zzuf: transparent application input fuzzer
zzuf
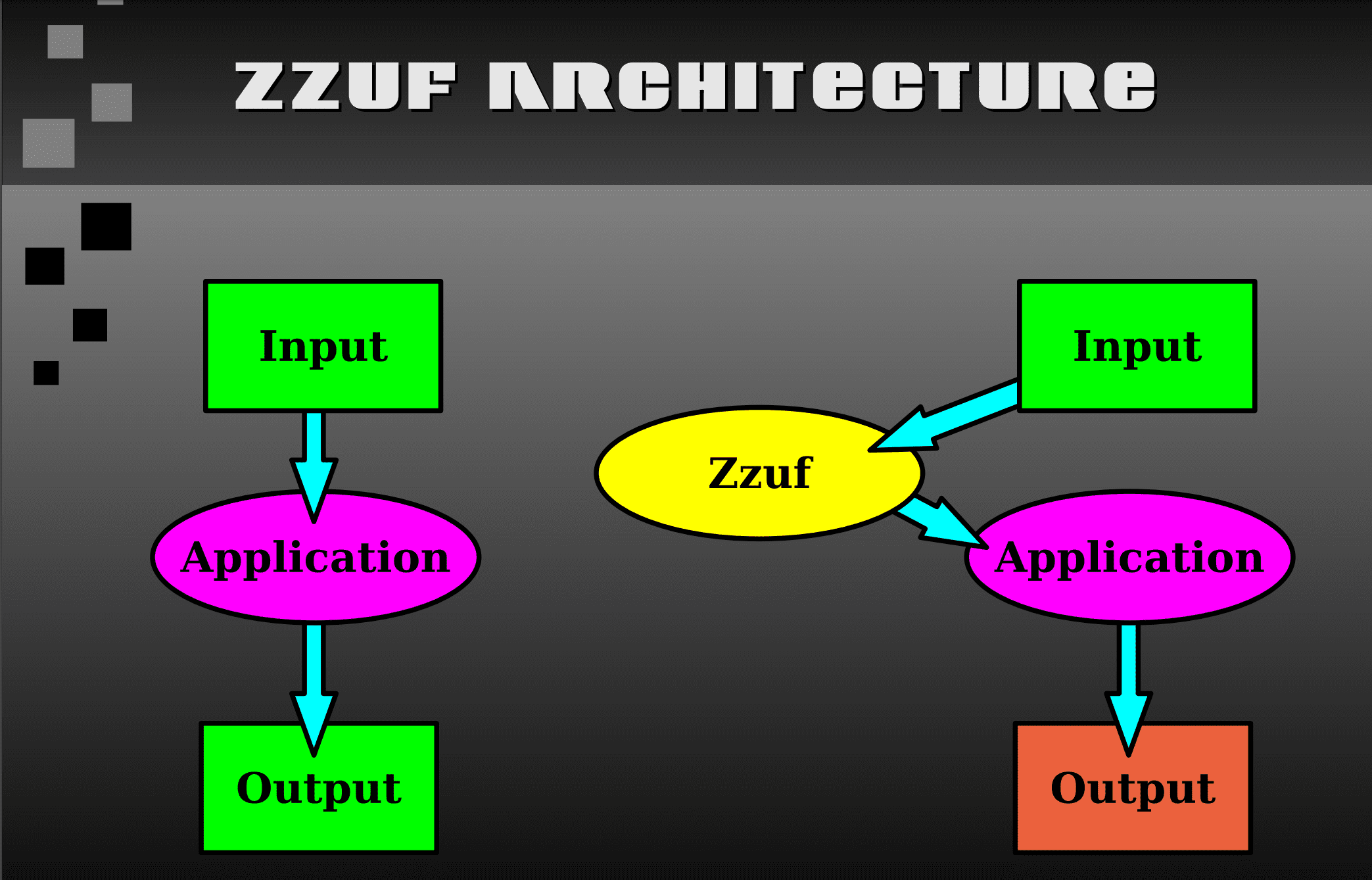
zzuf is a transparent application input fuzzer. Its purpose is to find bugs in applications by corrupting their user-contributed data (which more than often comes from untrusted sources on the Internet). It works by intercepting file and network operations and changing random bits in the program’s input. zzuf’s behaviour is deterministic, making it easier to reproduce bugs. Its main areas of use are:
- quality assurance: use zzuf to test existing software, or integrate it into your own software’s testsuite
- security: very often, segmentation faults or memory corruption issues mean a potential security hole, zzuf helps exposing some of them
- code coverage analysis: use zzuf to maximize code coverage
zzuf’s primary target is media players, image viewers and web browsers because the data they process is inherently insecure, but it was also successfully used to find bugs in system utilities such as objdump.
It is not rocket science: the idea of fuzzing input data is barely new, but zzuf’s main purpose is to make things easier and automated. You can see an old, impressive list of bugs found with zzuf.

The zzuf software consists of two parts:
- The
zzufexecutable - The
libzzufshared library
Here is the global workflow when zzuf fuzzes a process:
zzufreads options from the command line.zzufwrites fuzzing information to the environmentzuffpreloadslibzzufinto the called process and executes itlibzzufreads fuzzing information from the environmentlibzzufdiverts standard function calls with its own ones- the called process runs normally, but any diverted call goes through
libzzuffirst
Install
git clone https://github.com/samhocevar/zzuf.git cd zzuf ./configure make && make install
Copyright (C) 2004 Sam Hocevar





