Image Credit: Rapid7
In the realm of software collaboration tools, Atlassian’s Confluence Data Center and Server instances are titans. PoC exploit code has been released for an actively exploited zero-day vulnerability (CVE-2023-22515) affecting Atlassian Confluence Data Center and Server instances. Notably, the vulnerability score rests at a perilous 10 on the CVSS scale.
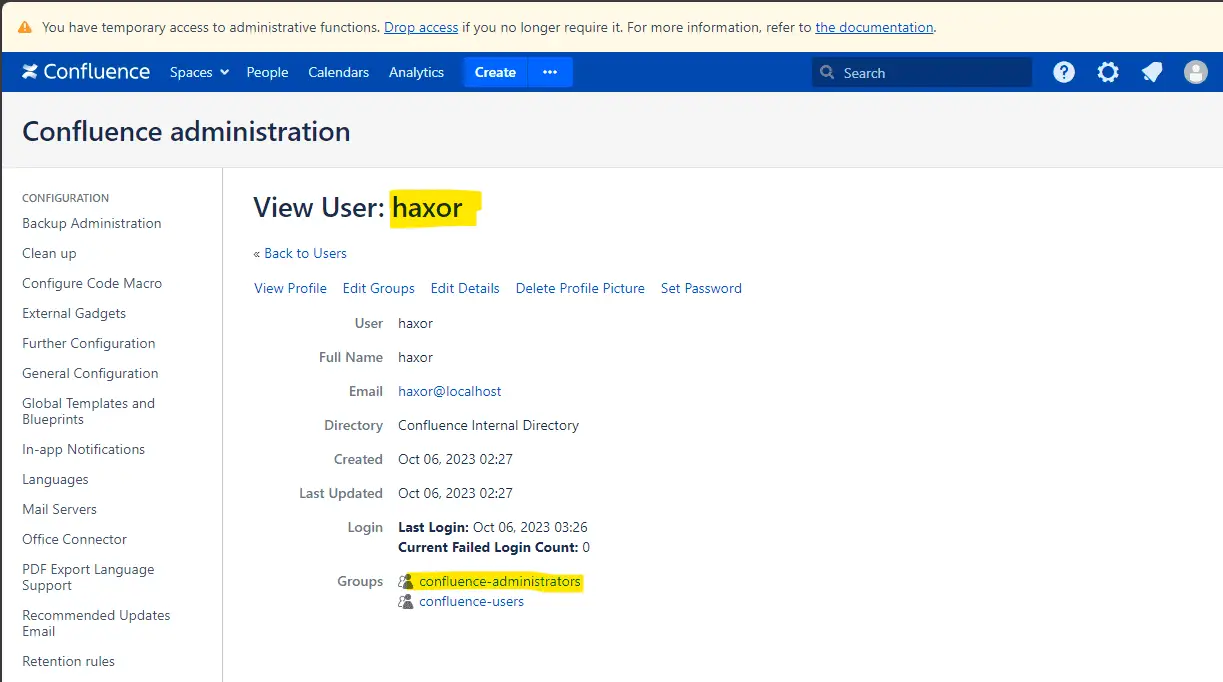
Diving into the specifics, this privilege escalation vulnerability allows rogue entities to craft administrator accounts with impunity. These unauthorized admin accounts then serve as gateways to infiltrate Confluence instances. What makes the situation dire is the ability for the vulnerability to be exploited anonymously, putting on-premise Confluence instances on the public internet under immediate threat. Fortunately, cloud-hosted versions remain unaffected.
For the technically inclined, the crux of the issue revolves around the malicious actor’s capacity to manipulate getter/setter chains on the Action object for unauthenticated endpoints. This manipulation allows the alteration of pivotal properties. The vulnerability’s intricacies were dissected in detail in Rapid7’s recent analysis, explaining how attackers can wield the setup functionality to concoct new administrator users and potentially exploit several other paths.
“The root cause of this vulnerability is the attacker’s ability to perform complex getter/setter chains on the Action object for unauthenticated endpoints, allowing for modification of critical properties. By modifying the setupComplete variable, the attacker was able to leverage the setup functionality to create a new administrator user. However, the attacker is not limited to this, and it is reasonable to assume there are other avenues of exploitation beyond targeting a specific endpoint such as /server-info.action which inherits from ConfluenceActionSupport (as do many other actions), or leveraging the vulnerability to create a new administrator user,” reads the analysis from Rapid7 blog.

The theoretical vulnerability was quickly brought into the realm of reality by security researcher Chocapikk. A proof-of-concept (PoC) exploit code for CVE-2023-22515 was released, which facilitates unauthorized access to Confluence Server and Data Center instances. This script acts as an x-ray into the exploitation procedure, shedding light on the vulnerability’s successful trigger, the genesis of a new admin, and the success rate of such unauthorized entries.
Adding to the alarm is Microsoft’s recent discovery linking the exploitation of this flaw to the enigmatic nation-state actor, Storm-0062—known to some as DarkShadow or Oro0lxy. Active since September 14, 2023, the tech behemoth’s intelligence team has been tracking the nefarious activities of this actor.
Microsoft has observed nation-state threat actor Storm-0062 exploiting CVE-2023-22515 in the wild since September 14, 2023. CVE-2023-22515 was disclosed on October 4, 2023. Storm-0062 is tracked by others as DarkShadow or Oro0lxy.
— Microsoft Threat Intelligence (@MsftSecIntel) October 10, 2023
Atlassian, well aware of the threat’s gravity, has classified this vulnerability as ‘critical.’ In response, patches to remedy the situation have been swiftly released. Yet, with the proof-of-concept out in the wild, and with the knowledge of the nation-state actor’s involvement, organizations utilizing Confluence tools need to spring into action.
It’s paramount for such organizations to migrate to the latest versions of the software, fortifying their defenses against any looming threats. Furthermore, in the interim, it would be prudent to distance these applications from the public internet, ensuring a robust shield is firmly in place.