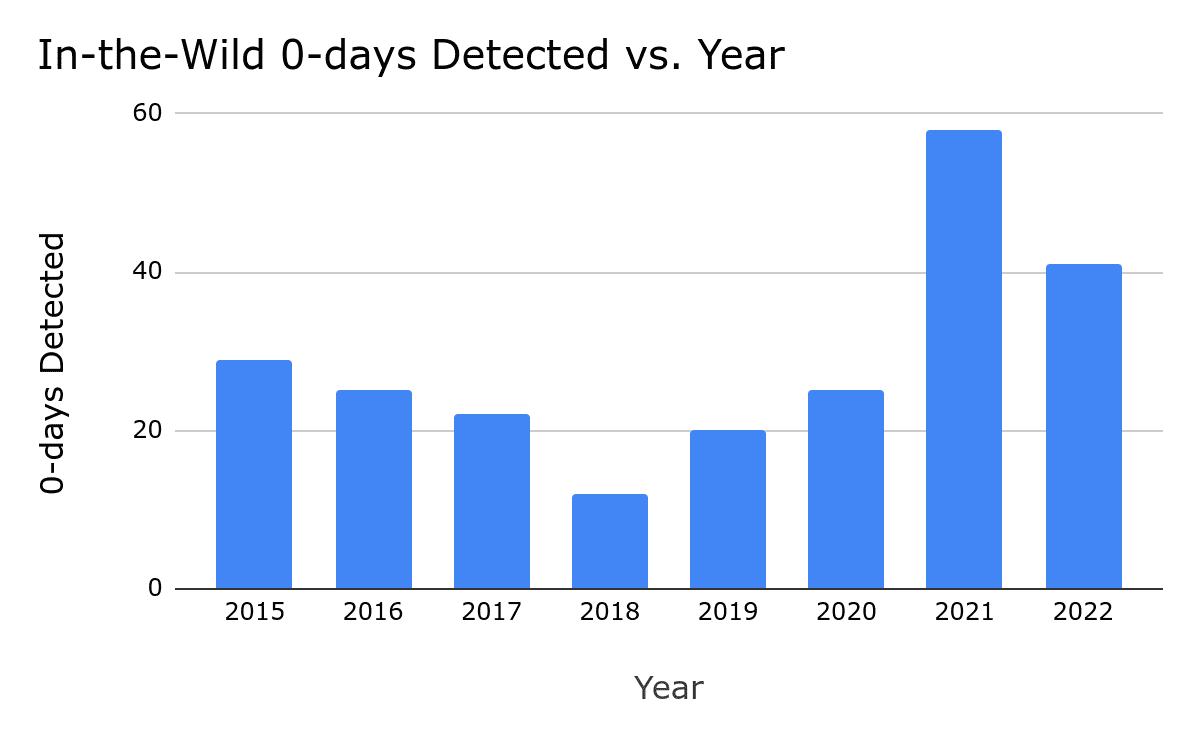
Google’s security team recently published a year review of 0-day vulnerabilities exploited in 2022. These reports are not intended to delve into each individual vulnerability, but rather to examine the year as a whole, identifying trends, gaps, experiences, lessons, and areas of success.
In this report, Google highlights industry-wide concerns: although vulnerabilities can be discovered and fixed relatively quickly, the delivery of these patches to user devices often requires a considerable amount of time.
To illustrate, consider an ecommerce app exploiting an Android system vulnerability to gain escalated privileges, transforming user devices into botnets. The exploited vulnerability was patched two months prior, yet the majority of Android devices have not received this update, allowing the ecommerce app to potentially launch another attack.

The report states that the extended time for Android patches to reach user devices compromises Android’s security.
Here are key points extracted from the report:
1. Due to the elongated patch times, N-day vulnerabilities function similarly to 0-day on Android: Google posits that within the Android ecosystem, users may be unable to receive patches for extended periods. Attackers don’t require 0-day vulnerabilities, they can leverage N-day vulnerabilities, acting as 0-day. The term N-day refers to the interval from when a patch is released to when it is actually installed by the user. Because end-users can’t promptly receive patches, this window of time can be exploited by attackers.
2. Zero-click exploits and new browser mitigation measures can reduce browser 0-days: Many attackers have shifted towards zero-click vulnerabilities, which require no user action to execute an attack, typically targeting components outside of the browser. Most major browsers have implemented new defensive measures, rendering exploits more challenging. This could potentially drive attackers toward other surfaces.
3. Over 40% of 0day vulnerabilities are variants of previously reported vulnerabilities: Of the 41 vulnerabilities reported in 2022 that have been exploited in the wild, 17 are variants of previously reported vulnerabilities. This is a continuation of the worrying trend identified in the 2020 report and the mid-2022 report, suggesting that we may see an increased emergence of related vulnerabilities in the future.
4. Bug collisions are high: Vulnerability exploitation is not subject to copyright, so once a vulnerability is discovered, many other attackers will swiftly exploit it, leading to multiple security personnel reporting the same vulnerability. When vulnerabilities are discovered, promptly fixed, and patched on user devices, it disrupts the actions of more potential attackers.
Google urges the industry to maintain focus on the following areas:
1. More comprehensive and timely vulnerability patching to address variant vulnerabilities and the issue of N-days being treated as 0-days.
2. Encourage more platforms to follow in the footsteps of browsers, implementing broader vulnerability mitigation measures to reduce the exploitability of an entire class of vulnerabilities.
3. Transparency and collaboration between suppliers and security maintainers should continue to grow, enabling the sharing of technical details and joint detection of vulnerability exploitation chains across multiple products.