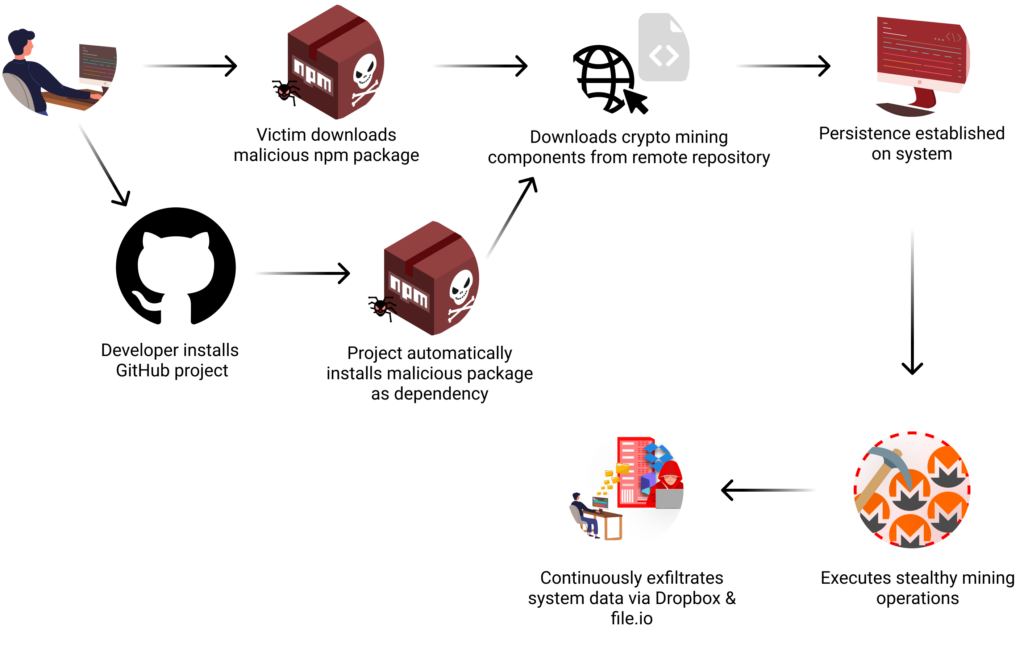
Attack Flow | Image: Checkmarx
The Checkmarx Security Research Team has uncovered a year-long supply chain attack involving the malicious NPM package @0xengine/xmlrpc. What began as a legitimate XML-RPC implementation in October 2023 morphed into a sophisticated cyber threat, combining cryptocurrency mining with data theft. The attack underscores the persistent vulnerabilities in the software supply chain.
Initially appearing as a “pure JavaScript XML-RPC server and client implementation for Node.js,” the package evolved maliciously after version 1.3.4. “This consistent update pattern helped maintain an appearance of legitimate maintenance while concealing the malicious functionality,” the report notes. Over its lifespan, the package received 16 updates, with the most recent published in October 2024.
The malicious code was concealed in the validator.js file, designed to activate only when specific conditions were met. The malware’s ability to mimic legitimate functionality allowed it to evade detection for an unusually long time in the NPM ecosystem.
The attackers used two distribution methods:
- Direct NPM Installation: Developers directly downloaded
@0xengine/xmlrpc. - Dependency in a Legitimate Repository: A GitHub project, “yawpp,” masqueraded as a WordPress posting tool while covertly installing the malicious package.
“This strategy exploits the trust developers place in package dependencies,” the researchers explained. By embedding the package as a dependency in a legitimate-looking project, attackers increased its reach while maintaining stealth.
Once triggered, the malware initiated a multi-stage attack:
- Data Theft: Sensitive information such as SSH keys, bash history, and environment variables was collected and exfiltrated every 12 hours through Dropbox and file.io APIs.
- Cryptocurrency Mining: The attack leveraged XMRig to mine Monero, targeting Linux systems. By October 2024, the attacker’s Monero wallet had 68 active miners connected through the hashvault.pro mining pool.
The malware employed sophisticated evasion techniques, halting operations when user activity was detected and avoiding security monitoring tools.
To ensure long-term control, the malware disguised itself as a legitimate system service, “Xsession.auth,” configured to start automatically on system boot. This persistence mechanism allowed mining operations to resume seamlessly after reboots. A daily check-in mechanism also enabled the attackers to update configurations and receive new commands.
This campaign highlights the dual threat of malicious packages and compromised legitimate ones. As the researchers warn, “A package’s longevity and consistent maintenance history do not guarantee its safety.” Developers must implement robust security measures, including:
- Thorough vetting of all open-source dependencies.
- Regular audits of package updates.
- Use of monitoring tools to detect anomalous behavior.
Related Posts:
- Malicious npm Packages Exploiting Typosquatting to Inject SSH Backdoors
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- North Korean Cyberattacks Persist: Developers Targeted via npm
- Major npm flaw crashes Linux Systems, force users to reinstall