Email Body | Image: Cofense
As millions of users continue to rely on Zoom for everything from business meetings to collaborative projects, threat actors have found new ways to exploit this trusted platform. In a recent report by Jhon Revesencio at the Cofense Phishing Defense Center (PDC), a sophisticated phishing campaign has been uncovered, using Zoom Docs links to target unsuspecting users and compromise their Microsoft accounts.
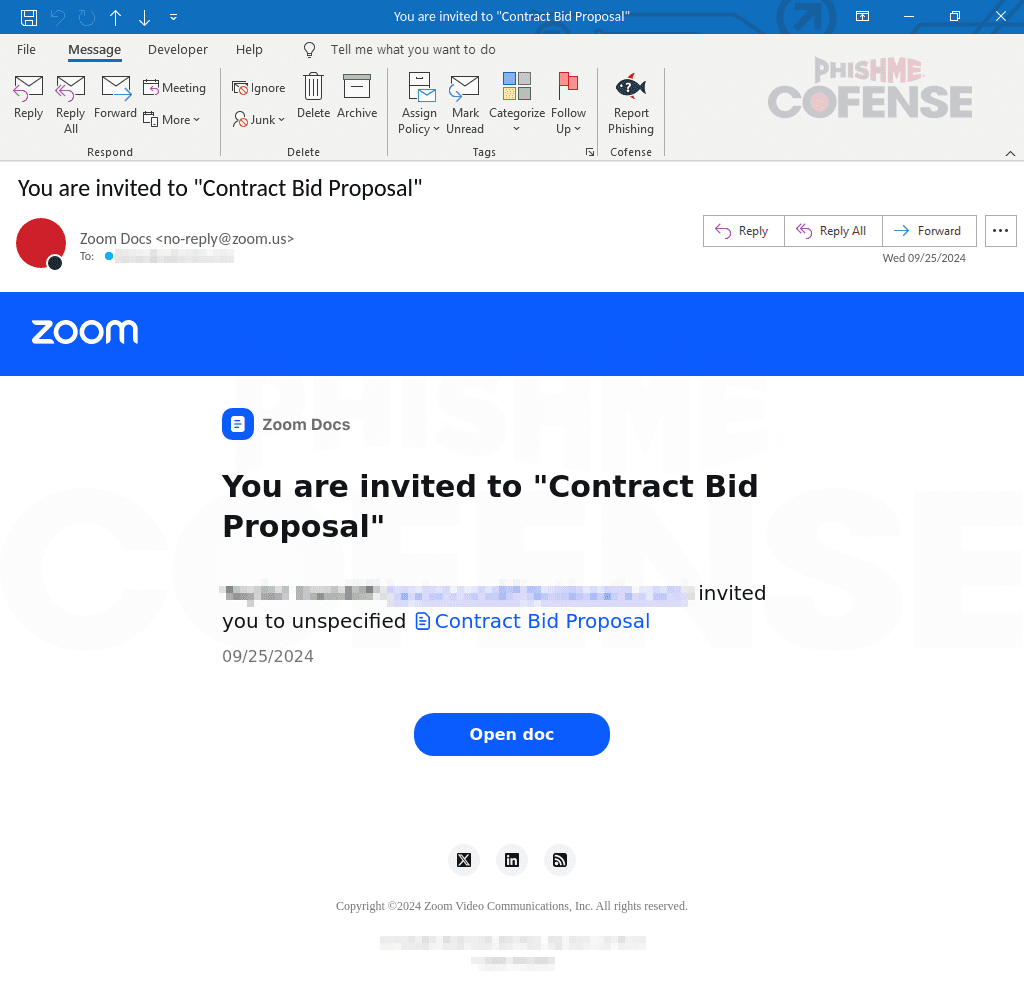
According to the report, this phishing attack is leveraging legitimate Zoom Docs links to make the email appear more credible. The phishing emails are disguised as official notifications from Zoom, often presenting a “shared file” that urges the recipient to take immediate action. The report emphasizes how threat actors are capitalizing on the sense of urgency to lure victims. “By initiating urgency and exploiting the trust associated with well-known platforms, it skillfully manipulates individuals into compromising their credentials,” Jhon Revesencio explains.
