Zircolite v2.10 releases: fast SIGMA-based detection tool for EVTX or JSON Logs
Zircolite
Zircolite is a standalone tool written in Python 3. It allows to use SIGMA rules on MS Windows EVTX (EVTX and JSON format)
- Zircolite can be used directly on the investigated endpoint (use releases) or in your forensic/detection lab
- Zircolite is fast and can parse large datasets in just seconds (check benchmarks)
- Zircolite can handle EVTX files and JSON files as long as they are in JSONL/NDJSON format
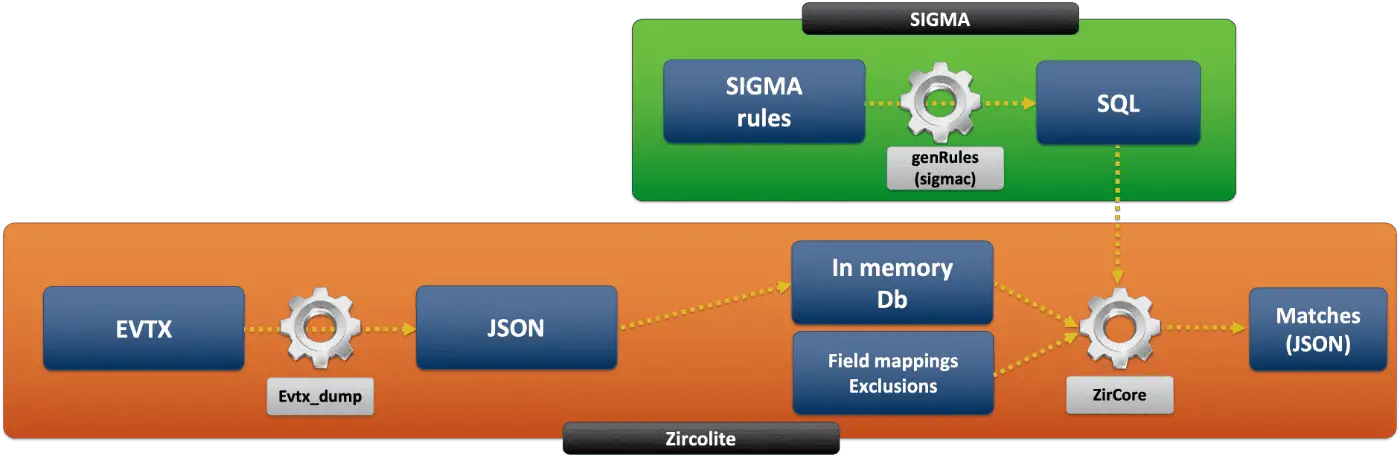
Zircolite architecture
Zircolite is more a workflow than a real detection engine. To put it simply, it leverages the ability of the sigma converter to output rules in SQLite format. Zircolite simply applies SQLite-converted rules to EVTX stored in an in-memory SQLite DB.

Benchmarks (Updated 22nd May 2021)
On an Intel Core-i9 8c/16t – 64 GB RAM – with 765 sigma rules :
| Monocore | Multicore | |
|---|---|---|
| EVTX : 34 GB – 16 files | – | 9 Min |
| EVTX : 7.8 GB – 4 files | – | 162 sec |
| EVTX : 1.7 GB – 1 file | 99 sec | – |
| EVTX : 40 MB – 263 files | 3 sec | 1 sec |
| MORDOR Datasets – APT29 Day 1 (196 081 events) | 62 sec | – |
| MORDOR Datasets – APT29 Day 2 (587 286 events) | 4 min | – |
| MORDOR Datasets – APT3 Scenario 1 (101 904 events) | 70 sec | – |
| MORDOR Datasets – APT3 Scenario 2 (121 659 events) | 27 sec | – |
ℹ️ These results can be largely improved with fine-tuned rulesets and filtering.
Changelog v2.10
- Add CSV and JSON Array logs support by @wagga40 in #70
- Docs have been reworked and available in a dedicated website
- Some code refactoring
⚠️ Some AVs may not like the packaged binaries.
⚠️ The set of tests for windows binaries is far from exhaustive, please create an issue if you encounter difficulties.





