XSS Jacking: new XSS attack that combines hijacking, Self-XSS, copy and paste hijacking

XSS Jacking is a new XSS attack by Dylan Ayrey that can steal sensitive information from the victim. XSS Jacking requires three paired with other technologies, are clicking hijacking, hijacking and paste Self-XSS, and even need the help of some social engineering, so this attack only those who also have storage type XSS vulnerabilities or CSRF Vulnerability Vulnerability on the site.
The necessary conditions for XSS hijacking attacks
There are several conditions necessary to form an XSS hijacking attack:
1. The target site must have click-through hijacking vulnerability
2.Self-XSS
3. Paste hijacking
Click hijacking, is a way to lead the victim to hackers designed a good trap of deceptive means. When the victim clicks on a button on a screen, there is actually no point to really point to the target page where the attacker has previously adjusted the opacity to zero.
Self-XSS (a cross-site scripting attack) is an XSS attack that is triggered by the victim’s own input XSS payload. This attack can be based on the DOM or on a domain that is only accessible or visible to the user.
Knowing Self-XSS, we can guess the attack ideas. However, how can we allow users to copy and paste malicious text? Copy action can be automated, this process requires the user to do the action is pasted!
This requires the use of paste hijacking attacks, and this attack has been there for many years, mainly in the copy and paste the data behind the secretly add malicious text to achieve.
XSS hidden in the “copy and paste” behind
Now there is such a website, there is self-XSS vulnerability https://security.love/XSSJacking.
The following figure is a simplified XSS code, if the box in the input alert (1) will play the window.
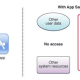
Attack in the use of paste hijacking technology, is the XSS payload paste to other domain name text bar framework. Since the location of these frames can be changed and not visible, you can use click hijacking to let the user feel that he is still visiting the site he is “visiting”. In fact, he has triggered a Self-XSS vulnerability, hackers can get his sensitive information.
Through XSS hijacking attacks, hackers can steal the user’s cookie, inbox information, configuration details, modify the configuration file settings (such as mobile phone number, mailbox number) or perform other malicious operations.
Conclusion
Today’s loopholes in the bonus items will be hijacked and Self-XSS excluded, once the two loopholes exist at the same time, it is no longer difficult to enforce the XSS payload on the target machine.
Dylan Ayrey said that many companies will ignore XSS-related vulnerability reports, he specifically mentioned
Attackers now have more and more innovative ways to take advantage of Self-XSS, I think companies will receive such a report, will begin to pay attention to this problem.