Zscaler said in an SSL threat report for the second half of 2017 that there has been a significant increase in phishing and malware attacks that abuse SSL and TLS.
In the first half of 2017, Zscaler’s products blocked 600,000 attacks per day hidden in encrypted traffic, and in the second half of 2017, this number increased to 800,000, which means a 30% increase.
Initially, malicious ads, phishing, and websites were compromised. Attackers used SSL-encrypted tunnels to deliver and distribute malware loads and exploits, as well as communication between infected hosts and command and control (C&C) servers.
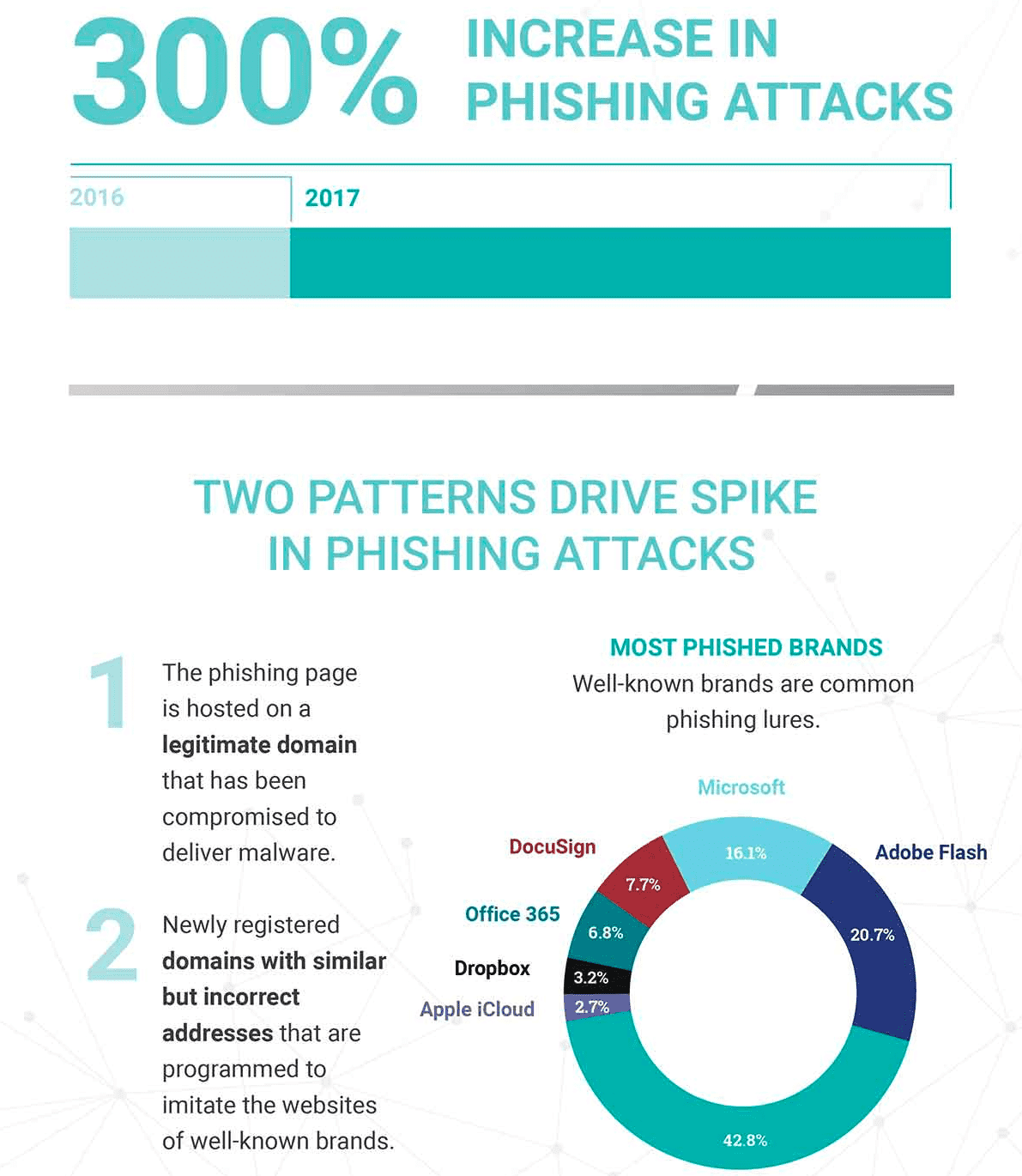
In terms of phishing trends, Zscaler data shows a 400% increase in the first half of 2017 compared to 2016. Overall, phishing activity increased by nearly 300% in 2017.
 Image: zscaler
Image: zscaler
Phishing pages that use HTTPS either end up on sites that have SSL certificates or are hosted on sites that rely on cybercriminals to illegally monetize well-known brands by themselves using free certificates from services such as Let’s Encrypt.
In terms of malware attacks, Zscaler said that 60% of SSL/TLS lanes will be used to deliver bank Trojans and 25% of ransomware throughout 2017. Many attackers get encrypted distribution channels by injecting malware into legitimate services such as Box, Dropbox, Google, and AWS.
An analysis of 6.7 thousand SSL transmissions blocked by Zscaler shows that most of the abused certificates come from legitimate sites that have been compromised.
Security companies have also found that the most commonly used type of certificate in cybercrime is a domain name verification (DV) certificate that is valid for three months and is readily available. Abuse of DV certificates is found in 75% of all incidents, especially those that are freely available.
More than half of the certificates are valid for less than a year, of which approximately one-third of the certificates are valid for three months or less.
Source: zscaler