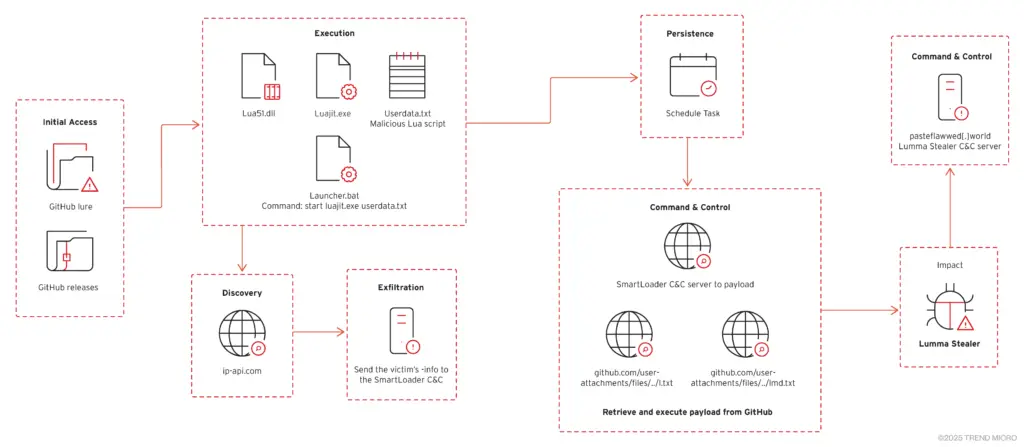
SmartLoader Attack chain | Image: Trend Micro
Trend Micro researchers have uncovered a new campaign that uses AI-generated content to create convincing fake GitHub repositories, distributing malware like SmartLoader and Lumma Stealer. These repositories are disguised as legitimate software, exploiting GitHub’s trusted reputation to deceive users.
The campaign primarily targets users seeking gaming cheats, cracked software, and system tools. Victims are tricked into downloading ZIP files containing obfuscated Lua scripts that, upon execution, deploy SmartLoader and subsequently Lumma Stealer.
“These repositories disguise malware as gaming cheats, cracked software, and system tools to deceive users,” the report states. The malicious actors leverage AI to generate convincing README files and documentation, making the fake repositories appear legitimate and trustworthy.
The campaign has evolved from previous attacks that primarily used GitHub for file hosting. Now, threat actors are creating entire repositories, complete with AI-generated descriptions and hyperlinks that redirect to malicious files.
“Cybercriminals are adapting from using GitHub file attachments to creating entire repositories, incorporating social engineering tactics and AI-assisted deception,” the report highlights. This tactic allows attackers to better exploit GitHub’s trusted reputation and evade detection.
Once a user downloads and extracts the malicious ZIP file, a chain of events is initiated. An obfuscated Lua script is executed, leading to the deployment of SmartLoader, which then delivers the Lumma Stealer payload.
Lumma Stealer is a powerful information stealer capable of gathering sensitive data from web browsers, cryptocurrency wallets, and 2FA extensions. It can steal login credentials, financial information, and other personally identifiable information (PII), putting victims at risk of identity theft and financial fraud.
This campaign demonstrates the increasing sophistication of cybercriminals, who are now using AI to enhance their social engineering tactics and bypass security measures. Trend Micro urges users to be cautious when downloading software from GitHub and other online sources, and to verify the authenticity of repositories before downloading any files.
Related Posts:
- Beyond Firewalls: NCSC Explores Cyber Deception’s Potential
- Lumma Stealer Malware Campaign Targets Educational Institutions with Deceptive PDF Lures
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
- MaaS in Action: How Lumma Stealer Employs Advanced Delivery Techniques
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign