Akira Goes Stealthy: Ransomware Group Prioritizes Data Theft for Extortion
In the dynamic world of cybersecurity, the Akira ransomware stands out as a formidable adversary. First gaining attention in early 2023, Akira quickly became notorious for its targeted attacks on small to medium-sized businesses across various sectors globally, including government, manufacturing, technology, education, consulting, pharmaceuticals, and telecommunications. According to the Sophos dataset, Akira has primarily targeted organizations located in Europe, North America, and Australia.
Initially known for its encryption-based ransomware attacks, Akira has since shifted towards extortion-only operations. This new tactic involves exfiltrating data without deploying ransomware, thereby avoiding the encryption of systems. This change in strategy indicates a sophisticated and adaptable adversary, focusing on extorting organizations over leaked data.

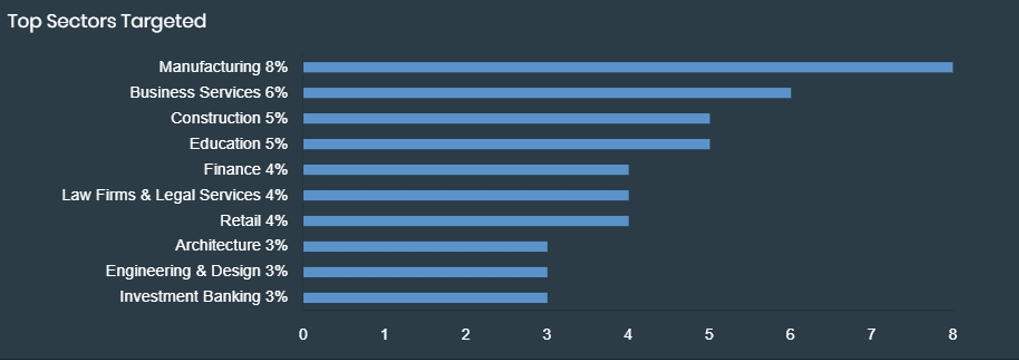
Top industry sectors targeted by Akira per FortiRecon.
Akira’s attack chain is a masterclass in cyber intrusion. The ransomware typically gains initial access through unauthorized VPN logins, exploiting weak points like accounts lacking multi-factor authentication (MFA) or known vulnerabilities in VPN software. Once inside, Akira actors use various methods to obtain credentials, often targeting Cisco VPN products.
The ransomware group is adept at credential access, employing techniques like minidumping the LSASS process memory and leveraging tools to acquire credentials from the Active Directory database. These activities include copying the SYSTEM registry hive and NTDS.dit file for full domain credential compromise.
Akira’s proficiency in evading detection is evident in its consistent attempts to disable endpoint protections and Windows Defender real-time monitoring. The actors use tools like runas for running commands as different users, further complicating tracking efforts for defenders.
Lateral movement within networks is another area where Akira excels. The ransomware actors frequently utilize Remote Desktop Protocol (RDP) with valid administrator accounts to move across environments. They also use SMB and various other tools for lateral movement, indicating a comprehensive understanding of network structures.
For command-and-control operations, Akira actors favor dual-use agents like AnyDesk to establish persistent remote access. This strategy demonstrates their ability to blend in with legitimate network traffic, making detection challenging.
Akira ransomware’s primary goal is data exfiltration. The actors use a variety of tools to exfiltrate sensitive information, adapting their methods based on the target’s network and defenses. In most cases, the ransomware binary is deployed under various names to encrypt multiple machines within target networks. However, the group has recently shown a tendency to focus on exfiltration without encryption, suggesting a strategic shift.
The Akira ransomware group exemplifies the evolving nature of cyber threats. Their ability to adapt tactics, from encryption-based ransomware to data exfiltration and extortion, underscores the need for robust cybersecurity measures. With its focus on credential access and defense evasion, Akira continues to pose a significant challenge in the cybersecurity landscape.