Image: Volexity
Cybersecurity firm Volexity has uncovered a zero-day vulnerability in Fortinet’s Windows VPN client, FortiClient, being exploited by the BrazenBamboo Advanced Persistent Threat (APT) group. This vulnerability, detailed in Volexity’s latest report, enables attackers to extract VPN credentials directly from process memory using their modular malware, DEEPDATA.
Volexity identified the flaw in July 2024, describing how user credentials, including usernames and passwords, remain in FortiClient’s process memory after authentication. BrazenBamboo, a Chinese state-affiliated APT group, has weaponized this vulnerability through the FortiClient plugin in their DEEPDATA malware. The plugin “extracts credentials and server information from the process memory of FortiClient VPN processes,” leveraging a method reminiscent of a similar vulnerability reported in 2016.
“Volexity verified the presence of these JSON objects in memory and confirmed this approach works against the latest version available at the time of discovery (v7.4.0),” the report states. Fortinet was notified of the issue on July 18, 2024, but as of now, the vulnerability remains unresolved, with no CVE assigned.
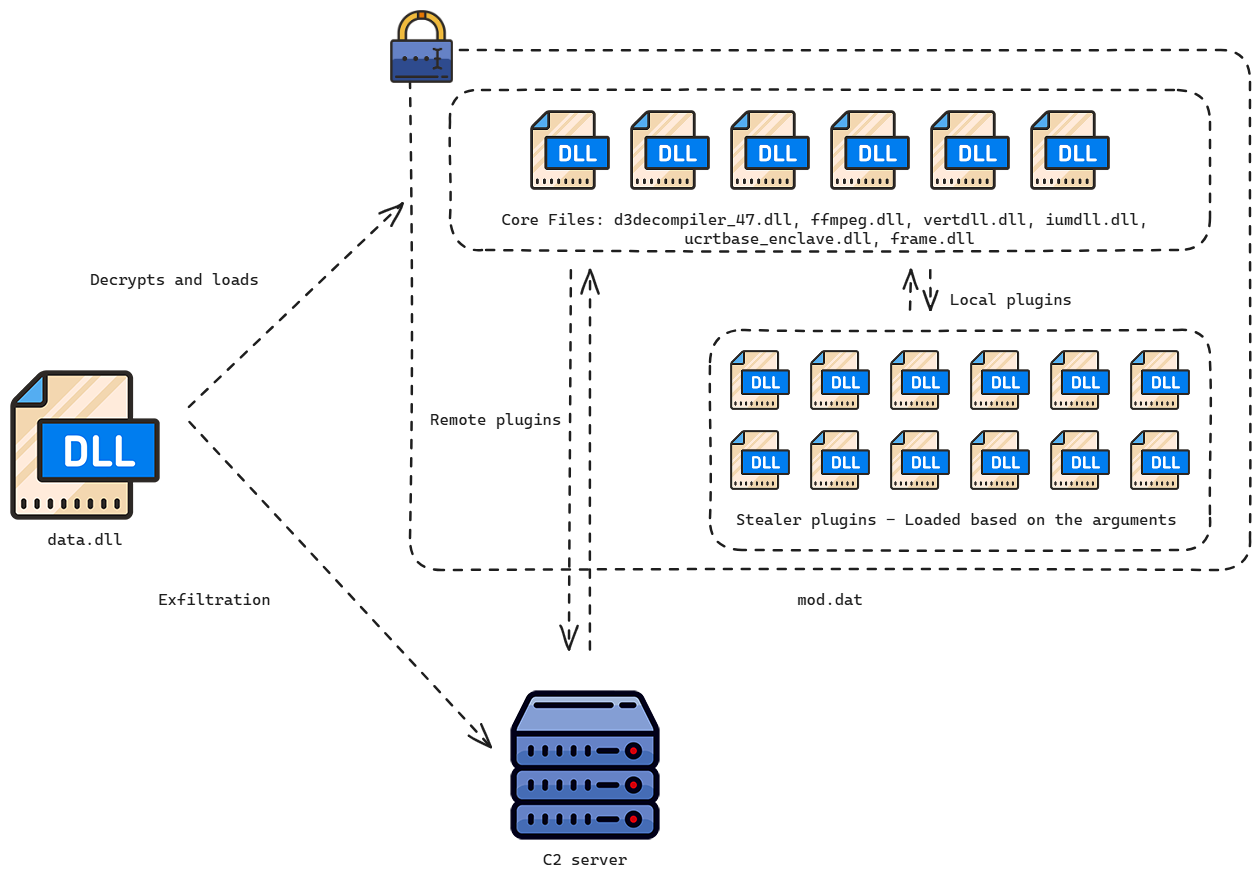
DEEPDATA is a sophisticated post-exploitation framework designed to extract sensitive data from compromised systems. Its capabilities extend beyond FortiClient credential theft to include:
- Stealing browser cookies, history, and passwords
- Recording audio and keystrokes
- Collecting data from messaging apps like WeChat, Line, and Telegram
- Extracting WiFi credentials and system information
The malware’s modular architecture enables attackers to load plugins as needed, enhancing its adaptability. Volexity uncovered 12 unique plugins, including one specifically targeting FortiClient.
BrazenBamboo, known for developing the LIGHTSPY and DEEPPOST malware families, demonstrates a consistent evolution in its tactics. “The DEEPDATA malware family has several overlaps with the LIGHTSPY malware family,” Volexity explains, citing shared plugin names, development paths, and command-and-control (C2) infrastructure. LIGHTSPY variants, which target multiple operating systems, including iOS and Windows.
The DEEPPOST tool complements DEEPDATA by exfiltrating data to remote servers using HTTPS. Together, these tools highlight BrazenBamboo’s sophisticated approach to cyber espionage.
The exploitation of FortiClient underscores the importance of securing widely used enterprise tools. As VPN clients are critical to remote work environments, this vulnerability poses significant risks to organizations relying on Fortinet solutions.
Related Posts:
- APT41’s LightSpy Campaign Expands with Advanced DeepData Framework in Targeted Espionage Against Southern Asia
- Volexity: Indian APT hacker organization Patchwork target US think tanks
- Critical Fortinet Vulnerability Exploited: Hackers Deploy Remote Control Tools and Backdoors
- PoC Exploit Released for Critical Fortinet FortiClient EMS CVE-2023-48788 Flaw
- LightSpy Malware Strikes macOS: Your Mac Could be the Target