Xiū Gǒu Phishing Kit: The ‘Doggo’ of Phishing Campaigns with Global Reach
The Netcraft research team recently revealed details about a new and distinct phishing kit known as “Xiū Gǒu” (修狗). In use since September 2024, this phishing toolkit has been deployed in targeted campaigns across the US, UK, Spain, Australia, and Japan, with over 2,000 phishing websites identified. The report states that Xiū Gǒu is actively “targeting organizations in the public sector, postal, digital services, and banking sectors” in a bid to steal sensitive information from unsuspecting victims.
The kit’s developers have branded Xiū Gǒu with a playful “doggo” mascot, which features as a cartoon dog in the admin panel. This mascot even comes with a hidden feature—an “Easter egg” that turns the mascot into a “thug life” version when clicked. Netcraft observed, “User experience is key, as we can see by xiū gǒu’s use of specific scripting languages as well as the inclusion of user tutorials.” The humorous, friendly exterior of the kit contrasts sharply with the serious threat it poses.
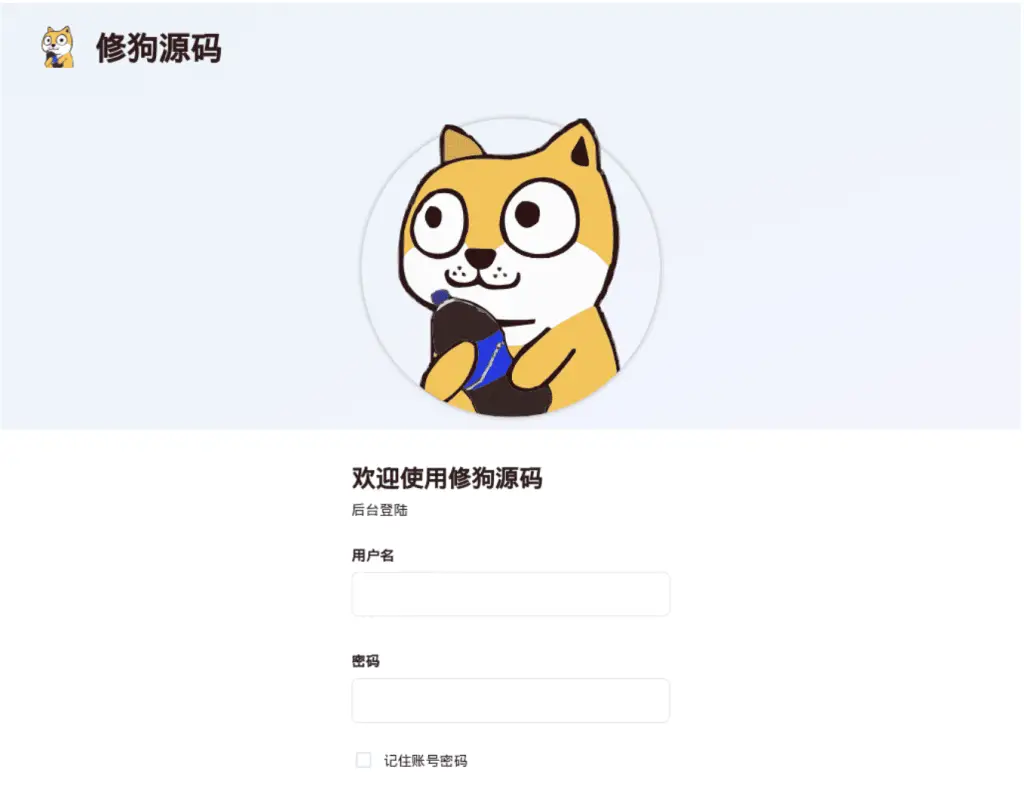
Admin Panel Login with “Doggo” mascot
Xiū Gǒu operates with a modern tech stack, using Vue.js for the front end and a Golang back-end, making it distinct from more traditional PHP-based phishing kits. It also includes features designed for efficient data exfiltration, such as Telegram bots that send stolen credentials directly to the threat actors. “The kit comes equipped with Telegram bots to exfiltrate credentials, ensuring that threat actors can maintain access to data even if their phishing site is taken down,” the report explains.
