Credit: Mickey Jin
A newly disclosed 0-day vulnerability in Parallels Desktop has exposed a root privilege escalation flaw, bypassing the patch for CVE-2024-34331. Independent researcher Mickey Jin (@patch1t) publicly disclosed the exploit after Parallels left the vulnerability unpatched for over seven months, despite multiple responsible disclosure attempts.
The vulnerability lies in the repack_osx_install_app.sh script, which is used to repackage macOS installer applications. The script contains a code signature check to verify that the createinstallmedia binary is Apple-signed. However, Jin discovered two ways to bypass this check:
- TOCTOU Attack: An attacker could replace the createinstallmedia tool with a malicious one after the signature verification but before it is executed with root privileges.
- Weak Signature Verification: The “anchor apple” requirement for signature verification is too weak, allowing an attacker to inject a malicious dynamic library (DYLIB) into an Apple-signed binary to bypass the check.
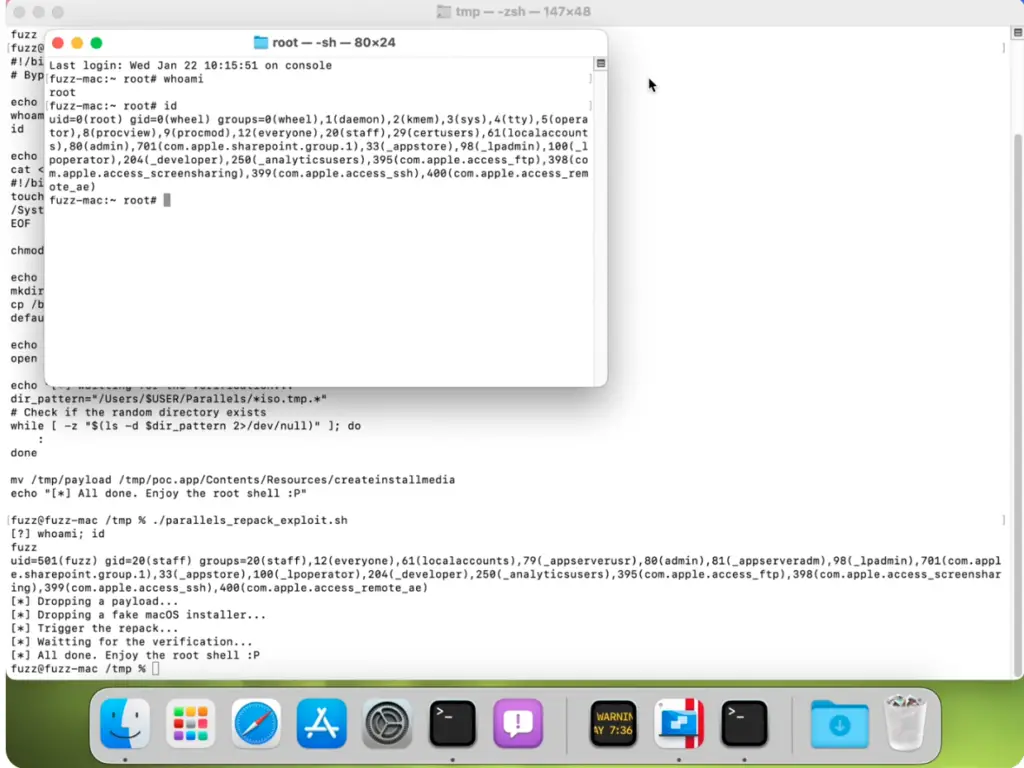
Jin published two proof-of-concept (PoC) exploits demonstrating how attackers could achieve root access:
Exploit 1: Abusing TOCTOU for Privilege Escalation
This exploit manipulates the function do_repack_createinstallmedia by replacing createinstallmedia with a custom payload that executes arbitrary commands with root privileges.
Exploit 2: Abusing do_repack_manual to Overwrite Root-Owned Files
With the introduction of do_repack_manual in Parallels 19.4.1, attackers can now:
- Control the destination path of a repacked macOS image.
- Use symbolic links to redirect root-owned folders.
- Inject a payload into the 7z extraction process, leading to execution with root privileges.
Jin reported the initial bypass to the Zero Day Initiative (ZDI) on May 31, 2024. However, the ZDI’s response was delayed, and they were unable to reproduce the exploit on the latest version at the time. Jin then reported a new issue related to changes in the repack command line to Parallels directly on July 22, 2024. Despite initial acknowledgement, Parallels did not respond to further inquiries.
Jin expressed frustration over the vendor’s continued inaction, stating: “Since the vendor Parallels is playing deaf and dumb, I have to disclose the 0 day exploit now.”
Related Posts:
- macOS Security Compromised: Novel Exploit Bypasses Sandbox Protections
- macOS Vulnerability CVE-2024-54527 Unveiled: TCC Bypass PoC Exploit Code Released
- Apple backports fix for actively exploited 0-day to older macOS and iPhone/iPad devices
- CVE-2024-34331: Parallels Desktop Vulnerability Gives Root to Hackers, PoC Published
- PoC Exploit Released for MacOS SUHelper Root Privilege Escalation