stegcloak: The Cloak of Invisibility for your texts
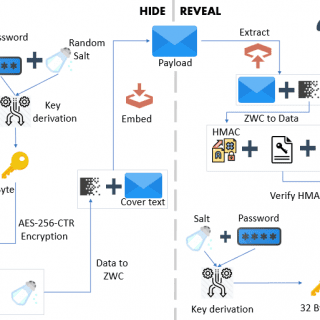
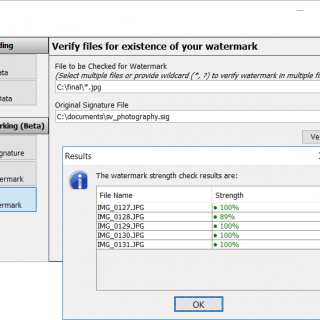
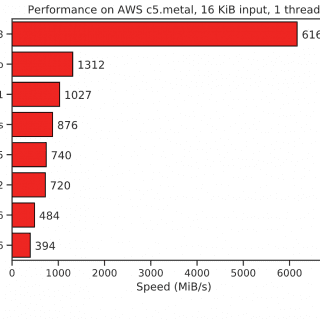
StegCloak StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside the text by compressing and encrypting the secret before cloaking it with special Unicode invisible characters. It...