Screenshot of the sample found on the VirusTotal platform
Cybersecurity analysts at Group-IB have uncovered a sophisticated malware campaign targeting bank customers in Central Asia. Dubbed “Ajina.Banker,” this Android malware poses a significant threat to users’ personal and financial data. The campaign, which began in November 2023, continues to wreak havoc across the region and is now expanding its reach beyond Central Asia.
Ajina, a name rooted in Uzbek folklore, refers to a mythical spirit known for its deception and malevolence. Like its namesake, the Ajina malware deceives users by masquerading as legitimate apps, luring unsuspecting individuals into a web of cyberattacks that compromise their devices and sensitive information.
Group-IB’s analysis has identified over 1,400 unique malware samples, all aimed at harvesting users’ banking information and potentially intercepting two-factor authentication (2FA) messages. The malware is cleverly disguised as everyday apps for banking, payments, and deliveries, making it easy for users to fall victim. These malicious applications are primarily distributed via Telegram channels, a favored platform for the campaign’s operators.
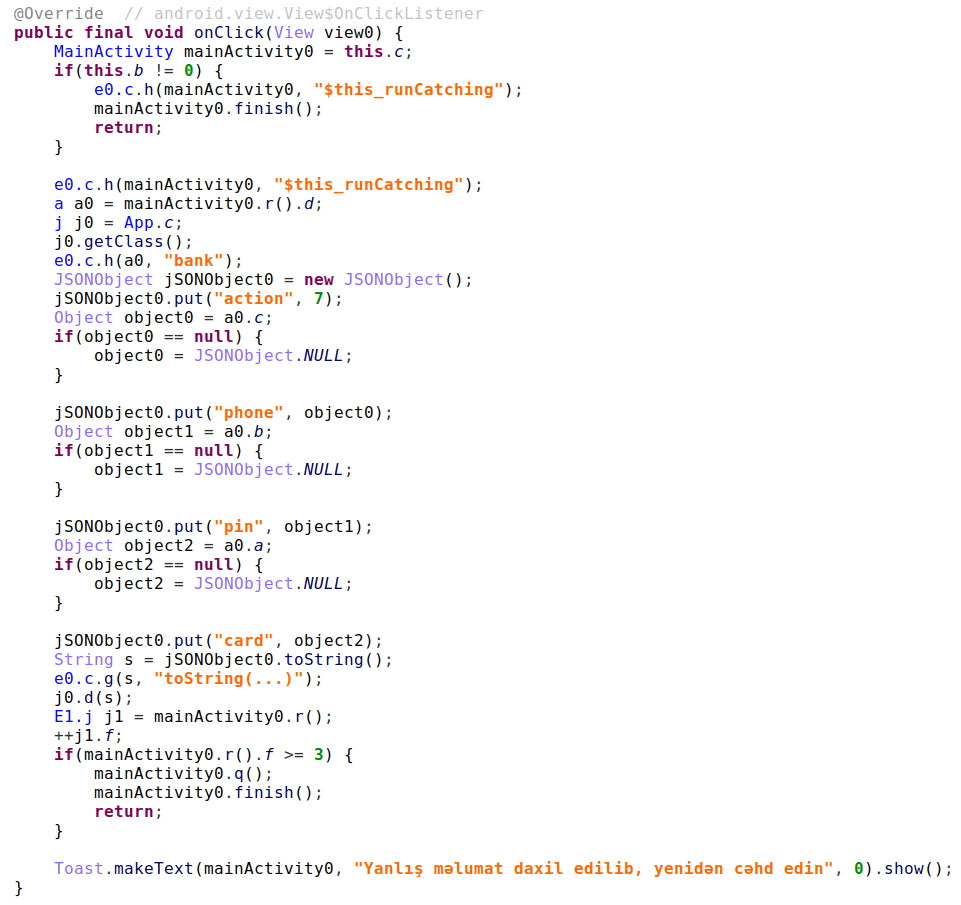
The scale of the Ajina campaign is alarming, with evidence pointing to a highly organized network of affiliates motivated by financial gain. This network utilizes automated tools to distribute malware, increasing the efficiency and scope of the attack. Notably, the campaign has evolved over time, incorporating more sophisticated techniques to ensure its continued success.
The Ajina malware targets users through phishing messages and malicious APK files disguised as trusted local applications. Group-IB’s research indicates a cultural familiarity in the malware’s design, suggesting the attackers have deep knowledge of the region and its digital landscape. Ajina’s malicious files have been tailored to appear as local finance or government apps, enhancing the likelihood of successful infections.
Once the malware infiltrates a device, it collects a range of sensitive data, including SIM card information, SMS messages, and installed banking applications. This data is then transmitted to the attackers’ servers, potentially giving them access to users’ financial accounts.
While initially focused on Central Asia, the Ajina campaign is now expanding into neighboring countries, with reports of infections spreading beyond the region. The use of Telegram channels to distribute malware has allowed the campaign to grow rapidly, exploiting regional community chats to spread malicious content.
Group-IB’s timeline of infections shows a steady increase in victims, underscoring the persistent threat posed by Ajina. The attackers have refined their social engineering tactics, using promotional messages and offers to lure users into downloading infected files.
As the Ajina malware campaign continues to evolve, cybersecurity experts are urging users to exercise caution when downloading applications, especially from unofficial sources like Telegram channels. The deceptive nature of this campaign, combined with its widespread reach, makes it a formidable threat in the region.
Related Posts:
- The Cobalt hacker group is still active, although the leader was arrested
- EstateRansomware Exploits Veeam Vulnerability (CVE-2023-27532) in Sophisticated Attack
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs
- Beyond the Ransom: Inside the Mind of Brain Cipher Ransomware Group
- Hackers exploit CVE-2023-38831 zero-day vulnerability in WinRAR