Last week, the Israeli security company CTS-Labs claimed to have discovered the security risks of the AMD Zen architecture processor and chipset. On March 21st, AMD responded to an official blog that all vulnerabilities could be completely repaired in the next few weeks, and not Has any effect on performance. Talk about the “rough process” of CTS-Labs before talking about AMD’s repair operations, because they disclosed to the media less than 24 hours after reporting to AMD, which made AMD very unprepared. This is indeed not authentic. After all, the industry The consensus is 90 days.
 AMD first emphasized that the related loopholes did not involve the “fuse” and “ghost” that had raged in the previous stage. Second, there is a security risk in the firmware of the embedded security control chip (32-bit Cortex-A5 architecture) and some of the chipsets (AM4, TR4, etc.) on which this module is installed. This is not the Zen architecture itself.
AMD first emphasized that the related loopholes did not involve the “fuse” and “ghost” that had raged in the previous stage. Second, there is a security risk in the firmware of the embedded security control chip (32-bit Cortex-A5 architecture) and some of the chipsets (AM4, TR4, etc.) on which this module is installed. This is not the Zen architecture itself.
Finally, mastering vulnerabilities and implementing attacks require full administrator privileges and the threshold is still high.
 CTS just released the flaws demo.
CTS just released the flaws demo.
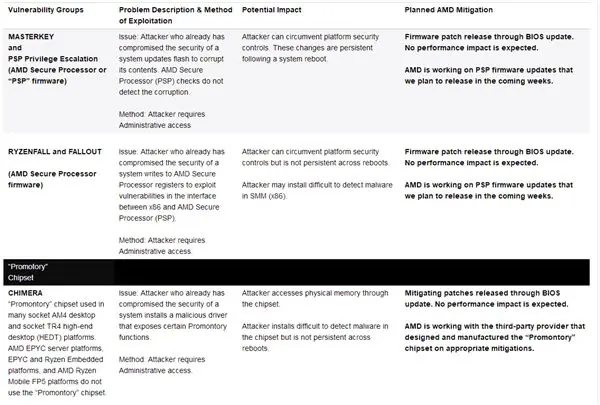
AMD initially divided the vulnerabilities into three categories: “Masterkey,” “RyzenFall/Fallout,” and “Chimera.” The first two involve security chips, while the latter involves chipsets.
As a solution, “Masterkey” and “RyzenFall/Fallout” can be completely immune to the PSP firmware upgrade through BIOS update and will be released in the next few weeks.
“Chimera” can also be solved through BIOS update, and AMD is working closely with “Promontory” outsourcer.
Source: TechSpot