The phishing email appears to come from a legitimate address, such as no-reply@zoom.us, which is typically used by Zoom for sending notifications. The subject line often mentions a Contract Bid Proposal or another professional-sounding document to further lower the recipient’s guard. Once the link is clicked, the user is directed to a genuine Zoom Docs page, further legitimizing the scam. “The link directs them to a legitimate Zoom Docs URL,” Revesencio notes.
One of the most alarming aspects of this campaign is its precision targeting of Windows users. The phishing link first verifies whether the victim is using a Windows environment. If not, the phishing page shown is harmless, redirecting non-Windows users to a different page that does not lead to credential theft. However, if the user is on Windows, they are taken to a fake Microsoft login page, designed to look identical to the real thing. “When the user clicks the malicious link from the legitimate Zoom Docs page, they are stepping into a sneaky trap designed just for them,” the report details.
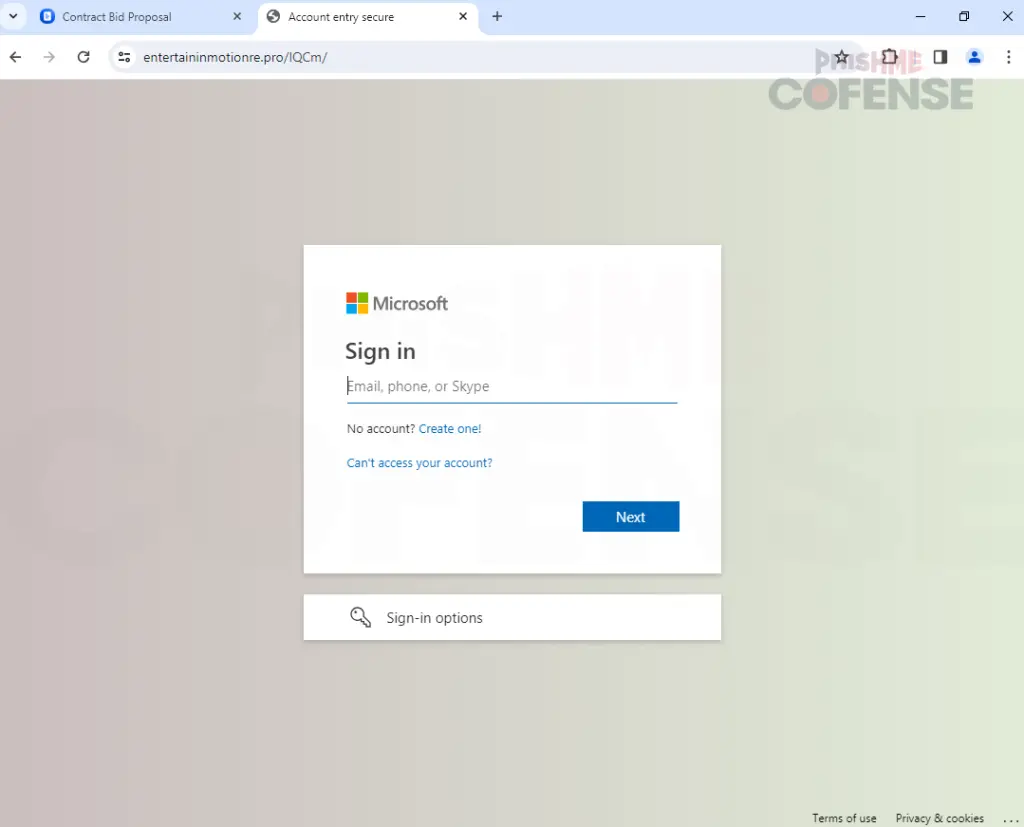
Once the victim enters their credentials, they are compromised. The fake Microsoft login page is near-perfect in its replication, making it difficult for the average user to detect that anything is amiss until it’s too late.
Revesencio’s report highlights how this tactic is becoming more common. “This showcases just how creative the threat actor can be in their attempts to capture unsuspecting users,” the report warns, urging organizations to strengthen their phishing defenses.
Related Posts:
- Zoom Customers Advised to Update Software to Fix Security Vulnerabilities
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Hackers Exploit Google Ads to Target Admins with Fake Software Downloads
- Zoom Patches High-Risk Flaws on Windows Platforms and its Client SDK
- Zoom Releases Patches for Multiple Critical Security Vulnerabilities