
zLabs has uncovered AppLite, a sophisticated new variant of the AntiDot banking trojan, targeting Android devices through a wide-reaching phishing campaign. This malware, disguised as legitimate apps like Chrome, TikTok, and corporate tools, is capable of stealing sensitive credentials and taking full control of infected devices.
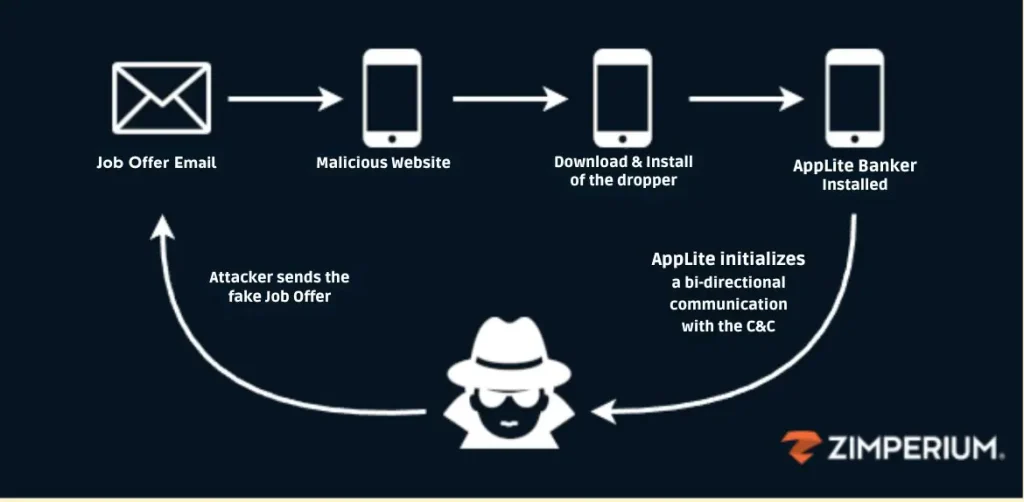
The attackers behind this campaign employed elaborate social engineering tactics to lure victims. Masquerading as HR representatives or job recruiters, they sent carefully crafted phishing emails to potential victims. These emails redirected users to phishing websites mimicking reputable companies and educational institutions, urging them to download a malicious Android app.
Once installed, this seemingly legitimate app served as a dropper, covertly delivering the AppLite banking trojan onto the victim’s device. As zLabs explained: “Victims are redirected to a malicious landing page to continue the application process or schedule an interview. The landing page manipulates victims into downloading and installing a malicious dropper application.”
AppLite uses obfuscation techniques such as ZIP manipulation to evade detection by security tools. zLabs noted: “Malicious actors often employ methods to alter the ZIP format of APK files and the structure of Android Manifest files to render analysis tools ineffective and evade detection. Parsers, if not updated, may fail to correctly process the file, allowing the malware to bypass detection mechanisms and remain installable on targeted devices.”
Similar to other banking trojans, AppLite employs overlay attacks to deceive users. When a targeted app is launched, the malware overlays a malicious HTML page that mimics the legitimate app, tricking users into entering sensitive credentials.
The malware establishes a connection with its Command and Control (C&C) server via a websocket, enabling real-time, bi-directional communication. Attackers can issue commands to collect sensitive data, such as contacts, SMS messages, and app credentials, and even take remote control of the device using Virtual Network Computing (VNC) features.
AppLite’s most alarming capability is its ability to automate the unlocking of devices. Using the Accessibility Service, it identifies the lock pattern view, calculates the movement path, and simulates touch gestures to unlock the device without user interaction.
The campaign targets users proficient in English, Spanish, French, German, Italian, Portuguese, and Russian. The primary victims are users of 95 banking apps, 62 cryptocurrency apps, and other financial services spread across regions in North America, Europe, and parts of Asia.
Related Posts:
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
- Attacker use DDoS attack to hit three major Dutch banks