EXIST (EXternal Information aggregation System against cyber Threat)
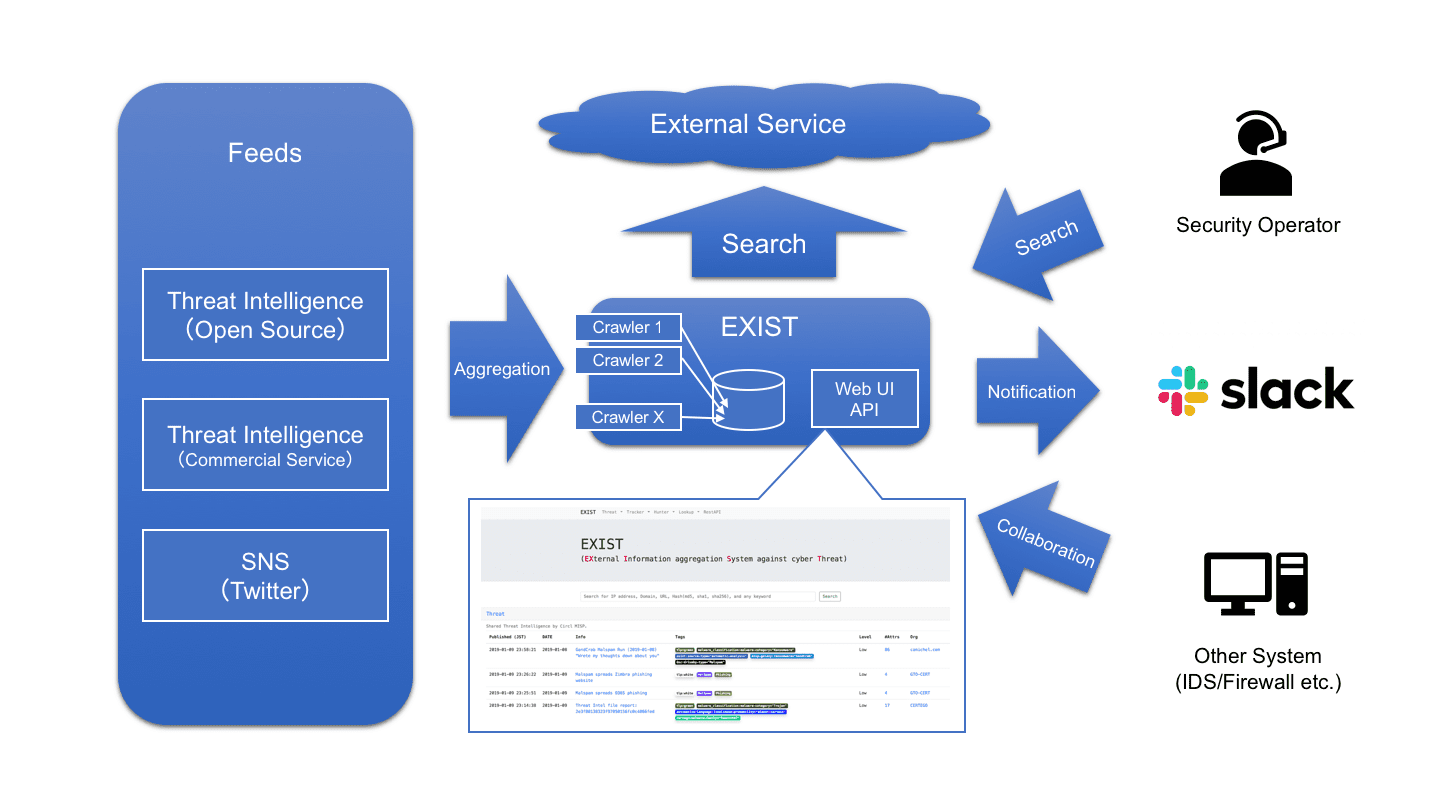
EXIST is a web application for aggregating and analyzing CTI (cyber threat intelligence).
EXIST is written by the following software.
- Python 3.5.1
- Django 1.11.20
EXIST is a web application for aggregating CTI to help security operators investigate incidents based on related indicators.
EXIST automatically fetches data from several CTI services and Twitter via their APIs and feeds. You can cross-search indicators via the web interface and the API.
If you have servers logging network behaviors of clients (e.g., logs of DNS and HTTP proxy servers, etc.), you will be able to analyze the logs by correlating with data on EXIST. If you implement some programs by using the API, you will realize an automated CTI-driven security operation center.
