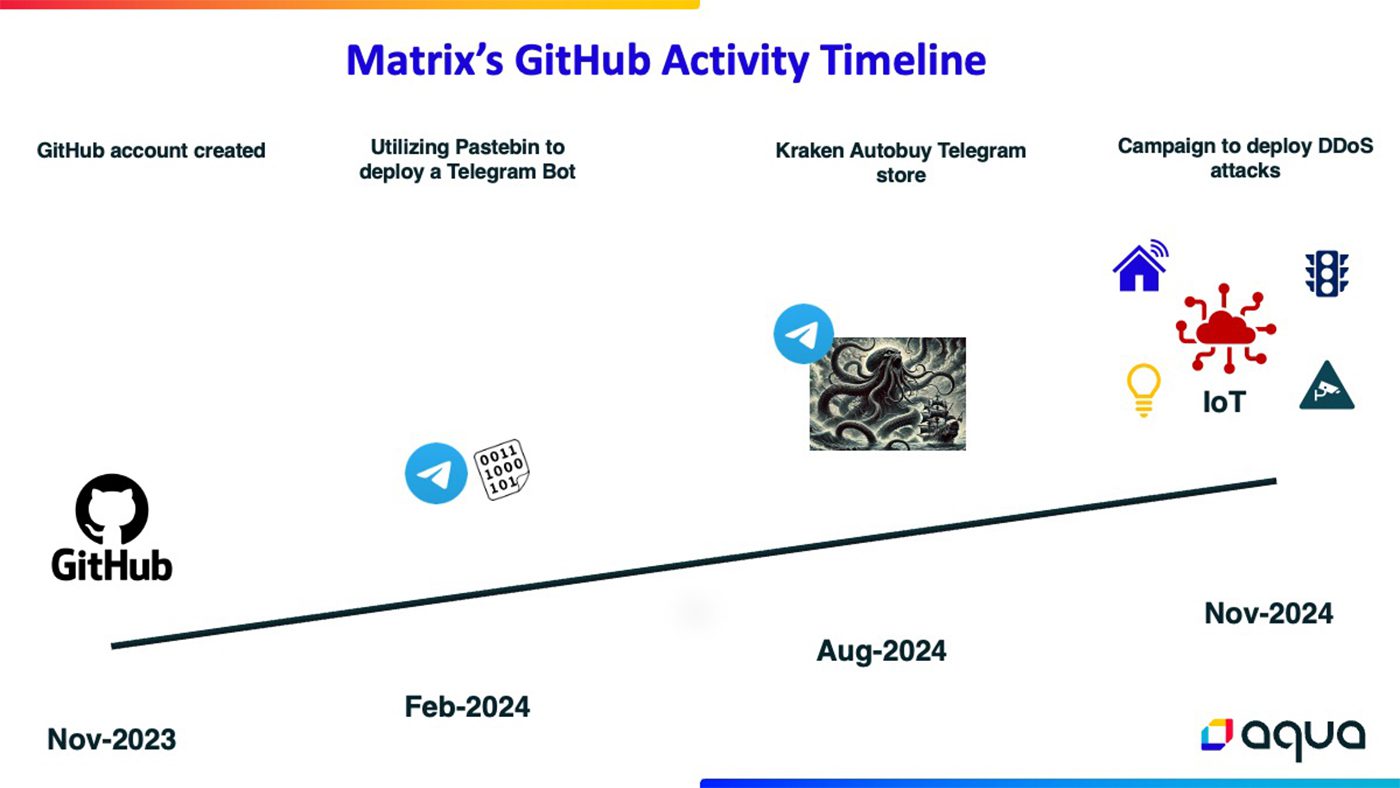
An analysis of Matrix’s activity on GitHub | Image: Aqua Nautilus
Aqua Nautilus researchers have uncovered a major Distributed Denial-of-Service (DDoS) campaign led by a threat actor operating under the name Matrix. This operation, detected through honeypot activities, showcases a concerning evolution in DDoS botnet strategies, with Matrix leveraging accessible tools and exploiting widespread vulnerabilities to launch large-scale cyberattacks.
Matrix exemplifies how even individuals with minimal technical expertise can deploy destructive DDoS operations using publicly available tools. As Aqua Nautilus highlights, “This campaign demonstrates how accessible tools and basic technical knowledge can enable individuals to execute a broad, multi-faceted attack on numerous vulnerabilities.” The campaign focuses on vulnerabilities across IoT devices, routers, telecom equipment, and enterprise systems, creating a botnet capable of significant global disruption.
