zelos v0.2 releases: comprehensive binary emulation and instrumentation platform
Zelos
Zelos (Zeropoint Emulated Lightweight Operating System) is a python-based binary emulation platform. One use of Zelos is to quickly assess the dynamic behavior of binaries via command-line or python scripts. All syscalls are emulated to isolate the target binary. Linux x86_64 (32- and 64-bit), ARM, and MIPS binaries are supported. Unicorn provides CPU emulation.
Changelog v0.2
Added
- Plugins: Yarascan
- Introduction of Zelos Manipulation Language (ZML), used for specifying events on the command line and in scripts. New zml_hook function in api
- Ability to redirect input to stdin
- Hooks for internal memory reads, writes, and maps
- Linked to crashd plugin, containing separate plugins for heap memory guards, static analysis via IDA Pro, and dataflow using QEMU TCG
Changed
- Moved to different command line flags for specifying what degree of information (instructions or syscalls) is printed while running
- Better support for lists in command line arguments
- Flags can be passed to the emulated program via the command line
- Misc. bug fixes (thanks to seth1002)
- General improvements to syscalls
Removed
- Verbosity command line flag (now handled via other flags)
Installation
pip install zelos
Use
Command-line
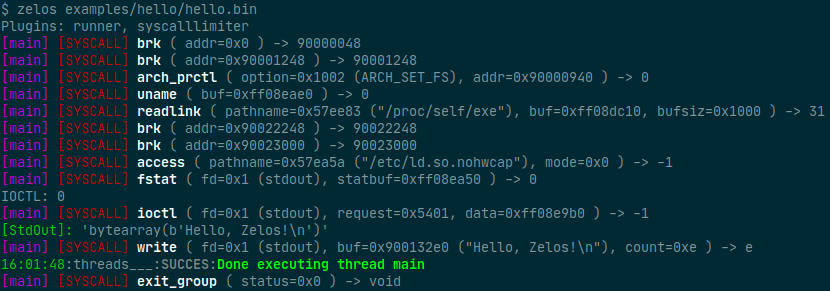
To emulate a binary with default options:
$ zelos my_binary
To view the instructions that are being executed, add the -v flag:
$ zelos -v my_binary
You can print only the first time each instruction is executed, rather than every execution, using –fasttrace:
$ zelos -v --fasttrace my_binary
By default, syscalls are emitted on stdout. To write syscalls to a file instead, use the –strace flag:
$ zelos --strace path/to/file my_binary
Specify any command-line arguments after the binary name:
$ zelos my_binary arg1 arg2
Programmatic
import zelos
z = zelos.Zelos("my_binary")
z.start(timeout=3)
Tutorial
Copyright (C) 2020 zeropointdynamics