Use Cases
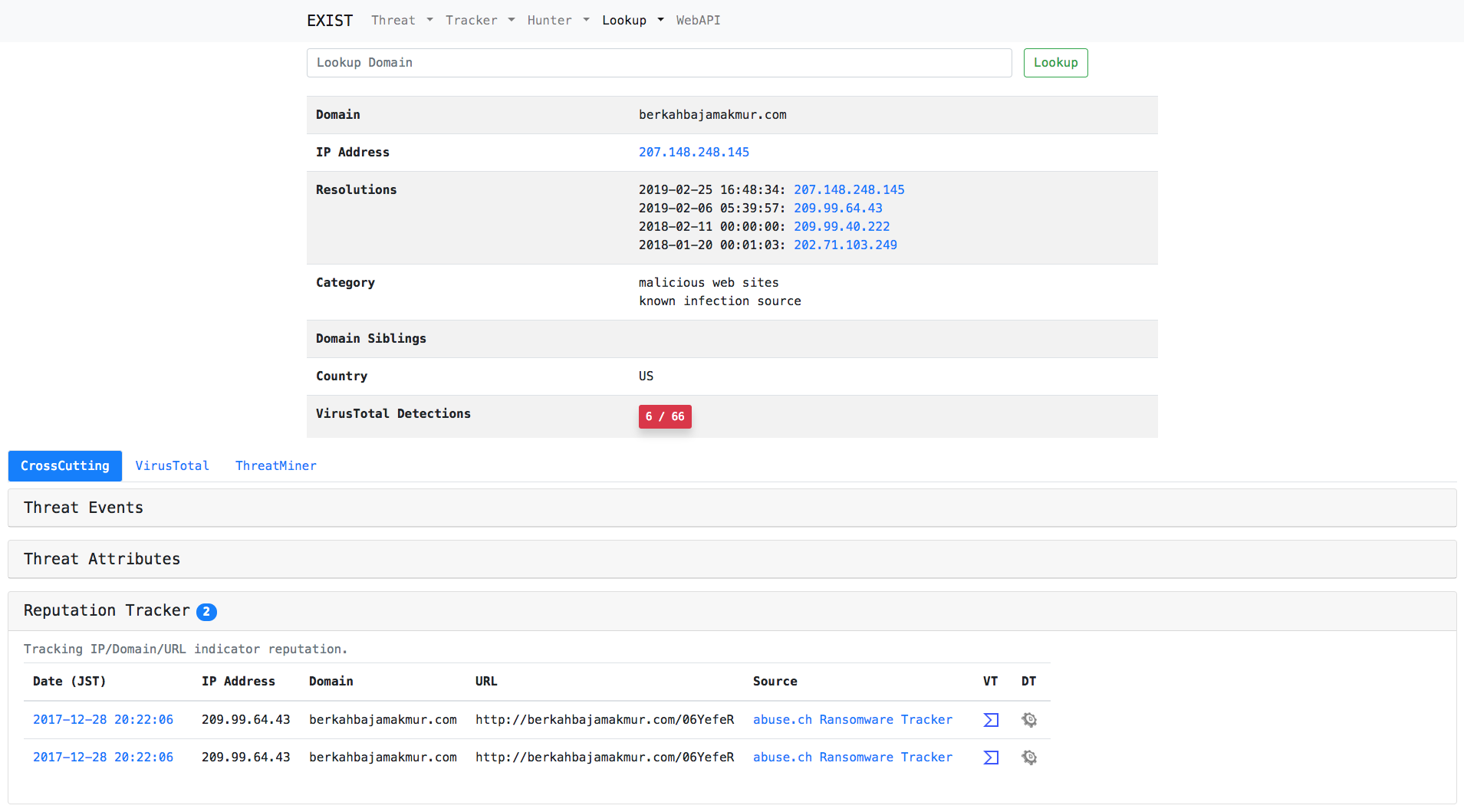
Case1: Investigate domain detected by IDS
Just type a domain in the search form.
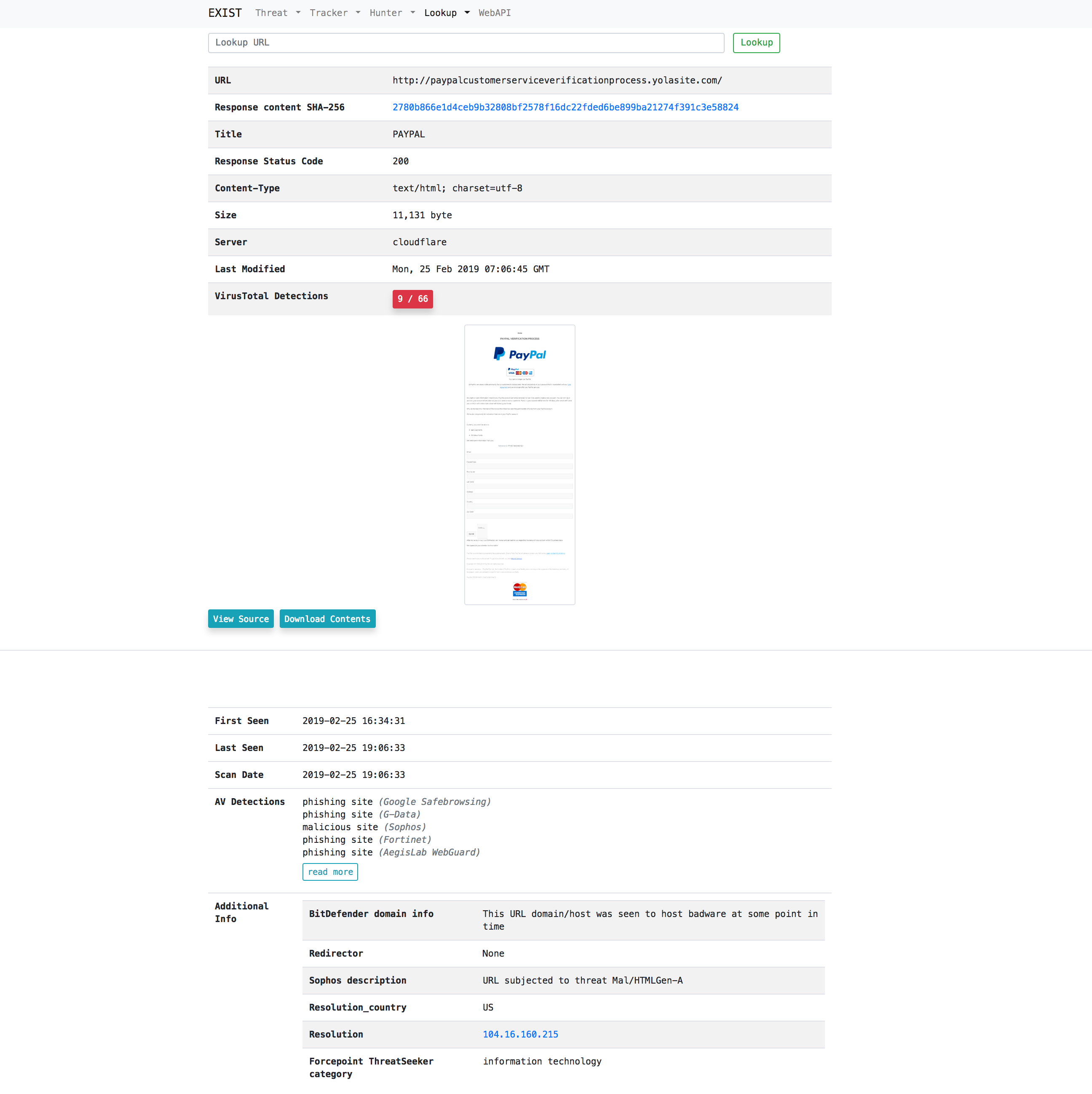
Case2: Access the malicious URL on behalf of the user and acquire the display image of the browser and the contents to be downloaded
Just type url in the search form.
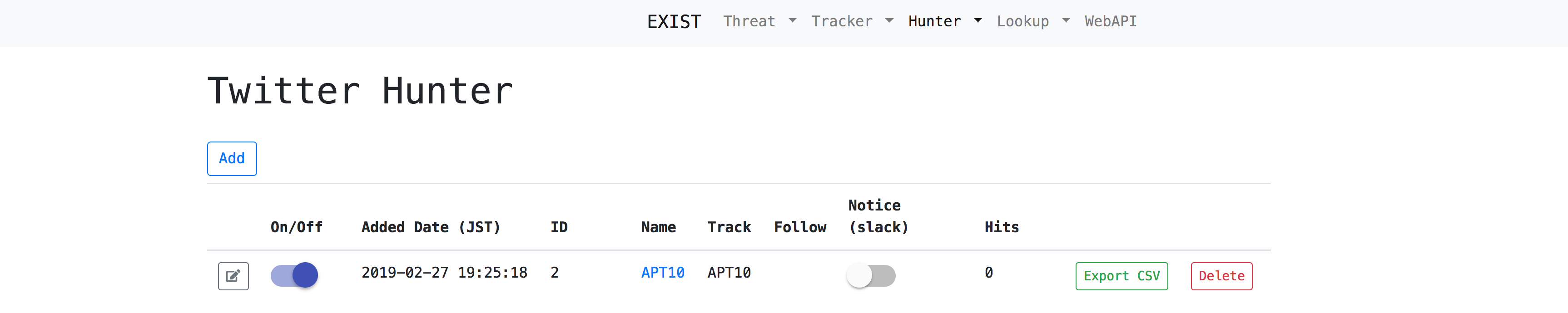
Case3: Monitor cyber threats
Just add keywords in the Threat Hunter or Twitter Hunter.
Features
Tracker
Tracker automatically collects data feeds from several CTI services.
- Threat Tracker
- Reputation Tracker
- Twitter Tracker
- Exploit Tracker
Hunter
Hunter enables us to set queries for gathering data from several CTI services and Twitter.
- Twitter Hunter
- Threat Hunter
Lookup
Lookup retrieves information related to specific information (e.g. IP address, domain) from several internet services (e.g. whois).
- IP Address
- Domain
- URL
- File Hash
Web API
Provide data stored in the EXIST database by Web API.
- reputation
- exploit
- threatEvent
- threatAttribute
Install && Use
Copyright (c) 2019 Cybersecurity Laboratory, NICT