Matrix employs a variety of initial access techniques, including:
- Router Exploits: Leveraging vulnerabilities such as CVE-2017-18368 (command injection) and CVE-2021-20090 (Arcadyan firmware).
- IoT and DVR Exploits: Exploiting weaknesses in devices like the Hi3520 platform.
- Enterprise Targets: Exploiting vulnerabilities in Apache Hadoop’s YARN and HugeGraph servers to infiltrate corporate systems.
- Credential Abuse: Conducting brute-force attacks using common default credentials (e.g., admin:admin).
These devices are then assimilated into the botnet, significantly amplifying the scale and power of the DDoS attacks.
Matrix’s operation benefits from a sophisticated, albeit heavily borrowed, arsenal of tools:
- Mirai Variants: Targeting IoT devices to execute massive DDoS attacks.
- PyBot and DiscordGo: Python-based frameworks used for botnet management and coordination.
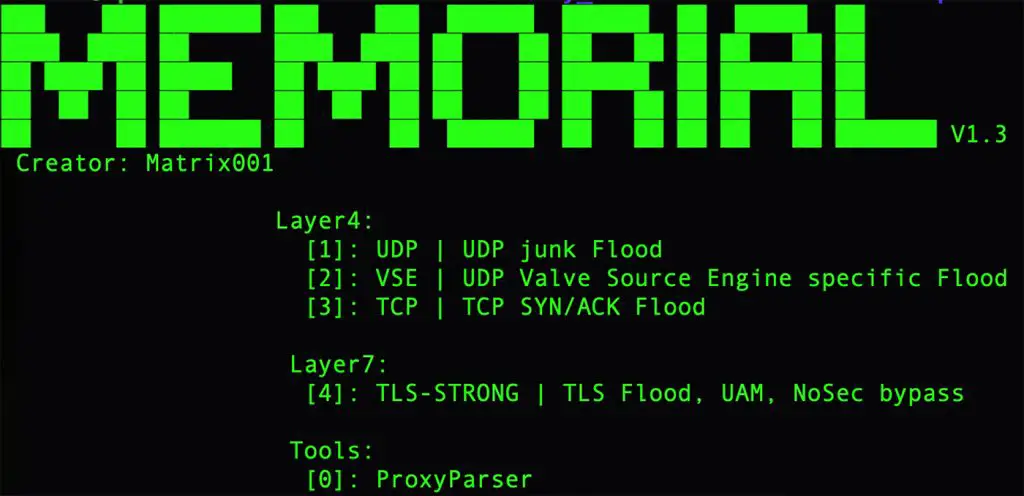
- Telegram-Based Sales: A Telegram bot named Kraken Autobuy facilitates automated DDoS service sales, offering plans for attacks targeting Layer 4 (Transport Layer) and Layer 7 (Application Layer).
Aqua Nautilus researchers observed that, despite the breadth of the campaign, the tools used are largely open-source. “The true skill lies in the ability to integrate and operate these tools effectively,” researchers remarked, underscoring the growing threat posed by script kiddies with access to powerful resources.
The campaign has primarily focused on IoT-rich regions like China and Japan, although its impact spans globally. Interestingly, despite suspected Russian origins, the campaign does not target Russian or Ukrainian assets, suggesting financial motives over political agendas. The potential scope of the botnet is staggering; an analysis revealed nearly 35 million internet-connected devices that could serve as targets, with an estimated botnet size of up to 1.7 million devices if only a fraction are exploited.
The consequences of these attacks extend beyond the immediate DDoS victims. As Aqua Nautilus notes, “If affected servers are part of a cloud vendor’s infrastructure, they might be deactivated by the service provider, leading to a disruption of the victim’s business.”
The Matrix DDoS campaign represents a troubling shift in the cyber threat landscape. By exploiting basic vulnerabilities and leveraging publicly available tools, Matrix has demonstrated the growing accessibility of large-scale cyberattacks. As threat actors continue to innovate and expand their reach, businesses and individuals must remain vigilant, adopting proactive measures to safeguard their systems from compromise.
Related Posts:
- Oracle release Critical Patch Update in several products
- New Attack Vector: Misconfigured Jupyter Servers Targeted for Illegal Streaming
- Openfire Bug (CVE-2023-32315) Exploited to Deploy Kinsing Malware and Cryptominer