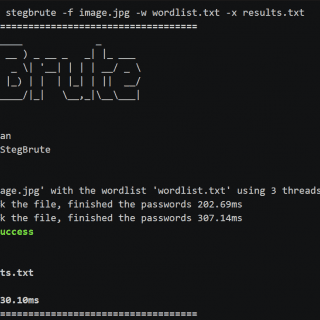
sncscan: Tool for analyzing SAP Secure Network Communications (SNC)
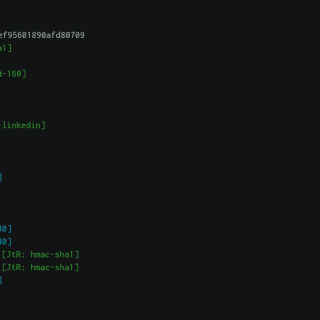
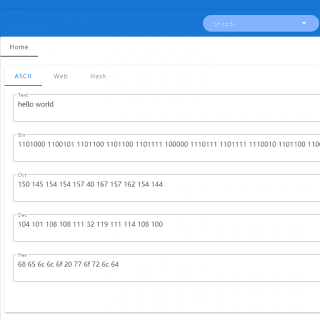
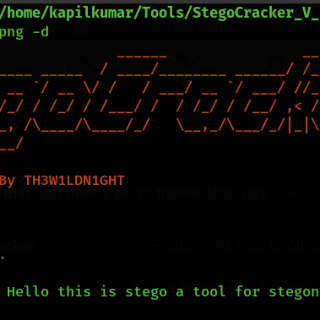
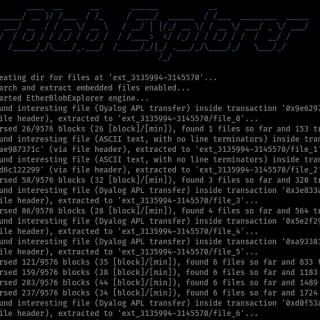
sncscan Tool for analyzing SAP Secure Network Communications (SNC). Background: SNC system parameters SNC Basics SAP protocols, such as DIAG or RFC, do not provide high security themselves. To increase security and ensure Authentication,...