Image: GRIT
A new wave of highly targeted cyberattacks is sweeping across the US, and it’s not your average phishing scam. The GuidePoint Research and Intelligence Team (GRIT) has uncovered a sophisticated campaign leveraging native English-speaking social engineers to trick employees into handing over their VPN credentials. Over 130 organizations have already been targeted, and the threat actors are showing no signs of slowing down.
The GRIT team’s investigation reveals that this ongoing campaign is driven by a financially motivated threat actor with a deep understanding of social engineering and intrusion techniques. What sets this campaign apart is the threat actor’s ability to operate largely outside the visibility of conventional security tools, making detection and prevention a significant challenge.
The attack begins with the targeting of individual users within an organization, using sophisticated social engineering methods to harvest credentials and one-time passcodes. The threat actor typically initiates contact via direct phone calls to users’ cell phones, posing as a member of the organization’s IT or help desk team. The attacker claims to be addressing a VPN login issue and subsequently sends the user a malicious link via SMS, which leads to a fake VPN login page.
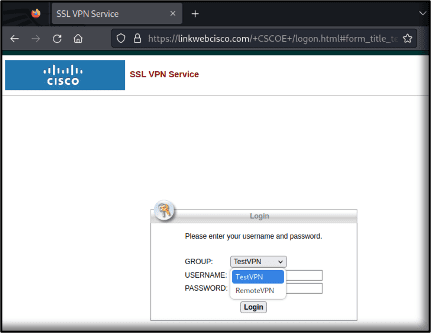
One of the most insidious aspects of this campaign is the creation of custom VPN login pages that closely mimic the legitimate ones used by the targeted organizations. The fake pages even include details such as VPN groups, some of which are added by the attackers—like “TestVPN” or “RemoteVPN”—to further deceive users.
When a user attempts to log in via the fake page, their username, password, and token (if multifactor authentication is in place) are captured by the threat actor. In cases where MFA uses a push notification, the attacker instructs the user to approve the notification during the call, thereby gaining full access to the user’s credentials.
GRIT’s research uncovered several domain names registered by the threat actor that are designed to closely resemble those of well-known VPN technologies, further enhancing the legitimacy of the social engineering attempts. These domains include:
-
ciscoweblink.com
-
ciscolinkweb.com
-
ciscolinkacc.com
-
ciscoacclink.com
-
linkciscoweb.com
-
fortivpnlink.com
-
vpnpaloalto.com
-
linkwebcisco.com
These domains are used to host fake VPN login pages, tricking users into believing they are accessing a legitimate service when, in fact, they are handing over their credentials to cybercriminals.
Once the threat actor successfully gains access to an organization’s network via the compromised VPN credentials, the attack rapidly escalates. The attacker begins scanning the network to identify potential targets for lateral movement, establishing persistence, and escalating privileges. The ultimate goal is to steal sensitive data, destroy backups, and deploy ransomware, which can cripple an organization’s operations and lead to significant financial losses.
Given the sophisticated nature of this campaign, GRIT recommends immediate action to mitigate the risk:
- Audit VPN Activity: Organizations should review VPN logs for any suspicious activity from the past 30 days. If any signs of compromise are detected, an immediate incident response should be initiated to investigate and contain the threat.
- Educate Users: It is critical to inform employees about this specific type of social engineering attack. Users should be instructed to report any unsolicited calls or messages claiming to be from the IT or help desk teams, especially if they involve requests to approve MFA notifications or provide login credentials.
Related Posts:
- GRIT Report 2023: Unpacking the Surge in Ransomware Attacks
- ToddyCat’s Stealthy Assault: Asian Nations in the Crosshairs
- Evolving Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters