yasuo: scans for vulnerable & exploitable 3rd-party web applications

Yasuo is a ruby script that scans for vulnerable 3rd-party web applications.
While working on a network security assessment (internal, external, redteam gigs etc.), we often come across vulnerable 3rd-party web applications or web front-ends that allow us to compromise the remote server by exploiting publicly known vulnerabilities. Some of the common & favorite applications are Apache Tomcat administrative interface, JBoss jmx-console, Hudson Jenkins and so on.
If you search through Exploit-db, there are over 10,000 remotely exploitable vulnerabilities that exist in tons of web applications/front-ends and could allow an attacker to completely compromise the back-end server. These vulnerabilities range from RCE to malicious file uploads to SQL injection to RFI/LFI etc. It is built to quickly scan the network for such vulnerable applications thus serving pwnable targets on a silver platter.
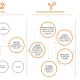
Tetris-style Program Flow
Install
git clone https://github.com/0xsauby/yasuo.git
cd yasuo
bundle install –path vendor
bundler exec ./yasuo.rb -f [myfile]
Usage
Yasuo provides following command-line options:
-r :: If you want Yasuo to perform the port scan, use this switch to provide an IP address or IP range
-l :: If you want Yasuo to perform the port scan, use this switch to provide an input file with new-line separated IP addresses, similar to nmap’s -iL option
-s :: Provide custom signature file. [./yasuo.rb -s mysignatures.yaml -f nmap.xml] [Default – signatures.yaml]
-f :: If you do not want Yasuo to perform the port scan and already have a nmap output in xml format, use this switch to feed the nmap output
-u :: Takes a newline-separated file of URLs saved from the previous run of Yasuo. See below for more details.
-n :: Tells Yasuo to not ping the host while performing the port scan. Standard nmap option.
-p :: Use this switch to provide the port number(s)/range
-A :: Use this switch to scan all the 65535 ports. Standard nmap option.
-b [all/form/basic] :: If the discovered application implements authentication, use this switch to brute-force the auth. “all” will brute-force both form & http basic auth. “form” will only brute-force form-based auth. “basic” will only brute-force http basic auth.
-t :: Specify the maximum number of threads
-h :: Well, take a guess
Source: https://github.com/0xsauby/