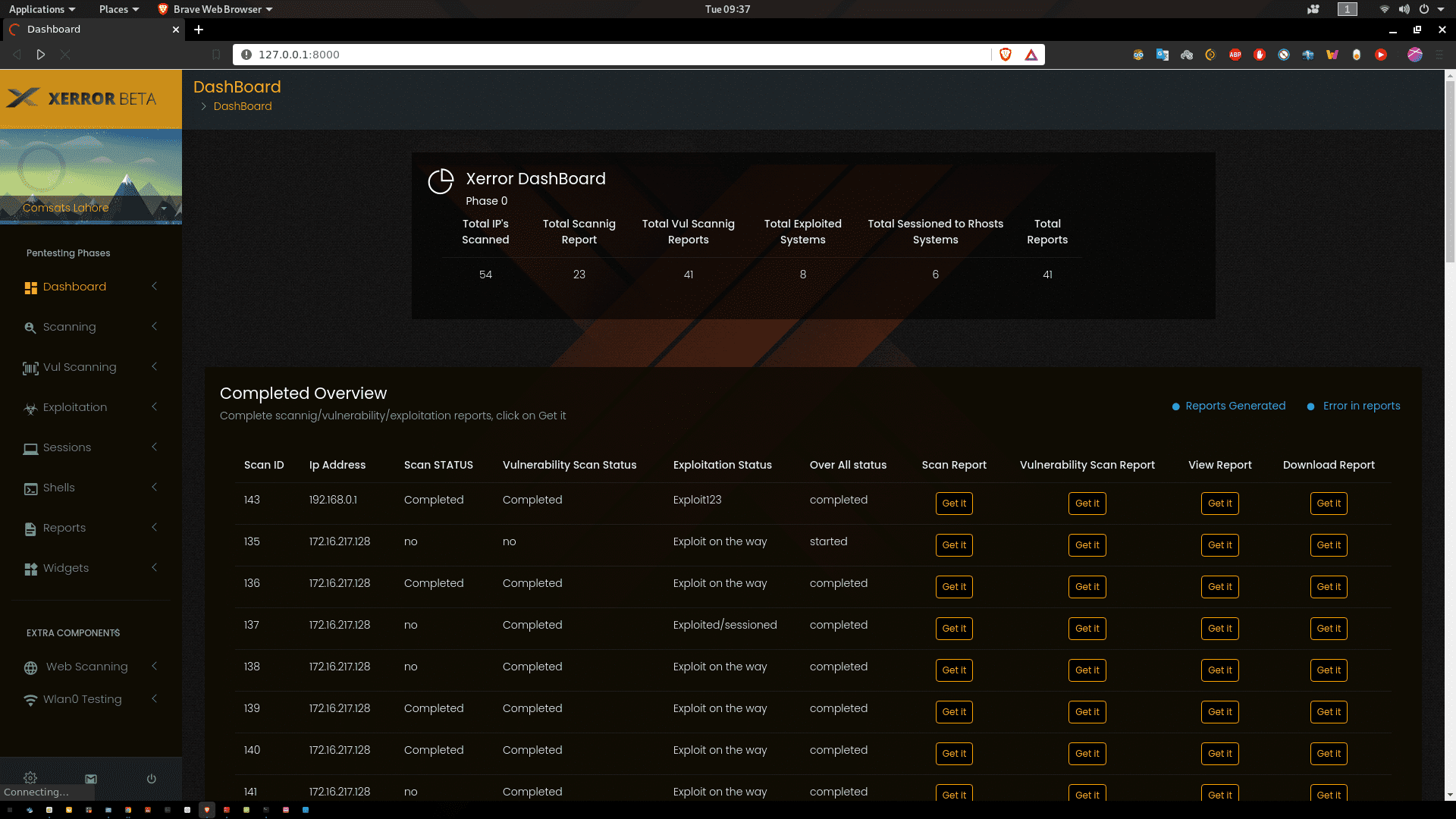
Xerror is an automated penetration tool, which will helps security professionals and nonprofessionals to automate their pentesting tasks. Xerror will do all tests and, at the end generate two reports for executives and analysts.
 After completion of Xerror, it will provide GUI, and internally it supports openVas, Nessus and Nexpose for vulnerability scanning, Metasploit for exploitation, and gives GUI based options after successful exploitation e.g Meterpreter sessions. Building in python as a major.
