Source: BushidoToken
Independent security researcher BushidoToken release of a report that delves deep into the murky world of anonymous VPS services and their role in facilitating ransomware attacks. The report focuses on BitLaunch, a UK-based hosting provider, and its alleged connection to a multitude of ransomware campaigns.
BitLaunch, also known as BL Networks or BLNWX, has been active since at least 2017, offering VPS services that can be “instantly launched” and paid for with cryptocurrencies like Bitcoin, Litecoin, and Ethereum. The report highlights the ease with which cybercriminals can utilize BitLaunch’s services to quickly set up command-and-control (C2) servers, the backbone of any ransomware operation.
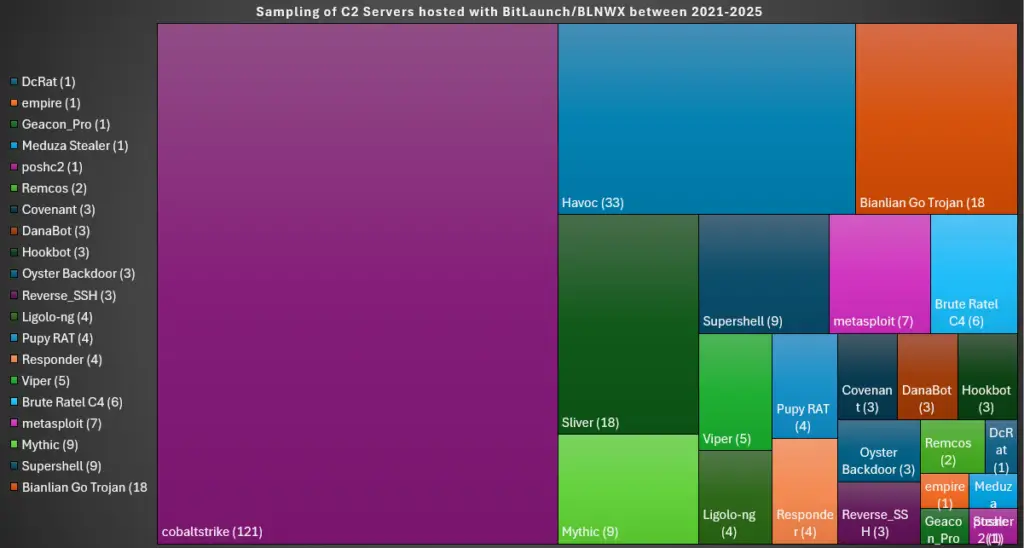
“The year-on-year growing number of CobaltStrike C2 servers hosted on BitLaunch’s services could be an indicator of tacit collusion with cybercriminals through the facilitation of cheap and quick to procurement of VPSs that end up being used to launch ransomware attacks on all sorts of victims, including hospitals, schools, governments, companies, and charities,” says BushidoToken in the report.
The report presents compelling evidence, including a breakdown of various C2 servers hosted on BitLaunch’s infrastructure. The data, collected between 2021 and 2025, shows a concerning trend: the number of C2 servers, particularly those associated with the notorious CobaltStrike framework, has been steadily increasing.
BushidoToken’s investigation also uncovered potential connections between BitLaunch and several well-known cybercriminal groups, including ShadowSyndicate, Blister Loader, PLAY ransomware, and FIN7-linked operators. These groups have been implicated in numerous high-profile ransomware attacks, causing significant financial damage and disruption to organizations worldwide.
The report raises critical questions about BitLaunch’s responsibility in preventing the misuse of its services. While the company claims to comply with takedown requests, the report argues that the ephemeral nature of C2 servers allows cybercriminals to “continually leverage BitLaunch without interference.”
BitLaunch’s commitment to anonymity and its acceptance of cryptocurrency payments have made it an attractive platform for cybercriminals seeking to operate under the radar. The report suggests that this business model, while potentially beneficial for legitimate users seeking privacy, creates a fertile ground for illicit activities.
The report concludes by urging authorities and the cybersecurity community to take action against anonymous VPS providers that inadvertently enable ransomware operations. It calls for stricter regulations, increased network observability, and greater cooperation between hosting providers and law enforcement agencies to disrupt the cybercriminal ecosystem.
Whether BitLaunch and similar providers will take proactive steps to mitigate the risks associated with their services remains to be seen.