z9 PowerShell Log Analyzer
This tool detects the artifact of the PowerShell-based malware from the eventlog of PowerShell logging.
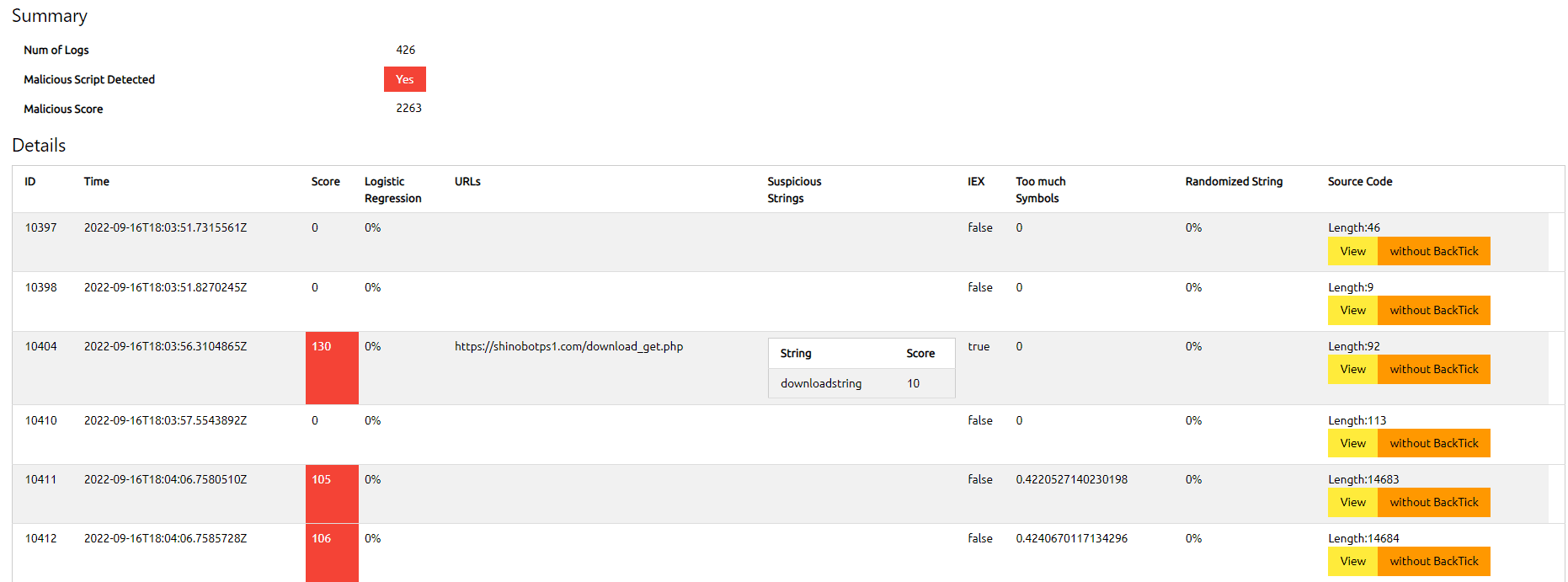
The strength of PowerShell scripts lies in their ability to run without touching the file system, which is referred to as fileless malware. This feature makes detection more challenging. Another obstacle in detecting malicious PowerShell scripts is their obfuscation. Similar to other scripting languages, PowerShell is easy to obfuscate, making it difficult to identify any malicious activity. The Z9 PowerShell Script Analyzer tackles this challenge by performing both static and dynamic analysis to determine whether the script is malicious or not. The analyzer examines the script’s behavior and structure, ensuring that it can identify any potentially harmful actions taken by the script. By analyzing the PowerShell execution logs, the analyzer can detect and prevent any malicious activity, making it an essential tool for cyber security professionals.

How it works
Z9 is specifically designed to analyze PowerShell execution logs, focusing on the log of each script block rather than the script as a whole. Fortunately, Microsoft has provided a method for logging PowerShell execution on a per-script-block basis. This approach enables us to retrieve the plain-text source code of the PowerShell, even when it has been obfuscated. This is because there is always a deobfuscation routine that ultimately leads to the execution of the plain-text version of the script, which can then be logged.
Z9 analyzes the XML file exported from the eventlog, with several detection engines and the following features.
Feature
| Obfuscation Detection | |
| ◮ | Symbol-Alphanumeric Rates |
| ◮ | Randomized String |
| Black Listed String | |
| ◮ | IEX Detection |
| ◮ | Static Blacklist |
| ◮ | Logistic Regression Analysis |
| Misc | |
| ◮ | Syntax Highlighting |
| ◮ | Sandbox |
| ◮ | Explanation by ChatGPT |
Install & Use
Copyright (c) 2022 Sh1n0g1