After completion of Xerror, it will provide GUI, and internally it supports openVas, Nessus and Nexpose for vulnerability scanning, Metasploit for exploitation, and gives GUI based options after successful exploitation e.g Meterpreter sessions. Building in python as a major.
cve_2_MSF_exploit_Mapping
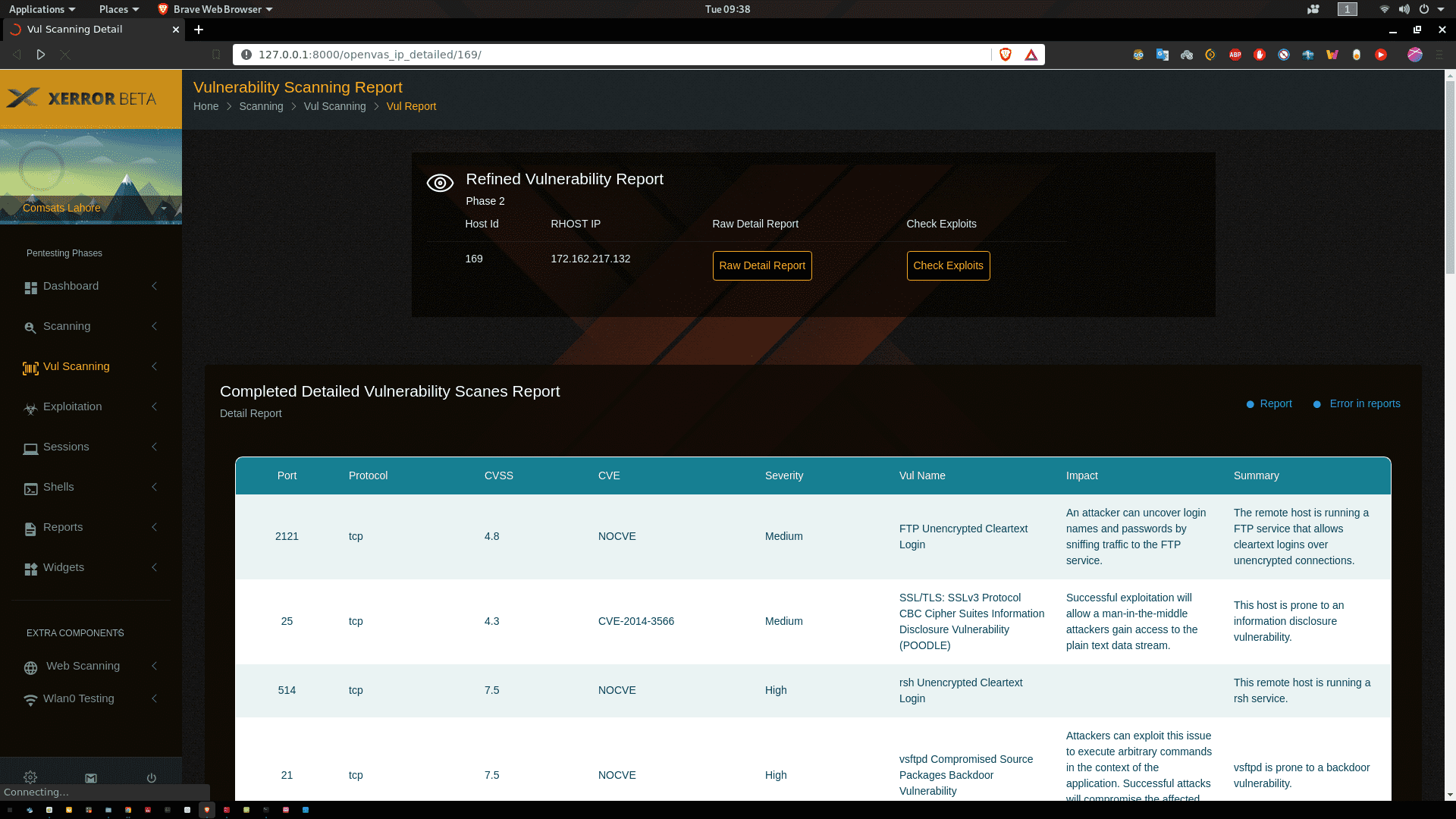
This module parse the openvas csv report, extract CVE number, and map with msf exploits_CVE file( msf_module_result folder have 1446 exploit list). At the end of the program returns the clean result containing CVE#, port, protocol, exploit_name.
Download
git clone https://github.com/Chudry/Xerror.git
Use
- Activate the virtual environment by following the command source env/bin/activate
- Start redis server service redis-server start
- Start python server
- cd xerror
- python mana.py runserver
- Start celery server
- cd xerror
- celery -A xerror worker -l info
- Start msfrpc server msfrpcd -P 123 -S -a 127.0.0.1
- Start openvas server for a default set OMP server credentials to admin@admin 127.0.0.1 9392
Source: https://github.com/Chudry/