One of Xiū Gǒu’s notable tactics involves using Rich Communications Services (RCS) instead of SMS to lure victims with scam messages, often relating to government payments, postal fees, or motorist fines. Victims are led to convincing phishing pages styled to resemble legitimate websites, including those of USPS, the UK government, and major banks. Once victims enter their personal details, these are immediately exfiltrated to the attackers through the integrated Telegram bot system.
To prevent detection, Xiū Gǒu operators rely on Cloudflare’s anti-bot protection and often choose the “.top” domain, aligning with scam themes by incorporating terms such as ‘parking’ or ‘living.’ Netcraft found that Xiū Gǒu domains targeting UK users frequently used variations of “yingguo.top” (Yingguo being the Chinese name for the United Kingdom). The report highlights, “By observing the full list of domains using xiū gǒu, we’ve identified threat actors targeting UK victims specifically”.
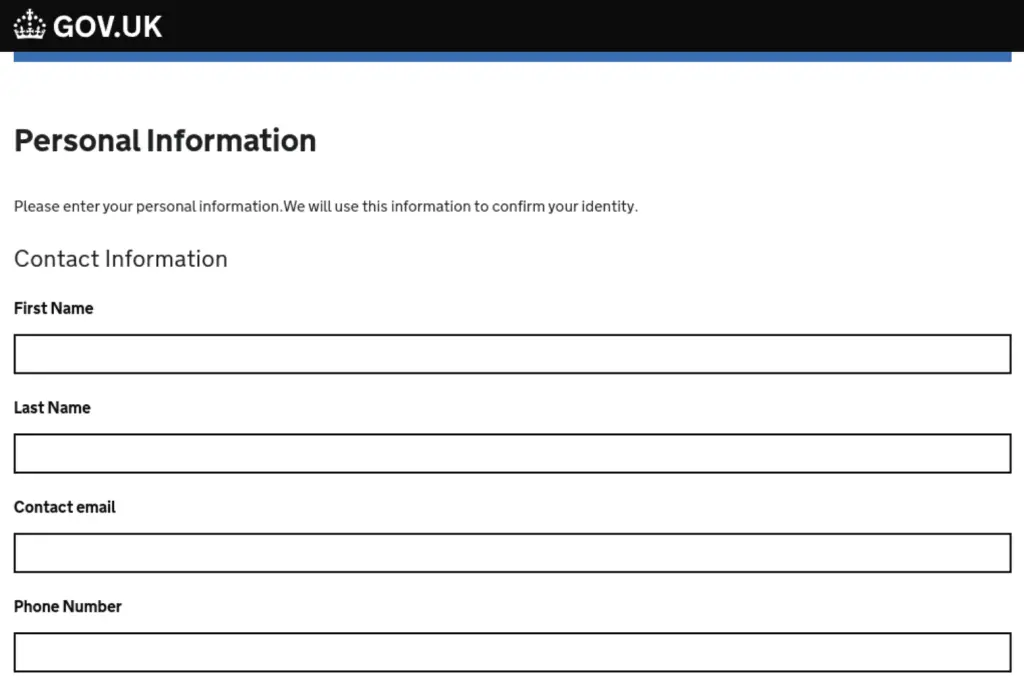
Fake PCN form mimicking gov.uk
By focusing on user experience, data exfiltration methods, and anti-detection tactics, Xiū Gǒu sets a new standard for phishing kits, likely encouraging similar developments in the cybercriminal community. As Netcraft concludes, “Understanding how phishing tradecraft are developed is essential to preventing phishing attacks,” reinforcing the importance of continued analysis and monitoring of emerging threats.
Related Posts:
- USPS Impersonation Scams Surge: Fake Domains Rival Real USPS Website in Traffic
- UK National Cyber Security Centre: Do not use ZTE equipment and services in the telecommunications industry
- Google Cloud Services Disrupted in UK Due to Power Outage
- Ransomware Cyber Attacks Spike to Over 1.2 mn per Month