Android Arsenal – Static Analysis Tools

- AmandroidAmandroid is a static analysis framework for Android apps.The Android platform is immensely popular. However, malicious or vulnerable applications have been reported to cause several security problems. Currently, there is no effective method that a market operator can use to vet apps entering a market (e.g., Google Play).Prior works using static analysis to address Android app security problems more focus on specific problems and built specialized tools for them. We observe that a large portion of those security issues can be resolved by addressing one underlying core problem – capturing semantic behaviors of the app such as object points-to and control-/data-flow information. Thus, we designed a new approach to conducting static analysis for vetting Android apps, and built a generic framework, called Amandroid, which does flow- and context-sensitive data flow analysis in an inter-component way.Our approach shows that a comprehensive (tracking all objects) static analysis method on Android apps is totally feasible in terms of computation resources, and the Amandroid framework is flexible and easy to be extended for many types of specialized security analyses.
Since Amandroid directly handles Inter-component control and data flow, it can be used to address security problems that result from interactions among multiple components from either the same or different apps. Amandroid analysis is sound in that it can provide assurance of the absence of the specified security problems in an app with well-specified and reasonable assumptions on the Android runtime and its library.
On top of Amandroid we performed certain specific security analyses, for instance, a) user password flow tracking, b) intent injection detection, and c) crypto API misuse checking. We apply those analyses on hundreds of apps collected from Google Play’s popular apps and a third-party security company, and the results show that it is capable of finding real security issues and efficient enough in terms of analysis time.
- Androwarn
Androwarn is a tool whose main aim is to detect and warn the user about potential malicious behaviors developed by an Android application.The detection is performed with the static analysis of the application’s Dalvik bytecode, represented as Smali.This analysis leads to the generation of a report, according to a technical detail level chosen from the user. - APKInspector
A powerful GUI tool for analysts to analyze Android applications. - Droid-hunter
 Android application vulnerability analysis and Android pentest tool
Android application vulnerability analysis and Android pentest tool
A. Support
> App info check
> Baksmaling android app
> Decompile android app
> Extract class file
> Extract java code
> Pattern base Information Leakage - Error-Prone
Error-Prone is a static analysis tool for Java that catches common programming mistakes at compile-time. - FindBugs + FindSecurityBugs
FindSecurityBugs is an extension of FindBugs, including Java application security rules. It will find the encryption problem and the specific problems of Android. - Lint
 Android Studio provides a code scanning tool called lint that can help you to identify and correct problems with the structural quality of your code without your having to execute the app or write test cases. Each problem detected by the tool is reported with a description message and a severity level so that you can quickly prioritize the critical improvements that need to be made. Also, you can lower the severity level of a problem to ignore issues that are not relevant to your project, or raise the severity level to highlight specific problems.The lint tool checks your Android project source files for potential bugs and optimization improvements for correctness, security, performance, usability, accessibility, and internationalization. When using Android Studio, configured lint and IDE inspections run whenever you build your app. However, you can manually run inspections or run lint from the command line.
Android Studio provides a code scanning tool called lint that can help you to identify and correct problems with the structural quality of your code without your having to execute the app or write test cases. Each problem detected by the tool is reported with a description message and a severity level so that you can quickly prioritize the critical improvements that need to be made. Also, you can lower the severity level of a problem to ignore issues that are not relevant to your project, or raise the severity level to highlight specific problems.The lint tool checks your Android project source files for potential bugs and optimization improvements for correctness, security, performance, usability, accessibility, and internationalization. When using Android Studio, configured lint and IDE inspections run whenever you build your app. However, you can manually run inspections or run lint from the command line. - Smali CFGs
- The SPARTA
The SPARTA project (Static Program Analysis for Reliable Trusted Apps) is building a toolset to verify the security of mobile phone applications.SPARTA is a research project funded by the DARPA Automated Program Analysis for Cybersecurity (APAC) program. SPARTA aims to detect certain types of malware in Android applications or to verify that the app contains no such malware. SPARTA’s verification approach is type-checking: the developer states a security property, annotates the source code with type qualifiers that express that security property, then runs a pluggable type-checker to verify that the type qualifiers are right (and thus that the program satisfies the security property).In addition to type-checking, SPARTA also provides tools to aid in the manual identification of malware in the source code. These tools include a tool to show what permissions are needed for each API call used and a tool to report the use of suspicious APIs. - Thresher
Thresher is a static analysis tool that specializes in checking heap reachability properties. Its secret sauce is using a coarse up-front points-to analysis to focus a precise symbolic analysis on the alarms reported by the points-to analysis. See our PLDI ’13 paper for more details.
 Android application vulnerability analysis and Android pentest tool
Android application vulnerability analysis and Android pentest tool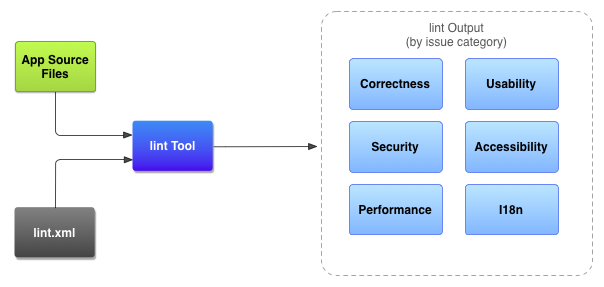 Android Studio provides a code scanning tool called lint that can help you to identify and correct problems with the structural quality of your code without your having to execute the app or write test cases. Each problem detected by the tool is reported with a description message and a severity level so that you can quickly prioritize the critical improvements that need to be made. Also, you can lower the severity level of a problem to ignore issues that are not relevant to your project, or raise the severity level to highlight specific problems.The lint tool checks your Android project source files for potential bugs and optimization improvements for correctness, security, performance, usability, accessibility, and internationalization. When using Android Studio, configured lint and IDE inspections run whenever you build your app. However, you can
Android Studio provides a code scanning tool called lint that can help you to identify and correct problems with the structural quality of your code without your having to execute the app or write test cases. Each problem detected by the tool is reported with a description message and a severity level so that you can quickly prioritize the critical improvements that need to be made. Also, you can lower the severity level of a problem to ignore issues that are not relevant to your project, or raise the severity level to highlight specific problems.The lint tool checks your Android project source files for potential bugs and optimization improvements for correctness, security, performance, usability, accessibility, and internationalization. When using Android Studio, configured lint and IDE inspections run whenever you build your app. However, you can 




