Image: Juniper Threat Labs
In the ever-evolving world of cybersecurity, threats emerge in various forms, preying on vulnerabilities within systems and applications. One such threat, identified and analyzed by Juniper Threat Labs, is AndroxGh0st, a Python-based malware specifically designed to infiltrate and exploit Laravel applications.

Laravel, known for its elegant syntax and efficiency, stands tall among PHP frameworks, powering a wide array of web applications, from e-commerce platforms to social networking sites. However, its popularity also makes it a target for malicious actors. AndroxGh0st is a sophisticated Python-based malware that exploits vulnerabilities within Laravel applications, extracting sensitive information and compromising systems.
AndroxGh0st works its insidious magic in several stages:
- Scanning for Targets: The malware scans the internet for vulnerable Laravel applications, often relying on outdated versions of the framework with known weaknesses.
- Accessing .env Files: If a vulnerable app is found, AndroxGh0st looks for the
.envfile. These files often contain critical information like database logins, cloud API keys (such as AWS or Twilio), and other authentication data. - Deploying as an SMTP Cracker: It then leverages this stolen information to compromise email services and send out spam or further malicious campaigns.
Juniper Threat Labs’ technical breakdown unveils the multifaceted nature of AndroxGh0st. Armed with features like awslimitcheck, sendgridcheck, and twilio_sender, this malware is not just about data exfiltration. It showcases an unsettling proficiency in exploiting SMTP services and deploying web shells.
Among its toolkit, AndroxGh0st boasts functions capable of interrogating AWS SES accounts, extracting email-sending quotas, and assessing SendGrid API keys. The awslimitcheck function, utilizing Boto3, delves into AWS SES, revealing email limits and recent activity—a capability hinting at the malware’s brute force potential, despite its novelty.
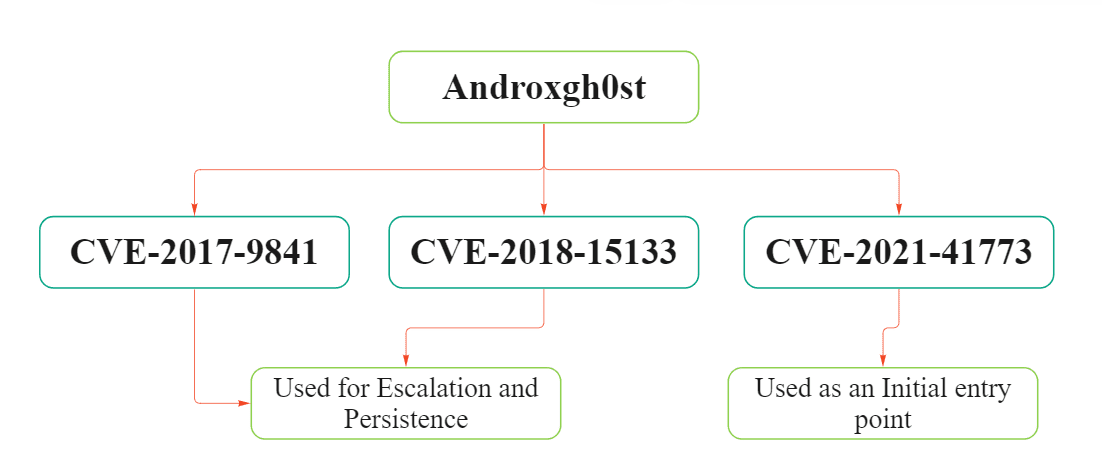
The real danger lurks in AndroxGh0st’s exploitation of vulnerabilities—CVE-2017-9841, CVE-2018-15133, and CVE-2021-41773. These vulnerabilities, associated with PHPUnit, Laravel framework, and Apache HTTP Server respectively, serve as a testament to the malware’s capability to execute code remotely and maintain persistent access.
AndroxGh0st reminds us that attackers relentlessly seek new ways to breach our defenses. It’s up to us to stay informed, and vigilant, and build applications with security in mind from the very beginning.