xortool v1.0 released: A tool to analyze multi-byte xor cipher
xortool.py
A tool to do some xor analysis:
- guess the key length (based on the count of equal chars)
- guess the key (base on knowledge of most frequent char)
Changelog v1.0
- switch to poetry build system, set new version 1.0.0
Download
python3 -m pip install –user xortool
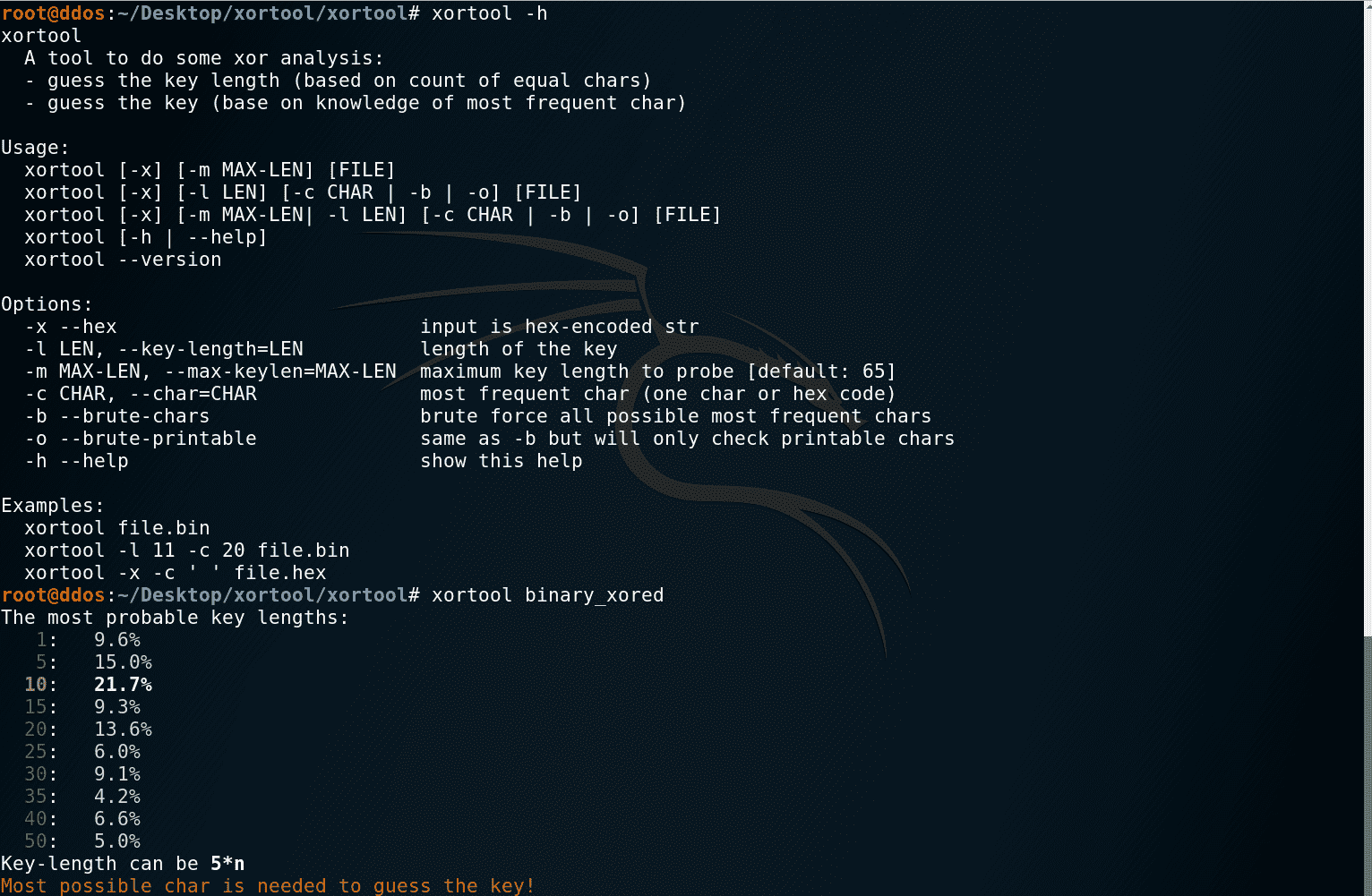
Usage

Example
The most common use is to pass just the encrypted file and the most frequent character (usually 00 for binaries and 20 for text files) – length will be automatically chosen:
Here, the key is longer than default 32 limit:
So, if automated decryption fails, you can calibrate:
- (
-m) max length to try longer keys - (
-l) selected length to see some interesting keys - (
-c) the most frequent char to produce right plaintext
Copyright (c) 2014 Hellman ( hellman1908@gmail.com )
Source: https://github.com/hellman/





