Active Exploits Targeting Apache HugeGraph Flaw (CVE-2024-27348): PoC Code Released
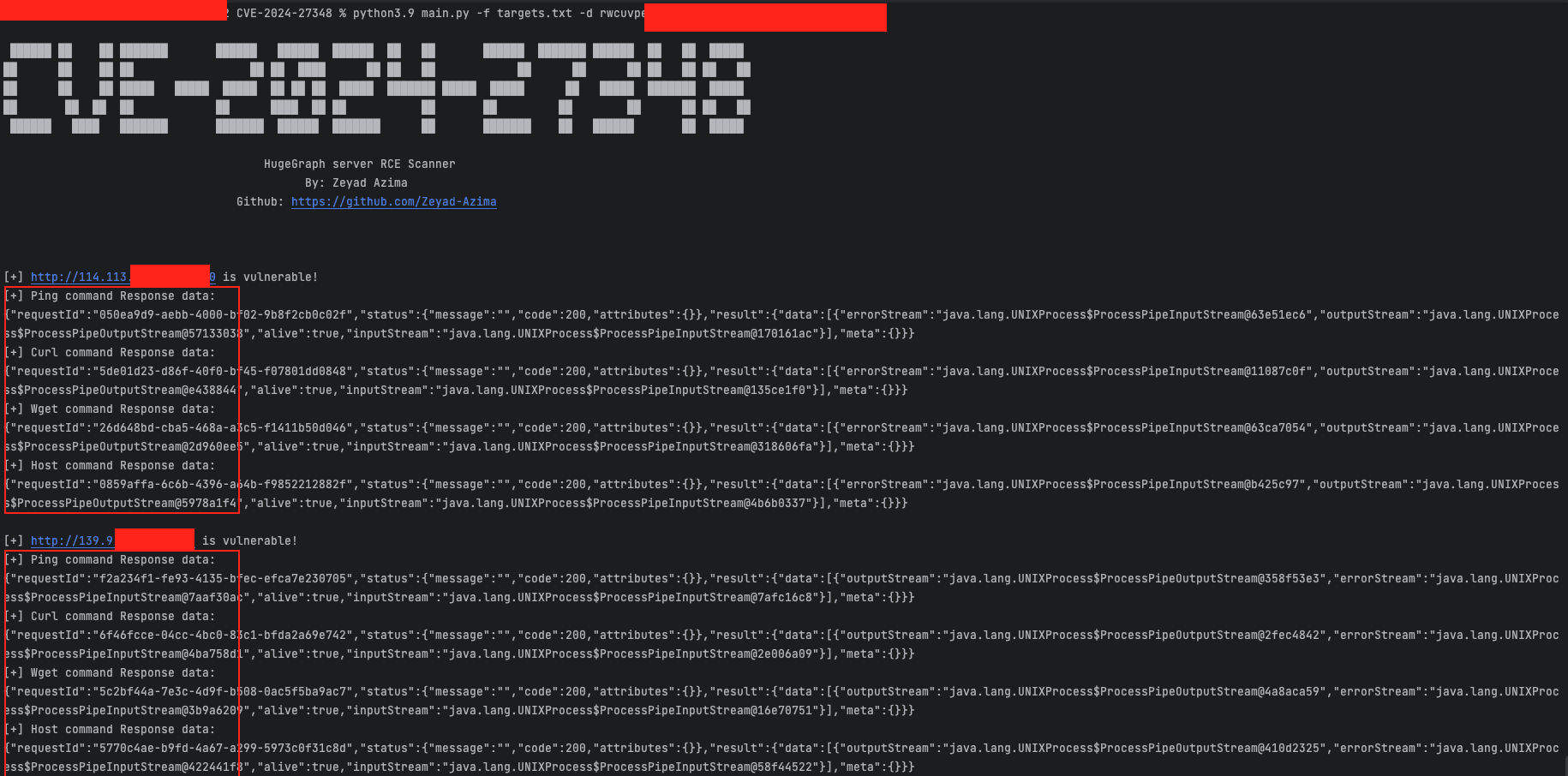
A remote code execution (RCE) vulnerability, tracked as CVE-2024-27348, is currently under active exploitation in the wild, targeting Apache HugeGraph-Server deployments. This discovery comes from the Shadowserver Foundation, a non-profit cybersecurity organization that has detected numerous attack attempts originating from various sources.
The flaw, impacting Apache HugeGraph-Server versions 1.0.0 to 1.2.1 running on Java 8 or Java 11, resides in the graph database’s Gremlin traversal language interface. This interface, designed for user interaction with the graph database, can be manipulated by attackers to bypass security measures and execute arbitrary code on the affected system.
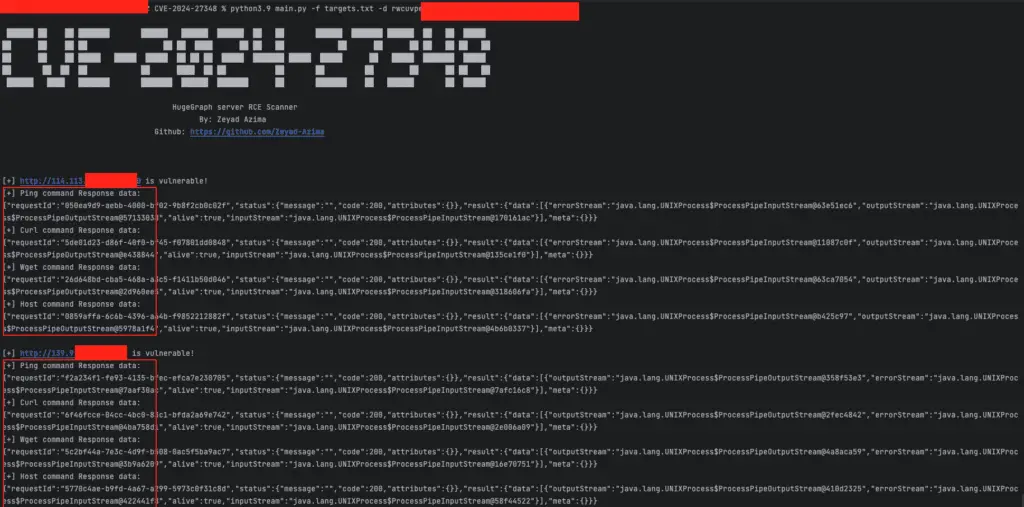
The situation has intensified with the recent release of a proof-of-concept (PoC) exploit code by security researcher Zeyad Azima in June. This Python script further simplifies the exploitation process, enabling malicious actors to easily execute commands on vulnerable servers.
In light of the ongoing attacks and the availability of PoC exploit code, the Apache Software Foundation has issued an urgent advisory, urging users to take immediate action:
-
Upgrade: Update HugeGraph to version 1.3.0 or later, ensuring it runs on Java 11. This upgraded version contains a fix for the vulnerability.
-
Enable Authentication: Activate the built-in authentication system to restrict access to the Gremlin server. This added layer of security can prevent unauthorized access attempts.
-
Whitelist IP Addresses: Utilize the “Whitelist-IP/port” function to limit access to authorized IP addresses and ports, further minimizing the attack surface.





