ngioweb botnet infection chain | Image: Lumen Technologies
A recent report by Black Lotus Labs at Lumen Technologies has exposed the scale and sophistication of the NSOCKS botnet, a criminal proxy network built on the infamous ngioweb botnet. With a daily average of over 35,000 bots across 180 countries, NSOCKS has become a backbone for malicious activities, including DDoS attacks, phishing, and malware obfuscation. Shockingly, two-thirds of these proxies are based in the U.S., making them a critical threat to global cybersecurity.
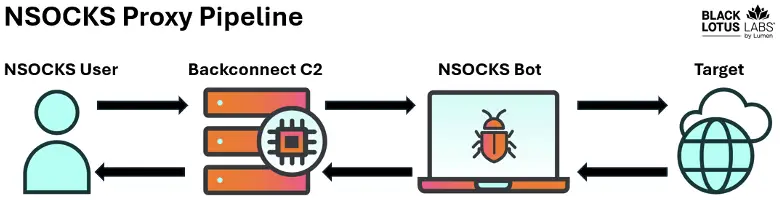
Proxy botnets like NSOCKS provide anonymity for threat actors by routing their malicious traffic through compromised devices. Black Lotus Labs describes it as: “An intricate web allowing users to proxy traffic, obfuscate malware operations, and enable various forms of malicious activity, including credential stuffing and phishing.”
The report highlights how NSOCKS is marketed on underground forums, allowing users to purchase proxy access for 24-hour periods using cryptocurrency. Its user-friendly interface even lets attackers filter proxies by domain types like .gov or .edu, enabling highly targeted attacks.
At least 80% of NSOCKS bots are powered by the ngioweb botnet, which primarily infects SOHO routers and IoT devices. These devices, often outdated or poorly secured, are exploited using n-day vulnerabilities in web application libraries, routers, and security cameras.
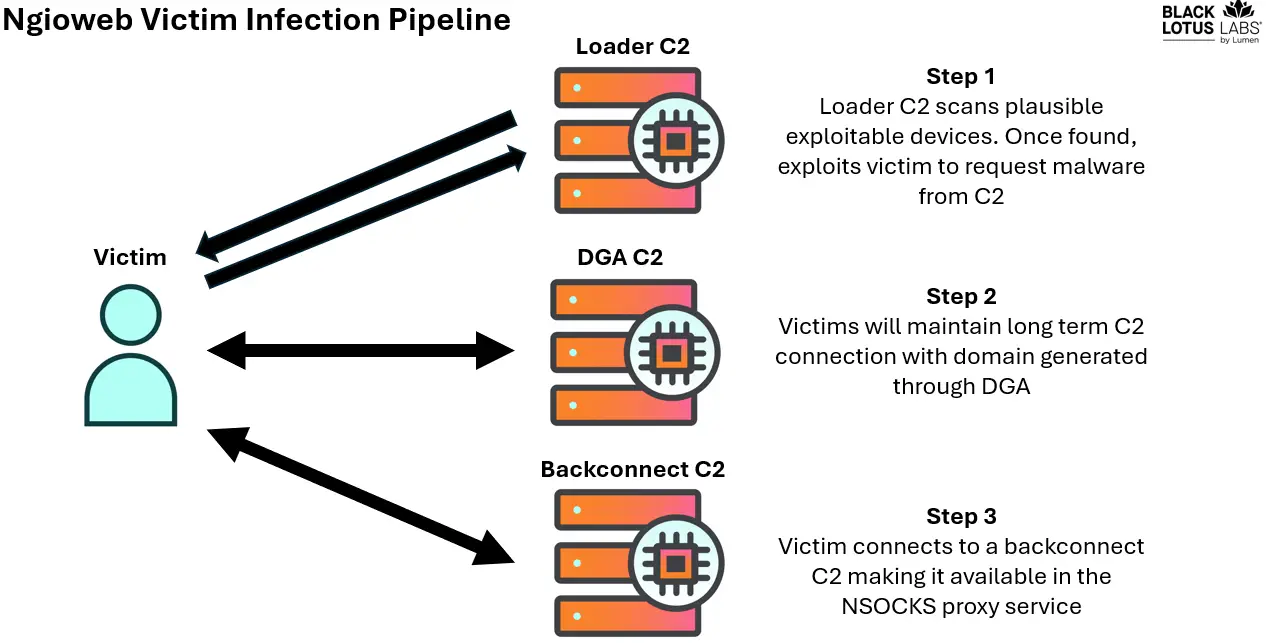
The ngioweb botnet utilizes a multi-stage infection chain:
- Initial Compromise: Devices are infected via exploits, downloading shell scripts to fetch ngioweb malware.
- Loader Nodes: Bots connect to loader command-and-control (C2) nodes for malware updates.
- Backconnect C2s: These nodes assign bots to the NSOCKS proxy network, enabling traffic routing
NSOCKS has emerged as a versatile tool for cybercriminals, with alarming capabilities:
- DDoS Amplification: Open proxies within NSOCKS have been used in recent large-scale DDoS attacks.
- Credential Stuffing: Attackers use the network to bypass geofencing and ASN-based blocking.
- Multi-Group Exploitation: Devices infected with ngioweb malware are often exploited by multiple criminal groups, including the APT group Pawn Storm.
Additionally, NSOCKS’s reliance on a decentralized architecture complicates mitigation. “There exists a group of over 180 backconnect C2s dedicated to the NSOCKS proxy service. These C2s are specifically used to route and proxy traffic, playing a critical role in the operational infrastructure of NSOCKS,” the report notes.
To combat this growing threat, Black Lotus Labs urges organizations and consumers to adopt stricter security measures:
- For Organizations:
- Monitor for suspicious login attempts from residential IP addresses.
- Block known IoCs and enforce strong firewall rules.
- For Consumers:
- Regularly update and reboot SOHO routers.
- Replace devices that are no longer supported by manufacturers
The NSOCKS botnet highlights the evolving complexity of proxy networks in the cybercrime ecosystem. With its global reach and sophisticated architecture, it serves as a reminder of the vulnerabilities in poorly secured IoT devices. As Lumen Technologies concludes: “Botnets such as these present a concerning and persistent threat to legitimate organizations across the internet.”
Related Posts:
- Cybercriminals Exploit Legitimate Windows Tool for Cryptojacking
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs
- Attacker use DDoS attack to hit three major Dutch banks
- GhostLocker 2.0 Unveiled: Evolving Ransomware-as-a-Service Poses Growing Threat