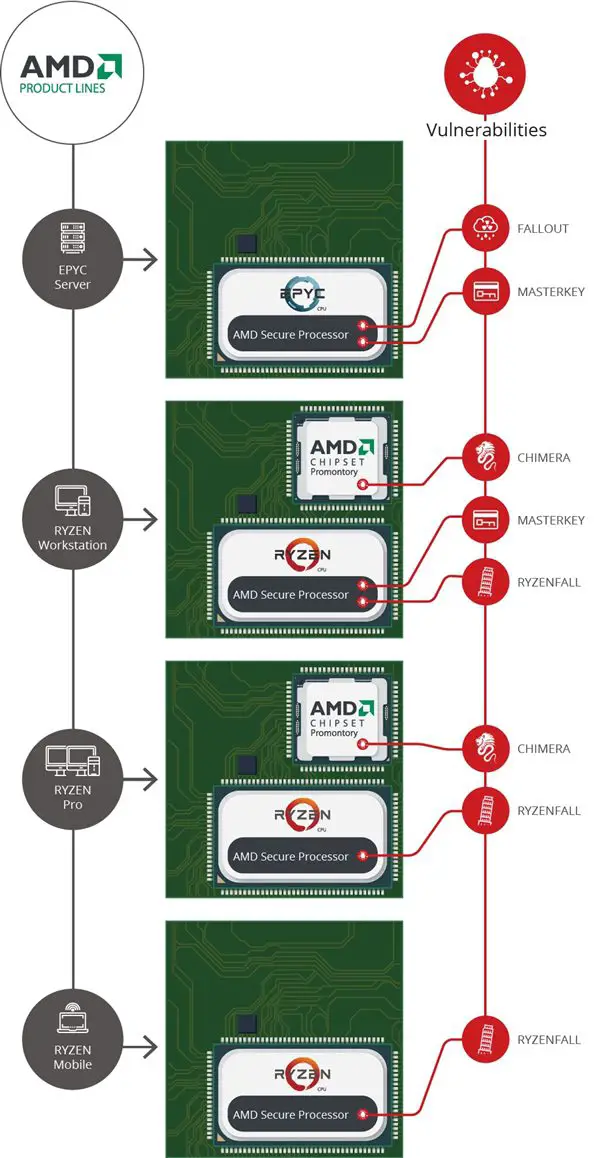
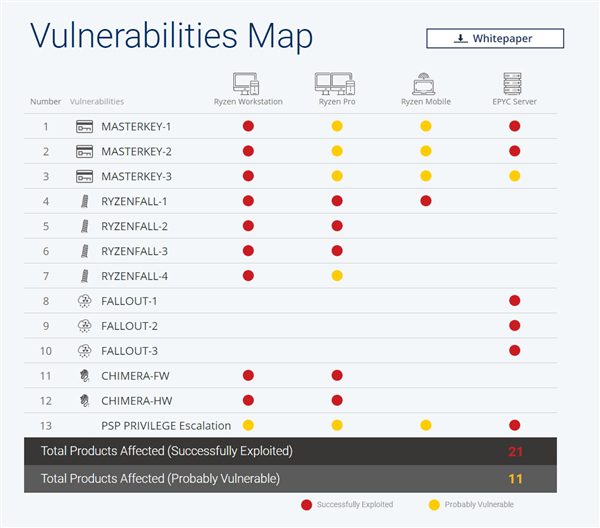
These vulnerabilities affect AMD Ryzen desktop processor, Ryzen Pro enterprise processor, Ryzen mobile processor, and EPYC data center processor. The EPYC data center processor has different platforms for different vulnerabilities. 21 of them have been successfully used, and 11 of them have been exploited.
The use of these vulnerabilities can cause many serious harms to the AMD Zen platform, including controlling the Ryzen/EPYC security processor, controlling the Ryzen motherboard, infecting AMD processors with malware, stealing corporate network sensitive information, bypassing almost all terminal security software, Causes physical damage to the hardware.

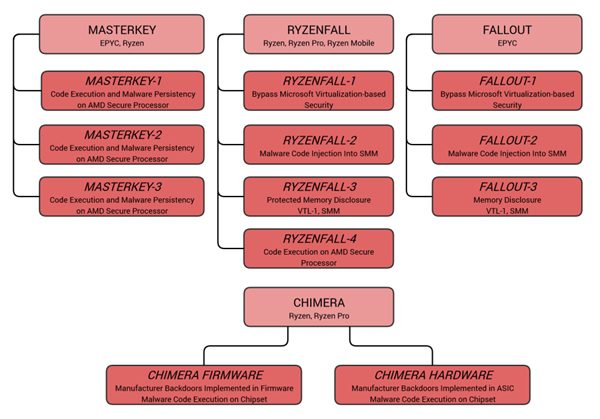
These vulnerabilities fall into four categories:
- Masterkey
It includes three loopholes that affect the entire Zen architecture product. It exists in the Secure Boot function and can modify the system BIOS with a special Ring 0 privilege level software to bypass the security check. The reason for this vulnerability is that the AMD Zen-architecture-integrated security processor (a 32-bit Cortex-A5 architecture module) does not use its own separate physical memory space, but rather shares system memory. - Ryzenfall
Including four vulnerabilities, the full range of Ryzen is affected, as is the Zen security processor, which can lead to the disclosure of public and private keys and execute at the chip level due to defects in the design of security processors and integrated memory controllers.
In addition, the vulnerabilities can bypass Windows Defender Credentials Guard, which is used to save and authenticate passwords, as well as other security features, and can even be used to spread to other computers. - Fallout
There are three vulnerabilities that can open up the virtual machine and host. The attack object is the server -level EPYC. - Chimera
Including two vulnerabilities, not for the processor, but the supporting 300 series chipset. Researchers have found that a keylogger can be inserted into the chipset through the network and then through the motherboard BIOS because it is stored in an 8-pin serial ROM connected to the chipset.
Researchers have published white papers on related vulnerabilities, but they hide technical details for protection purposes and also provide solutions. AMD has 90 days to repair them.