
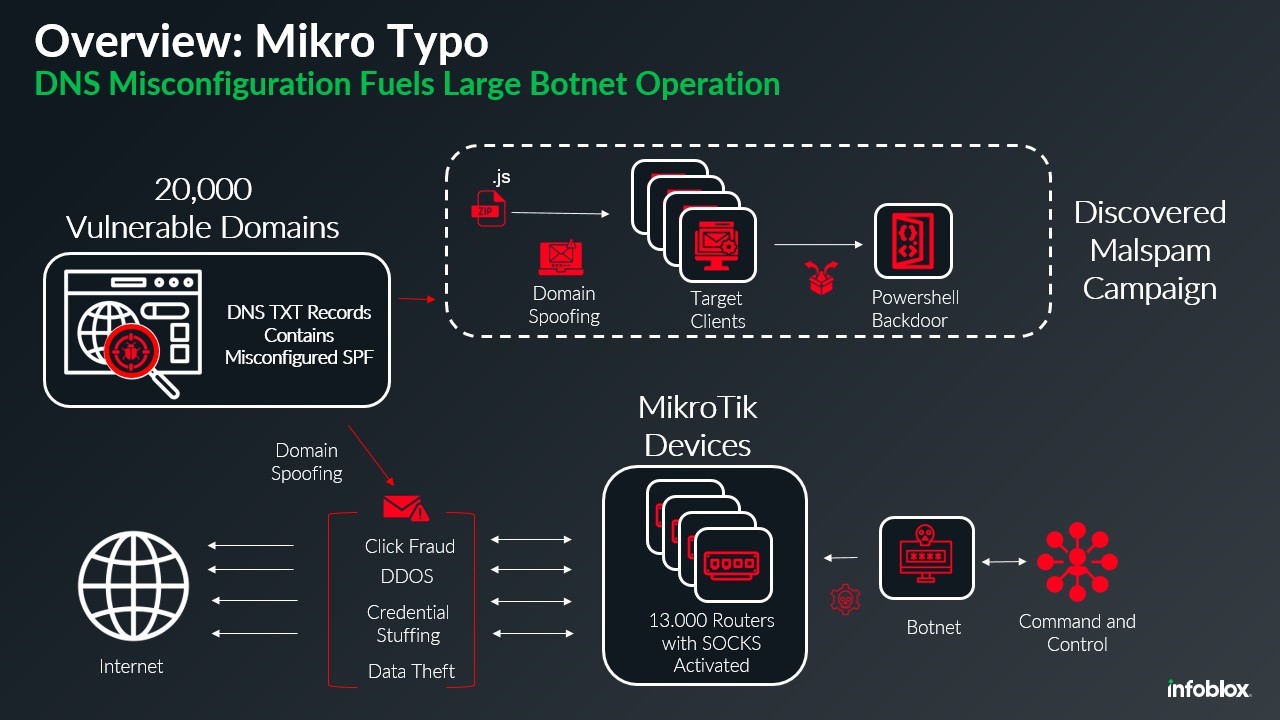
A recent report from Infoblox Threat Intel highlights a sophisticated botnet operation leveraging a simple DNS misconfiguration to distribute malware on a massive scale. This botnet, built on approximately 13,000 compromised MikroTik devices, uses spoofed sender domains and malspam campaigns to deploy trojan malware and potentially conduct other nefarious activities.
According to the report, “This botnet uses a global network of MikroTik routers to send malicious emails that are designed to appear to come from legitimate domains.” The attackers exploit DNS misconfigurations, specifically in Sender Policy Framework (SPF) records, allowing emails from unauthorized servers to pass as legitimate.
Infoblox uncovered that approximately 20,000 sender domains were involved in this operation. A critical factor was the misconfigured SPF records. As Infoblox explains, the SPF information is published in the domain’s DNS records as a TXT record. If misconfigured, it can allow any server to send emails on behalf of the domain.
A correctly configured SPF record looks like this:
v=spf1 include:example.com -all
However, the botnet exploited domains with misconfigurations such as:
v=spf1 include:example.com +all
The inclusion of “+all” effectively permits any server to send emails on behalf of the domain, nullifying SPF protections.
The campaign’s emails typically mimicked shipping companies like DHL, using subject lines referencing invoices or tracking information. The emails contained zip file attachments named with a consistent pattern, such as “Invoice###.zip” or “Tracking###.zip.” Inside these zip files, Infoblox found obfuscated JavaScript files that executed PowerShell scripts, connecting victims to a command-and-control (C2) server hosted on an IP associated with suspicious Russian activity.
MikroTik routers have been a known target for compromise due to vulnerabilities in their firmware. Many of these devices shipped with a hardcoded ‘admin’ account with a blank password, a glaring security flaw. Threat actors exploited these routers to enable SOCKS proxies, effectively transforming the devices into anonymous relays for malicious traffic.
Infoblox states, “Enabling SOCKS effectively turns each device into a proxy, masking the true origin of malicious traffic and making it harder to trace back to the source.” The compromised routers facilitated various attacks, including:
- Malware Delivery: Using proxies to bypass security filters.
- Data Exfiltration: Sending sensitive data to attacker-controlled servers.
- Phishing Campaigns: Amplifying the scale of malicious email campaigns.
The report concludes, “Each compromised device becomes a cog in a much larger, nefarious machine, capable of wreaking havoc on unsuspecting targets.”
Related Posts:
- Infoblox Uncovers Malicious Wave in .US Domain Registrations
- Security experts found MikroTik RouterOS SMB Buffer Overflow flaw
- Critical Vulnerability in Hosted Email Services Exposes Users to Spoofing Attacks
- Exim Vulnerability CVE-2023-42118 Affects Sophos Firewall and SG UTM Customers
- Critical Exim Bug Exposes Email Servers to Remote Attacks